Detailed explanation of permission management in mysql learning
The meaning of database permissions:
In order to ensure that the business data in the database is not illegally stolen by unauthorized users, various restrictions need to be imposed on the visitors to the database, and DatabaseSecurity There are three main types of security control measures. The first is user identity authentication, which can be password, magnetic card, fingerprint and other technologies. Only people with legal identities can enter the database. The second type of access permission control. Different roles have different access permissions to the database. The database object and permissions they access must be set for each role. The third type is to formulate a management system for database management. The system ultimately restrictspeople'sbehavior. By formulating corresponding rules and regulations, it can ensure that the data is processed by the right people at the right time. Proper operation.
mysqlThe check of user permissions is divided into two stages
1. Whether a link can be established with the mysql server
2. Whether there are certain Operation permissions (such as: select update, etc.)
1. Establish a link with the mysql server
How does the mysql server verify whether the user can establish Link
1. Verify where you come from host
2. Who are you user
3. Password password
How to link to mysql: C:\Users\PC003>mysql -h192.168.6.223 -uroot -pjalja
Parameter explanation: -h: Where to establish the link
-u: user
-p:Password
mysql> select user,host,password from user; +------+-----------+-------------------------------------------+ | user | host | password | +------+-----------+-------------------------------------------+ | root | localhost | *CFAFE434FB0E5D64538901E668E1EACD077A54DF | | root | % | *CFAFE434FB0E5D64538901E668E1EACD077A54DF | +------+-----------+-------------------------------------------+
host=localhost indicates that the default host can be used for linking (C:\Users\PC003>mysql -uroot -pjalja, C:\Users\PC003>mysql -hlocalhost -uroot -pjalja, C:\Users\PC003>mysql -h127.0.0.1 -uroot -pjalja)
host=% means that the server can be connected to the same local area network (public network) where it is located ). This method is not safe in a production environment.
host=192.168.6.224 means that the server can only establish links with the 192.168.6.224 host C:\Users\PC003>mysql -h192. 168.6.223 -uroot -pjalja
How to modify host:
mysql> update user set host='192.168.6.223' where user ='root'
mysql> flush privileges; refresh permissions (because the modified data is in memory each time the user operates Permission-related operations must be refreshed)
Change password:
mysql> update user set password=password('111111') where user='root'; mysql> flush privileges;
2. How to check permissions in mysql
mysql There is a mysql library in the library. The user table under the library checks whether the user exists, the db table checks what operating permissions the user has on which libraries, and the tables_priv table checks what operating permissions the user has on those tables.
Create user and authorize:
grant [Permission 1, Permission 2] on *.* to user@'host' identfied by 'password';
Common permissions: all, create, drop, insert, delete, update, select
For example: grant the ls user all permissions to all databases and all tables and can log in from any host in this LAN segment.
mysql> grant all on *.* to 'ls'@'192.168.6.%' identified by '111111';
Use this user to log in: C:\Users\PC003>mysql -h192.168.6.223 -uls -p111111;
View the specific permissions of the ls user:
mysql> select * from mysql.user where user='ls' \G;
*************************** 1. row ***************************
Host: 192.168.6.%
User: ls
Password: *FD571203974BA9AFE270FE62151AE967ECA5E0AA
Select_priv: Y
Insert_priv: Y
Update_priv: Y
Delete_priv: Y
Create_priv: Y
Drop_priv: Y
Reload_priv: Y
Shutdown_priv: Y
Process_priv: Y
File_priv: Y
Grant_priv: N
References_priv: Y
Index_priv: Y
Alter_priv: Y
Show_db_priv: Y
Super_priv: Y
Create_tmp_table_priv: Y
Lock_tables_priv: Y
Execute_priv: Y
Repl_slave_priv: Y
Repl_client_priv: Y
Create_view_priv: Y
Show_view_priv: Y
Create_routine_priv: Y
Alter_routine_priv: Y
Create_user_priv: Y
Event_priv: Y
Trigger_priv: Y
Create_tablespace_priv: Y
ssl_type:
ssl_cipher:
x509_issuer:
x509_subject:
max_questions: 0
max_updates: 0
max_connections: 0
max_user_connections: 0
plugin:
authentication_string: NULLPermission recovery: revoke all permissions of ls
mysql> revoke all on *.* from ls@'192.168.6.%';
Authorize someone Library permissions:
mysql> grant all on blog.* to ls@'192.168.6.%'; Grant the ls user all permissions to the blog database.
In this way, the ls user has no permissions in the user table. At this time, a db-level permission check will be performed.
