 Java
Java
 javaTutorial
javaTutorial
 Examples to explain the use of Java client of distributed caching software Memcached
Examples to explain the use of Java client of distributed caching software Memcached
Examples to explain the use of Java client of distributed caching software Memcached
Memcached introduction
Let’s introduce Memcached.
1. What is Memcached
Memcached is an open source, high-performance, distributed memory object cache system that accesses data in the form of key-value teams. Memcached is simple and Powerful, its simple design promotes rapid deployment, is easy to develop, and solves many problems faced by big data caching.
The official website is: http://memcached.org/. Currently, many well-known Internet applications use Memcached, such as Wikipedia, Flickr, Youtube, WordPress, etc.
2. Download MemCached under Windows platform, the address is:
http://code.jellycan.com/files/memcached-1.2.6-win32-bin.zip
The corresponding source code address is:
http://code.jellycan.com/files/memcached-1.2.6-win32-src.zip
Then, unzip it, You will see a memcached.exe file. Install it as shown below. It will be installed on the machine as a system service.
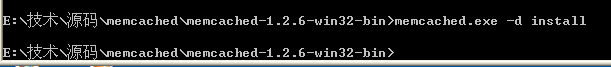
Then, select this service and right-click the mouse to start it. Serve.
Enter: telnet 127.0.0.1 11211 in the DOS interface to confirm whether the service is started correctly. If it is correct, it will be displayed as follows
The ERROR shown in the above picture is when I enter the characters casually and press The carriage return is displayed because you need to install the protocol specified by memcached for input, otherwise the error shown above will be displayed.
3. Memcached protocol and data access
The so-called protocol can be understood as the grammatical rules for its operation (data access). Common commands and parameters for accessing data are as follows:
set: save a record
key: key value of the record
flags: decimal int, identifies the client flag when storing the record, and will be returned when the record is taken out .
exptim: The expiration time of the data, 0 means no expiration, other values represent the effective number of milliseconds. After expiration, the client will not be able to obtain this record, and the expired records in memcached will be cleared or delete.
get: means to get the value corresponding to key from memcached. If there is no corresponding value, return the end flag END
append: means to add the input content to the value corresponding to key at the end
delete: delete the value corresponding to the key
For more protocols, please refer to: protocol.txt included in the memcached package
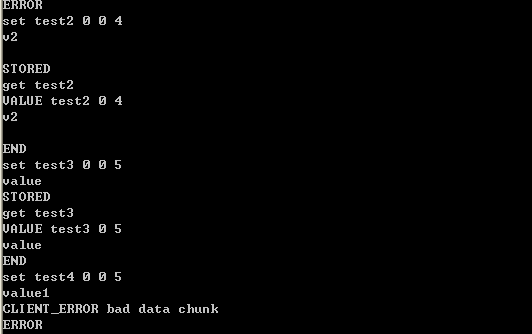
Specific examples such as:
Required Note: If the specified character length is 5 during set, and the input content exceeds this length, an error will be reported: CLIENT_ERROR bad data chunk
4, Write code to perform data access operations on memcached
Generally speaking, you can use the open source encapsulated memcached client to operate memcached. Of course, you can also write socket communication in the code according to the memcached protocol. Program implementation.
Memcached-Java-Client download page:
http://github.com/gwhalin/Memcached-Java-Client/downloads, then select download:
java_memcached -release_2.5.1.zip
You can see some written examples in the unzipped Test directory. You can check the data storage and withdrawal status by running com.danga.MemCached.test. TestMemcached, here The code is also posted:
package com.danga.MemCached.test;
import com.danga.MemCached.MemCachedClient;
import com.danga.MemCached.SockIOPool;
import org.apache.log4j.*;
public class TestMemcached {
public static void main(String[] args) {
// memcached should be running on port 11211 but NOT on 11212
BasicConfigurator.configure();
//缓存服务器地址,多台服务器则以逗号隔开,11211为memcached使用的端口号
String[] servers = { “localhost:11211″ };
//得到一个链接池对象并进行一些初始化工作
SockIOPool pool = SockIOPool.getInstance();
pool.setServers( servers );
pool.setFailover( true );
pool.setInitConn( 10 );
pool.setMinConn( 5 );
pool.setMaxConn( 250 );
//pool.setMaintSleep( 30 );
pool.setNagle( false );
pool.setSocketTO( 3000 );
pool.setAliveCheck( true );
pool.initialize();
MemCachedClient mcc = new MemCachedClient();
// turn off most memcached client logging:
//Logger.getLogger( MemCachedClient.class.getName() ).setLevel( com.schooner.MemCached.Logger. );
//以下是数据写入和取出操作例子
for ( int i = 0; i < 10; i++ ) {
boolean success = mcc.set( “” + i, “Hello!” );
String result = (String)mcc.get( “” + i );
System.out.println( String.format( “set( %d ): %s”, i, success ) );
System.out.println( String.format( “get( %d ): %s”, i, result ) );
}
System.out.println( “\n\t — sleeping –\n” );
try { Thread.sleep( 10000 ); } catch ( Exception ex ) { }
for ( int i = 0; i < 10; i++ ) {
boolean success = mcc.set( “” + i, “Hello!” );
String result = (String)mcc.get( “” + i );
