
During HTTP communication between the server and the terminal device, packets are often captured by the network. , decompilation (Android APK decompilation tool) and other technologies to obtain the HTTP communication interface address and parameters. In order to ensure the security of the information, we use the AES+RSA combination. Method to encrypt and decrypt interface parameters.
1. Regarding the RSA encryption mechanism: the public key is used to encrypt the data, and the private key is used to decrypt the data. The public key and the private key are generated at the same time. , one-to-one correspondence. For example: A has a public key, and B has a public key and a private key. After A encrypts the data with the public key, B can decrypt it with the private key and public key.
#2. AES encryption is also called symmetric encryption: After A uses the password to AES encrypt the data, B uses the same password to AES decrypt the ciphertextKey, and the server has the public key. PublicKey and private key PrivateKey.
3. Android sends a request to the server: Android randomly generates a Byte[] random password, assuming RandomKey="123456", and uses the AES algorithm toJson data Use encryption.
4. But at this moment, the server does not know what the client's RandomKey is, so it needs to pass the Randomkey to the server at the same time, otherwise the server cannot decrypt the Json data through AES. But if the request is sent directly, The RandomKey will be exposed, so the RandomKey must be irreversibly encrypted with RSA. 5. Android will use Randomkey for AES encryption and RandomKey for RSA encryption to send the data to the server through HTTP. The request is completed. 6. The server receives the AES-encrypted Json data and the Rsa-encrypted RandomKey data. 7. The server decrypts the encrypted RandomKey using the private key. Get the original RandomKey generated by Android. 8. Use the original RandomKey to perform AES symmetric decryption of the encrypted Json data. At this point, the original Json data sent from the Android side has been obtained. Perform regular server business operations, and then encrypt the returned data with AES through RandomKey on the Android side, and then the Response is returned. 9. After the Android terminal receives the Response data, it can directly perform AES decryption using the RandomKey generated locally. You can view the detailed flow chart below.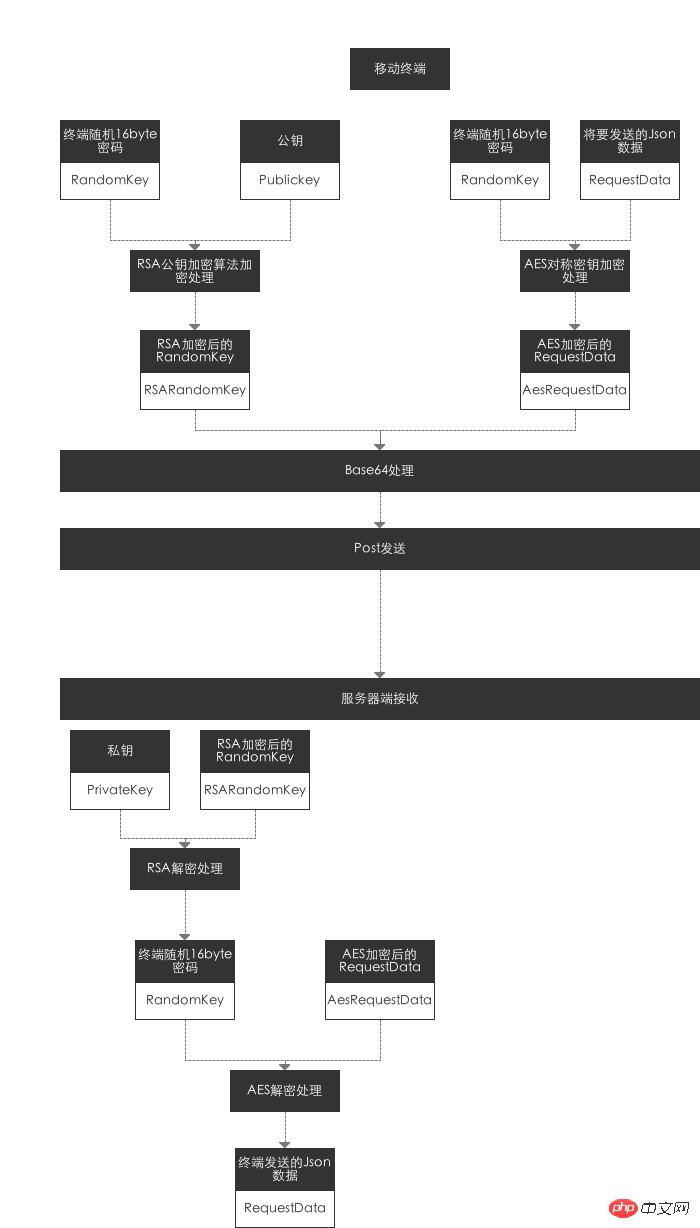
Notes:
1. During the actual development process, it was found that RSA and AES have different ciphertext generation standards and are incompatible with IOS. IOS requires a different public key in the RSA algorithm than JAVA. For detailed solutions, please see: 2. AES encryption cannot use KEYs exceeding 128Byte, because versions above jdk1.7 do not support KEYs exceeding 128Byte. Summary: From a performance perspective, the entire client from sending encrypted data to decrypting and getting the original data returned does not exceed300ms (Iphone4 and Centos Java server transmission test). This plan does not use TOKEN, but it may be used in the future. How to update the public key also needs to continue to be improved.
The above is the detailed content of AES/RSA encryption mechanism. For more information, please follow other related articles on the PHP Chinese website!




