Apache Shiro User Manual (2) Shiro Certification
Jan 18, 2017 am 09:18 AMApache Shiro User Manual (2) Shiro Authentication
Authentication is the process of verifying user identity. During the authentication process, users need to submit entity information (Principals) and credential information (Credentials) to verify whether the user is legitimate. The most common "entity/credential" combination is the "username/password" combination.
1. Shiro authentication process
1. Collect entity/credential information
//Example using most common scenario of username/password pair: UsernamePasswordToken token = new UsernamePasswordToken(username, password); //”Remember Me” built-in: token.setRememberMe(true);
UsernamePasswordToken supports the most common username/password authentication mechanisms. At the same time, since it implements the RememberMeAuthenticationToken interface, we can set the "remember me" function through the token.
However, there is a difference between "remembered" and "authenticated":
Remembered users are only non-anonymous users, and you can obtain user information through subject.getPrincipals(). But it is not a fully authenticated user. When you access functions that require authenticated users, you still need to resubmit authentication information.
You can refer to the Amazon website for this difference. The website will remember logged-in users by default. When you visit the website again, for non-sensitive page functions, the remembered user information will be displayed on the page, but when you access the website account information Still need to log in again.
2. Submit entity/credential information
Subject currentUser = SecurityUtils.getSubject(); currentUser.login(token);
After collecting the entity/credential information, we can obtain the current user through the SecurityUtils tool class, and then submit the authentication by calling the login method.
3. Authentication processing
try {
currentUser.login(token);
} catch ( UnknownAccountException uae ) { ...
} catch ( IncorrectCredentialsException ice ) { ...
} catch ( LockedAccountException lae ) { ...
} catch ( ExcessiveAttemptsException eae ) { ...
} ... catch your own ...
} catch ( AuthenticationException ae ) {
//unexpected error?
}If the login method is executed without throwing any exception information, then the user authentication is considered passed. Afterwards, calling SecurityUtils.getSubject() anywhere in the application can obtain the currently authenticated user instance. Using subject.isAuthenticated() to determine whether the user has been authenticated will return true.
On the contrary, if the login method is executed If an exception is thrown, the authentication will be considered failed. Shiro has a rich set of distinct exception classes to describe the reasons for authentication failures, such as code examples.
2. Logout operation
The logout operation can delete your login information by calling subject.logout(), such as:
currentUser.logout(); //removes all identifying information and invalidates their session too.
After the logout operation is completed, Session The information will be cleared and the subject will be treated as an anonymous user.
3. Internal processing mechanism of authentication
The above is the processing process of Shiro authentication in the application. The internal processing mechanism of Shiro authentication will be explained in detail below.
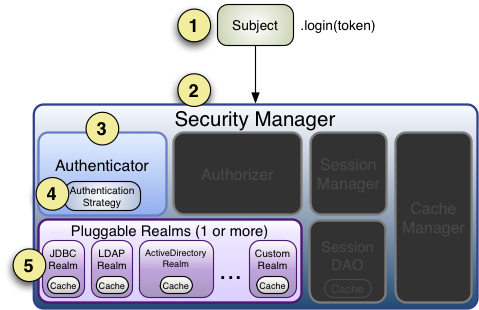
As shown above, we use the authentication part of the Shiro architecture diagram to illustrate the internal processing sequence of Shiro authentication:
1. The application constructs an end-user authentication information After the AuthenticationToken instance, call the Subject.login method.
2. The instance of Sbuject is usually an instance object of the DelegatingSubject class (or subclass). When authentication starts, the securityManager instance set by the application is entrusted to call the securityManager.login(token) method.
3. After receiving the token information, SecurityManager will entrust an instance of the built-in Authenticator (usually an instance of the ModularRealmAuthenticator class) to call authenticator.authenticate(token). ModularRealmAuthenticator will set a or Multiple Realm instances are adapted, which actually provides a pluggable authentication mechanism for Shiro.
4. If multiple Realms are configured in the application, ModularRealmAuthenticator will perform the multi-Realm authentication process according to the configured AuthenticationStrategy (authentication strategy). After Realm is called, AuthenticationStrategy will respond to each Realm result.
Note: If only one Realm is configured in the application, Realm will be called directly without configuring the authentication policy.
5. Determine whether each Realm supports the submitted token. If so, Realm will call getAuthenticationInfo(token); the getAuthenticationInfo method is the actual authentication processing. We write our custom authentication processing by overriding Realm's doGetAuthenticationInfo method.
4. Processing mechanism using multiple Realm:
1. Authenticator
The default implementation is ModularRealmAuthenticator, which supports both single Realm and multiple Realm. If only one Realm is configured, ModularRealmAuthenticator will directly call the Realm to process the authentication information. If multiple Realms are configured, it will adapt the Realm according to the authentication policy and find the appropriate Realm to execute the authentication information.
Customize Authenticator configuration:
[main] ... authenticator = com.foo.bar.CustomAuthenticator securityManager.authenticator = $authenticator
2、AuthenticationStrategy(认证策略)
当应用程序配置了多个Realm时,ModularRealmAuthenticator将根据认证策略来判断认证成功或是失败。
例如,如果只有一个Realm验证成功,而其他Realm验证失败,那么这次认证是否成功呢?如果大多数的Realm验证成功了,认证是否就认为成功呢?或者,一个Realm验证成功后,是否还需要判断其他Realm的结果?认证策略就是根据应用程序的需要对这些问题作出决断。
认证策略是一个无状态的组件,在认证过程中会经过4次的调用:
在所有Realm被调用之前
在调用Realm的getAuthenticationInfo 方法之前
在调用Realm的getAuthenticationInfo 方法之后
在所有Realm被调用之后
认证策略的另外一项工作就是聚合所有Realm的结果信息封装至一个AuthenticationInfo实例中,并将此信息返回,以此作为Subject的身份信息。
Shiro有3中认证策略的具体实现:
AtLeastOneSuccessfulStrategy 只要有一个(或更多)的Realm验证成功,那么认证将被视为成功
FirstSuccessfulStrategy 第一个Realm验证成功,整体认证将被视为成功,且后续Realm将被忽略
AllSuccessfulStrategy 所有Realm成功,认证才视为成功
ModularRealmAuthenticator 内置的认证策略默认实现是AtLeastOneSuccessfulStrategy 方式,因为这种方式也是被广泛使用的一种认证策略。当然,你也可以通过配置文件定义你需要的策略,如:
[main] ... authcStrategy = org.apache.shiro.authc.pam.FirstSuccessfulStrategy securityManager.authenticator.authenticationStrategy = $authcStrategy ...
3、Realm的顺序
由刚才提到的认证策略,可以看到Realm在ModularRealmAuthenticator 里面的顺序对认证是有影响的。
ModularRealmAuthenticator 会读取配置在SecurityManager里的Realm。当执行认证是,它会遍历Realm集合,对所有支持提交的token的Realm调用getAuthenticationInfo 。
因此,如果Realm的顺序对你使用的认证策略结果有影响,那么你应该在配置文件中明确定义Realm的顺序,如:
blahRealm = com.company.blah.Realm ... fooRealm = com.company.foo.Realm ... barRealm = com.company.another.Realm securityManager.realms = $fooRealm, $barRealm, $blahRealm
以上就是Apache Shiro 使用手册(二)Shiro 认证的内容,更多相关内容请关注PHP中文网(www.php.cn)!

