 Backend Development
Backend Development
 Python Tutorial
Python Tutorial
 Getting started with python crawlers (3)--Using requests to build Zhihu API
Getting started with python crawlers (3)--Using requests to build Zhihu API
Getting started with python crawlers (3)--Using requests to build Zhihu API
This article mainly introduces you to the relevant information about python Getting started with crawlers and using requests to build ZhihuAPI. The article introduces it in detail through sample code, which is of great help to everyone. It has certain reference and learning value. Friends who need it can take a look below.
Preface
The use of requests is introduced in the crawler series article Elegant HTTP Library Requests. This time we use requests to build a knowledge base. The functions of the Hu API include: sending private messages, liking articles, following users, etc. Because any function involving user operations requires logging in, it is recommended to understand Python to simulate Zhihu login before reading this article. Now assume that you already know how to use requests to simulate Zhihu login.
Idea Analysis
The process of sending a private message is that the browser sends an HTTP request to the server, and the request message includes the request URL and request headerHeader, and the request body. As long as these information are clear, it is easy to use requests to simulate the browser sending private messages.
Open the Chrome browser, find a user, click to send a private message, and track the network request process of the private message.
Look at the request header information first

The request header header contains cookies login information, in addition There is also an authorization field, which is used for user authentication. At the same time, this field is also stored in cookies (in order to prevent cookie information from being leaked, I made a mosaic). This information must be carried when requests are requested.
Let’s take a look at the request URL and request body

The request URL is www.zhihu.com/api/v4/messages , the request method is POST, the request body
{"type":"common","content":"你好,我是pythoner","receiver_hash":"1da75b85900e00adb072e91c56fd9149"}The request body is a json string, the type and content are easy to understand, but I don’t know what receiver_hash is and need to be further determined, but you should guess that this is A field similar to user id.
Now the question is, how to find the user's id through the URL of the user's homepage? In order to completely simulate the entire process of private messaging, I specially registered a Zhihu account.
If you don’t have an extra mobile phone number, you can use Google to search for “receive sms online”. There are many mobile phone numbers on the Internet that provide free online reception of text messages. The homepage of my registered account: https://www.zhihu .com/people/xiaoxiaodouzi
First try to follow the trumpet account, and then find the trumpet account in the list I follow. When I move the mouse to the trumpet account's avatar, I find that there is an HTTP network request.
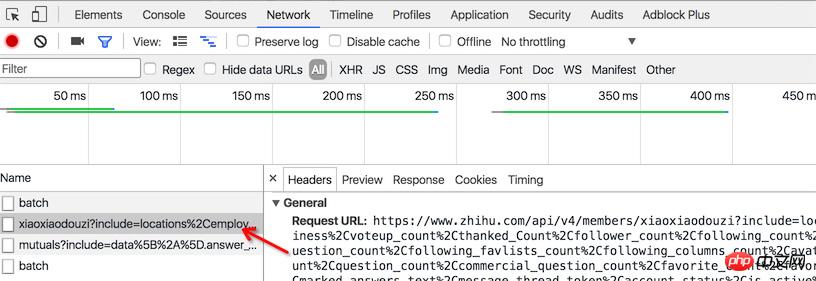
The request URL is www.zhihu.com/api/v4/members/xiaoxiaodouzi. The back part of this URL "xiaoxiaodouzi" corresponds to the back part of the Xiaoxiao homepage URL. This Part of it we call url_token.
The data returned by interface is the user’s personal public information.
{
...
"id":"1da75b85900e00adb072e91c56fd9149",
"favorite_count":0,
"voteup_count":0,
"commercial_question_count":0,
"url_token":"xiaoxiaodouzi",
"type":"people",
"avatar_url":"https://pic1.zhimg.com/v2-ca13758626bd7367febde704c66249ec_is.jpg",
"is_active":1492224390,
"name":"\u6211\u662f\u5c0f\u53f7",
"url":"http://www.zhihu.com/api/v4/people/1da75b85900e00adb072e91c56fd9149",
"gender":-1
...
}We can clearly see that there is an id field. As we guessed before, the receiver_hash field in the private message is the user's id.
Code implementation
Now we have clarified the idea of the private message function, and code implementation is a matter of course.
User information
#In order to get the receiver_hash dictionary required for the private message interface, we first need to obtain the user information, which contains the id for value.
@need_login def user(self, url_token): """ 获取用户信息, :param url_token: url_token 是用户主页url中后面部分 例如: https://www.zhihu.com/people/xiaoxiaodouzi url_token 是 xiaoxiaodouzi :return:dict """ response = self._session.get(URL.profile(url_token)) return response.json()
Send a private message
@need_login
def send_message(self, user_id, content):
"""
给指定的用户发私信
:param user_id: 用户ID
:param content: 私信内容
"""
data = {"type": "common", "content": content, "receiver_hash": user_id}
response = self._session.post(URL.message(), json=data)
data = response.json()
if data.get("error"):
self.logger.info("私信发送失败, %s" % data.get("error").get("message"))
else:
self.logger.info("发送成功")
return dataThe above two methods are placed in a class called Zhihu. I only listed the key code. The @need_login involved is a user authentication decorator, indicating that this method requires login before it can operate. If you are careful, you may notice that I did not explicitly specify the Header field in each request because I initialized it in the init.py method.
def init(self):
self._session = requests.session()
self._session.verify = False
self._session.headers = {"Host": "www.zhihu.com",
"Referer": "https://www.zhihu.com/",
'User-Agent': 'Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_5) AppleWebKit/537.36'
' (KHTML, like Gecko) Chrome/56.0.2924.87',
}
self._session.cookies = cookiejar.LWPCookieJar(filename=cookie_filename)
try:
self._session.cookies.load(ignore_discard=True)
except:
passCall execution
from zhihu import Zhihu
if name == 'main':
zhihu = Zhihu()
profile = zhihu.user("xiaoxiaodouzi")
_id = profile.get("id")
zhihu.send_message(_id, "你好,这是来自Python之禅的问候")After the execution was completed, the trumpet successfully received the private message I sent.