System.out.println( String.format( “set( %d ): %s”, i, success ) );
System.out.println( String.format( “get( %d ): %s”, i, result ) );
}
}
}MemCached's java client example
package com.danga.MemCached.test;
import com.danga.MemCached.*;
public class TestMemcached {
public static void main(String[] args) {
/*初始化SockIOPool,管理memcached的连接池*/
String[] servers = { "192.168.105.217:11211" };
SockIOPool pool = SockIOPool.getInstance();
pool.setServers(servers);
pool.setFailover(true);
pool.setInitConn(10);
pool.setMinConn(5);
pool.setMaxConn(250);
pool.setMaintSleep(30);
pool.setNagle(false);
pool.setSocketTO(3000);
pool.setAliveCheck(true);
pool.initialize();
/*建立MemcachedClient实例*/
MemCachedClient memCachedClient = new MemCachedClient();
for (int i = 0; i < 10; i++) {
/*将对象加入到memcached缓存*/
boolean success = memCachedClient.set("" + i, "Hello!");
/*从memcached缓存中按key值取对象*/
String result = (String) memCachedClient.get("" + i);
System.out.println(String.format("set( %d ): %s", i, success));
System.out.println(String.format("get( %d ): %s", i, result));
}
}
}1. Unzip (in this case, unzip to c:\memcached).
2. In the command line state, enter: c:\memcached\memcached.exe -d install. At this point, memcached has been installed as a windows service
3. Enter: c:\memcached\memcached.exe -d start at the command line to start the memcached service. Of course, you can also choose to start it in the windows service
For more examples to explain the use of the Java client of the distributed caching software Memcached, please pay attention to the PHP Chinese website for related articles!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 How to simplify field mapping issues in system docking using MapStruct?
Apr 19, 2025 pm 06:21 PM
How to simplify field mapping issues in system docking using MapStruct?
Apr 19, 2025 pm 06:21 PM
Field mapping processing in system docking often encounters a difficult problem when performing system docking: how to effectively map the interface fields of system A...
 How to elegantly obtain entity class variable names to build database query conditions?
Apr 19, 2025 pm 11:42 PM
How to elegantly obtain entity class variable names to build database query conditions?
Apr 19, 2025 pm 11:42 PM
When using MyBatis-Plus or other ORM frameworks for database operations, it is often necessary to construct query conditions based on the attribute name of the entity class. If you manually every time...
 Is the company's security software causing the application to fail to run? How to troubleshoot and solve it?
Apr 19, 2025 pm 04:51 PM
Is the company's security software causing the application to fail to run? How to troubleshoot and solve it?
Apr 19, 2025 pm 04:51 PM
Troubleshooting and solutions to the company's security software that causes some applications to not function properly. Many companies will deploy security software in order to ensure internal network security. ...
 How to correctly divide business logic and non-business logic in hierarchical architecture in back-end development?
Apr 19, 2025 pm 07:15 PM
How to correctly divide business logic and non-business logic in hierarchical architecture in back-end development?
Apr 19, 2025 pm 07:15 PM
Discussing the hierarchical architecture problem in back-end development. In back-end development, common hierarchical architectures include controller, service and dao...
 How do I convert names to numbers to implement sorting and maintain consistency in groups?
Apr 19, 2025 pm 11:30 PM
How do I convert names to numbers to implement sorting and maintain consistency in groups?
Apr 19, 2025 pm 11:30 PM
Solutions to convert names to numbers to implement sorting In many application scenarios, users may need to sort in groups, especially in one...
 How to safely convert Java objects to arrays?
Apr 19, 2025 pm 11:33 PM
How to safely convert Java objects to arrays?
Apr 19, 2025 pm 11:33 PM
Conversion of Java Objects and Arrays: In-depth discussion of the risks and correct methods of cast type conversion Many Java beginners will encounter the conversion of an object into an array...
 In back-end development, how to distinguish the responsibilities of the service layer and the dao layer?
Apr 19, 2025 pm 01:51 PM
In back-end development, how to distinguish the responsibilities of the service layer and the dao layer?
Apr 19, 2025 pm 01:51 PM
Discussing the hierarchical architecture in back-end development. In back-end development, hierarchical architecture is a common design pattern, usually including controller, service and dao three layers...
 How to restrict access to specific interfaces of nested H5 pages through OAuth2.0's scope mechanism?
Apr 19, 2025 pm 02:30 PM
How to restrict access to specific interfaces of nested H5 pages through OAuth2.0's scope mechanism?
Apr 19, 2025 pm 02:30 PM
How to use OAuth2.0's access_token to achieve control of interface access permissions? In the application of OAuth2.0, how to ensure that the...