Hot Article

Hot tools Tags

Hot Article

Hot Article Tags

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 PHP Framework Performance Comparison: The Ultimate Showdown of Speed vs. Efficiency
Apr 30, 2024 pm 12:27 PM
PHP Framework Performance Comparison: The Ultimate Showdown of Speed vs. Efficiency
Apr 30, 2024 pm 12:27 PM
PHP Framework Performance Comparison: The Ultimate Showdown of Speed vs. Efficiency
 The evasive module protects your website from application layer DOS attacks
Apr 30, 2024 pm 05:34 PM
The evasive module protects your website from application layer DOS attacks
Apr 30, 2024 pm 05:34 PM
The evasive module protects your website from application layer DOS attacks
 Integration and expansion of golang function concurrency control and third-party libraries
Apr 25, 2024 am 09:27 AM
Integration and expansion of golang function concurrency control and third-party libraries
Apr 25, 2024 am 09:27 AM
Integration and expansion of golang function concurrency control and third-party libraries
 How to conduct concurrency testing and debugging in Java concurrent programming?
May 09, 2024 am 09:33 AM
How to conduct concurrency testing and debugging in Java concurrent programming?
May 09, 2024 am 09:33 AM
How to conduct concurrency testing and debugging in Java concurrent programming?
 Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
Application of algorithms in the construction of 58 portrait platform
 Java package management and integration of dependencies and version control
Apr 24, 2024 pm 09:48 PM
Java package management and integration of dependencies and version control
Apr 24, 2024 pm 09:48 PM
Java package management and integration of dependencies and version control