mysql> select * from mysql.db where user='ls'
\G;*************************** 1. row ***************************
Host: 192.168.6.%
Db: blog
User: ls
Select_priv: Y
Insert_priv: Y
Update_priv: Y
Delete_priv: Y
Create_priv: Y
Drop_priv: Y
Grant_priv: N
References_priv: Y
Index_priv: Y
Alter_priv: Y
Create_tmp_table_priv: Y
Lock_tables_priv: Y
Create_view_priv: Y
Show_view_priv: Y
Create_routine_priv: Y
Alter_routine_priv: Y
Execute_priv: Y
Event_priv: Y
Trigger_priv: YRecover all permissions of the ls user and grant permissions to a certain table: Grant the ls user crud permissions of the user table in the blog library
mysql> revoke all on *.* from ls@'192.168.6.%'; Query OK, 0 rows affected (0.00 sec) mysql> flush privileges; Query OK, 0 rows affected (0.00 sec) mysql> grant insert,update,select,delete on blog.user to ls@'192.168.6.%'; Query OK, 0 rows affected (0.00 sec) mysql> flush privileges; Query OK, 0 rows affected (0.00 sec)
In this way, the ls user does not have permissions at the db level. At this time, the permissions check at the tables_priv level will be performed:
mysql> select * from mysql.tables_priv where user='ls'
\G;*************************** 1. row ***************************
Host: 192.168.6.%
Db: blog
User: ls
Table_name: user
Grantor: root@localhost
Timestamp: 2017-02-09 14:35:38
Table_priv: Select,Insert,Update,DeleteColumn_priv:1 row in set (0.00 sec)
mysql permission control Process:
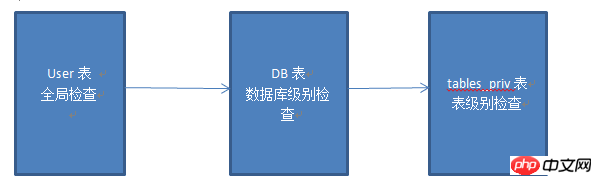
#Note: MySQL's permission check can be accurate to a certain column of data.
The above is the detailed content of Detailed explanation of permission management in mysql learning. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1384
1384
 52
52
 MySQL: Simple Concepts for Easy Learning
Apr 10, 2025 am 09:29 AM
MySQL: Simple Concepts for Easy Learning
Apr 10, 2025 am 09:29 AM
MySQL is an open source relational database management system. 1) Create database and tables: Use the CREATEDATABASE and CREATETABLE commands. 2) Basic operations: INSERT, UPDATE, DELETE and SELECT. 3) Advanced operations: JOIN, subquery and transaction processing. 4) Debugging skills: Check syntax, data type and permissions. 5) Optimization suggestions: Use indexes, avoid SELECT* and use transactions.
 How to open phpmyadmin
Apr 10, 2025 pm 10:51 PM
How to open phpmyadmin
Apr 10, 2025 pm 10:51 PM
You can open phpMyAdmin through the following steps: 1. Log in to the website control panel; 2. Find and click the phpMyAdmin icon; 3. Enter MySQL credentials; 4. Click "Login".
 MySQL: An Introduction to the World's Most Popular Database
Apr 12, 2025 am 12:18 AM
MySQL: An Introduction to the World's Most Popular Database
Apr 12, 2025 am 12:18 AM
MySQL is an open source relational database management system, mainly used to store and retrieve data quickly and reliably. Its working principle includes client requests, query resolution, execution of queries and return results. Examples of usage include creating tables, inserting and querying data, and advanced features such as JOIN operations. Common errors involve SQL syntax, data types, and permissions, and optimization suggestions include the use of indexes, optimized queries, and partitioning of tables.
 Why Use MySQL? Benefits and Advantages
Apr 12, 2025 am 12:17 AM
Why Use MySQL? Benefits and Advantages
Apr 12, 2025 am 12:17 AM
MySQL is chosen for its performance, reliability, ease of use, and community support. 1.MySQL provides efficient data storage and retrieval functions, supporting multiple data types and advanced query operations. 2. Adopt client-server architecture and multiple storage engines to support transaction and query optimization. 3. Easy to use, supports a variety of operating systems and programming languages. 4. Have strong community support and provide rich resources and solutions.
 How to use single threaded redis
Apr 10, 2025 pm 07:12 PM
How to use single threaded redis
Apr 10, 2025 pm 07:12 PM
Redis uses a single threaded architecture to provide high performance, simplicity, and consistency. It utilizes I/O multiplexing, event loops, non-blocking I/O, and shared memory to improve concurrency, but with limitations of concurrency limitations, single point of failure, and unsuitable for write-intensive workloads.
 MySQL and SQL: Essential Skills for Developers
Apr 10, 2025 am 09:30 AM
MySQL and SQL: Essential Skills for Developers
Apr 10, 2025 am 09:30 AM
MySQL and SQL are essential skills for developers. 1.MySQL is an open source relational database management system, and SQL is the standard language used to manage and operate databases. 2.MySQL supports multiple storage engines through efficient data storage and retrieval functions, and SQL completes complex data operations through simple statements. 3. Examples of usage include basic queries and advanced queries, such as filtering and sorting by condition. 4. Common errors include syntax errors and performance issues, which can be optimized by checking SQL statements and using EXPLAIN commands. 5. Performance optimization techniques include using indexes, avoiding full table scanning, optimizing JOIN operations and improving code readability.
 MySQL's Place: Databases and Programming
Apr 13, 2025 am 12:18 AM
MySQL's Place: Databases and Programming
Apr 13, 2025 am 12:18 AM
MySQL's position in databases and programming is very important. It is an open source relational database management system that is widely used in various application scenarios. 1) MySQL provides efficient data storage, organization and retrieval functions, supporting Web, mobile and enterprise-level systems. 2) It uses a client-server architecture, supports multiple storage engines and index optimization. 3) Basic usages include creating tables and inserting data, and advanced usages involve multi-table JOINs and complex queries. 4) Frequently asked questions such as SQL syntax errors and performance issues can be debugged through the EXPLAIN command and slow query log. 5) Performance optimization methods include rational use of indexes, optimized query and use of caches. Best practices include using transactions and PreparedStatemen
 How to build a SQL database
Apr 09, 2025 pm 04:24 PM
How to build a SQL database
Apr 09, 2025 pm 04:24 PM
Building an SQL database involves 10 steps: selecting DBMS; installing DBMS; creating a database; creating a table; inserting data; retrieving data; updating data; deleting data; managing users; backing up the database.