Finally, we can follow similar ideas to implement functions such as following users and liking them.
[Related recommendations]
1. Getting started with python crawlers (5)--regular expression example tutorial
3. Getting started with python crawlers (2)--HTTP library requests
4. Getting started with python crawlers (1) - Quickly understand the HTTP protocol
5. Share an example of using a Python crawler to simulate Zhihu login
The above is the detailed content of Getting started with python crawlers (3)--Using requests to build Zhihu API. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 Is the vscode extension malicious?
Apr 15, 2025 pm 07:57 PM
Is the vscode extension malicious?
Apr 15, 2025 pm 07:57 PM
VS Code extensions pose malicious risks, such as hiding malicious code, exploiting vulnerabilities, and masturbating as legitimate extensions. Methods to identify malicious extensions include: checking publishers, reading comments, checking code, and installing with caution. Security measures also include: security awareness, good habits, regular updates and antivirus software.
 How to run programs in terminal vscode
Apr 15, 2025 pm 06:42 PM
How to run programs in terminal vscode
Apr 15, 2025 pm 06:42 PM
In VS Code, you can run the program in the terminal through the following steps: Prepare the code and open the integrated terminal to ensure that the code directory is consistent with the terminal working directory. Select the run command according to the programming language (such as Python's python your_file_name.py) to check whether it runs successfully and resolve errors. Use the debugger to improve debugging efficiency.
 Can vs code run in Windows 8
Apr 15, 2025 pm 07:24 PM
Can vs code run in Windows 8
Apr 15, 2025 pm 07:24 PM
VS Code can run on Windows 8, but the experience may not be great. First make sure the system has been updated to the latest patch, then download the VS Code installation package that matches the system architecture and install it as prompted. After installation, be aware that some extensions may be incompatible with Windows 8 and need to look for alternative extensions or use newer Windows systems in a virtual machine. Install the necessary extensions to check whether they work properly. Although VS Code is feasible on Windows 8, it is recommended to upgrade to a newer Windows system for a better development experience and security.
 Can visual studio code be used in python
Apr 15, 2025 pm 08:18 PM
Can visual studio code be used in python
Apr 15, 2025 pm 08:18 PM
VS Code can be used to write Python and provides many features that make it an ideal tool for developing Python applications. It allows users to: install Python extensions to get functions such as code completion, syntax highlighting, and debugging. Use the debugger to track code step by step, find and fix errors. Integrate Git for version control. Use code formatting tools to maintain code consistency. Use the Linting tool to spot potential problems ahead of time.
 Choosing Between PHP and Python: A Guide
Apr 18, 2025 am 12:24 AM
Choosing Between PHP and Python: A Guide
Apr 18, 2025 am 12:24 AM
PHP is suitable for web development and rapid prototyping, and Python is suitable for data science and machine learning. 1.PHP is used for dynamic web development, with simple syntax and suitable for rapid development. 2. Python has concise syntax, is suitable for multiple fields, and has a strong library ecosystem.
 Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
VS Code is available on Mac. It has powerful extensions, Git integration, terminal and debugger, and also offers a wealth of setup options. However, for particularly large projects or highly professional development, VS Code may have performance or functional limitations.
 Can vscode run ipynb
Apr 15, 2025 pm 07:30 PM
Can vscode run ipynb
Apr 15, 2025 pm 07:30 PM
The key to running Jupyter Notebook in VS Code is to ensure that the Python environment is properly configured, understand that the code execution order is consistent with the cell order, and be aware of large files or external libraries that may affect performance. The code completion and debugging functions provided by VS Code can greatly improve coding efficiency and reduce errors.
 Golang vs. Python: Concurrency and Multithreading
Apr 17, 2025 am 12:20 AM
Golang vs. Python: Concurrency and Multithreading
Apr 17, 2025 am 12:20 AM
Golang is more suitable for high concurrency tasks, while Python has more advantages in flexibility. 1.Golang efficiently handles concurrency through goroutine and channel. 2. Python relies on threading and asyncio, which is affected by GIL, but provides multiple concurrency methods. The choice should be based on specific needs.



