10 recommended articles about php chroot() function
This article focuses on configuration records, and the benefits of chroot (jail) will not be described in detail. This article is divided into three parts: configuring basic chroot jail, configuring chroot jail for nginx, and configuring chrootjail for tomcat. 1. Configure a basic chroot jail1.1. Create a directory as the root directory of the chroot jail. # mkdir /home/chroot/jail1.2. Use the ldd command to find out the dependent libraries of the command you want to run in the chroot jail. # ldd /bin/bash linux-vdso.so.1 => (0x00007fff56fcc000) libtinfo.so.5 => /lib64/libtinfo.so.5 (0x0000003ad1200000) libdl.so.2 => /lib64/libdl.so.2 (0x0000003abe600000) libc.so.6 => /lib64/l
1. nginx and tomcat use chroot (jail) related configuration
Introduction:: This article mainly introduces the configuration related to chroot (jail) used by nginx and tomcat. Students who are interested in PHP tutorials can refer to it.
2. php download system PHP security configuration method explained in Wood Wing Download System
Introduction: php download System: PHP download system PHP security configuration method explained in Muyi download system: 1. Web server security PHP is actually just a module function of the Web server, so the security of the Web server must be ensured first. Of course, in order for a web server to be secure, it must first ensure system security, which is a long way off. PHP can be combined with various web servers, and only Apache will be discussed here. It is highly recommended to install and start Apache in chroot mode. In this way, even if there are vulnerabilities in Apache, PHP and their scripts, only the restricted system will be affected and will not harm the actual system. But using chroot Apac
3. http://www.kaqima.com/index.ht PHP security configuration
Introduction: http://www.kaqima.com/index.ht: http://www.kaqima.com/index.ht PHP security configuration: PHP security configuration 1. Web server security PHP is actually just a Web server A module function, so the security of the web server must be ensured first. Of course, in order for a web server to be secure, it must first ensure system security, which is a long way off. PHP can be combined with various web servers, and only Apache will be discussed here. It is highly recommended to install and start Apache in chroot mode, so that even if there are vulnerabilities in Apache, PHP and their scripts, only this will be affected
Introduction: PHP-FPM Chroot execution environment detailed explanation, php-fpmchroot detailed explanation. Detailed explanation of PHP-FPM's Chroot execution environment. Detailed explanation of php-fpmchroot. Setting up chroot in PHP-FPM has a good isolation effect and improves system security. However, if you want to establish a reasonable PHP-FPM Chr
5. Learn the security protection knowledge of Apache server with examples
Introduction: PHP tutorial
6. Establish the Chroot execution environment of PHP-FPM
Introduction: Establish the Chroot execution environment of PHP-FPM
Introduction: PHP Security Configuration 1. Web server security PHP is actually just a module function of the web server, so the security of the web server must be ensured first. Of course, in order for a web server to be secure, it must first ensure system security, which is a long way off. PHP can be combined with various web servers, and only Apache will be discussed here. It is highly recommended to install and start Apache in chroot mode, so that even if there are vulnerabilities in Apache, PHP and their scripts, those affected will be
8. PHP urgently needed disabled functions
Introduction: PHP functions that need to be disabled disable_functions =gzinflate,passthru,exec,system,chroot,scandir,chgrp,chown,shell_exec,proc_open,proc_get_status,ini_alter,ini_alter,ini_restore,dl,pfsockopen,ope
##9. php urgently needs disabled functions
Introduction: PHP functions that need to be disabled disable_functions =gzinflate, passthru, exec, system, chroot, scandir, chgrp, chown, shell_exec, proc_open, proc_get_status, ini_alter, ini_alter, ini_restore, dl, pfsockopen, ope
10. PHP insurance configuration
Introduction: PHP security configuration 1. Web server security PHP is actually just a web server A module function, so the security of the web server must be ensured first. Of course, in order for a web server to be secure, it must first ensure system security, which is a long way off. PHP can be combined with various web servers, and only Apache will be discussed here. It is highly recommended to install and start Apache in chroot mode, so that even if there are vulnerabilities in Apache, PHP and their scripts, only
[Related Q&A recommendations]:
java - The zookeeper client namespace (Chroot) does not take effect, how to solve it?
linux - There is no information in Grub's configuration file
linux - vsftpd: refusing to run with writable root inside chroot()
java-ee - Calling AudioSystem.getMixerInfo() in Java under Linux (gentoo) returns nothing
linux - Building a cluster under CentOS
The above is the detailed content of 10 recommended articles about php chroot() function. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1375
1375
 52
52
 PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 brings several new features, security improvements, and performance improvements with healthy amounts of feature deprecations and removals. This guide explains how to install PHP 8.4 or upgrade to PHP 8.4 on Ubuntu, Debian, or their derivati
 CakePHP Working with Database
Sep 10, 2024 pm 05:25 PM
CakePHP Working with Database
Sep 10, 2024 pm 05:25 PM
Working with database in CakePHP is very easy. We will understand the CRUD (Create, Read, Update, Delete) operations in this chapter.
 CakePHP Date and Time
Sep 10, 2024 pm 05:27 PM
CakePHP Date and Time
Sep 10, 2024 pm 05:27 PM
To work with date and time in cakephp4, we are going to make use of the available FrozenTime class.
 CakePHP File upload
Sep 10, 2024 pm 05:27 PM
CakePHP File upload
Sep 10, 2024 pm 05:27 PM
To work on file upload we are going to use the form helper. Here, is an example for file upload.
 CakePHP Routing
Sep 10, 2024 pm 05:25 PM
CakePHP Routing
Sep 10, 2024 pm 05:25 PM
In this chapter, we are going to learn the following topics related to routing ?
 Discuss CakePHP
Sep 10, 2024 pm 05:28 PM
Discuss CakePHP
Sep 10, 2024 pm 05:28 PM
CakePHP is an open-source framework for PHP. It is intended to make developing, deploying and maintaining applications much easier. CakePHP is based on a MVC-like architecture that is both powerful and easy to grasp. Models, Views, and Controllers gu
 CakePHP Creating Validators
Sep 10, 2024 pm 05:26 PM
CakePHP Creating Validators
Sep 10, 2024 pm 05:26 PM
Validator can be created by adding the following two lines in the controller.
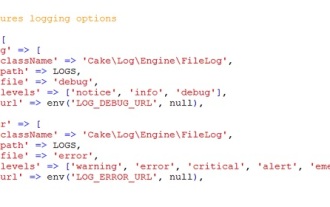 CakePHP Logging
Sep 10, 2024 pm 05:26 PM
CakePHP Logging
Sep 10, 2024 pm 05:26 PM
Logging in CakePHP is a very easy task. You just have to use one function. You can log errors, exceptions, user activities, action taken by users, for any background process like cronjob. Logging data in CakePHP is easy. The log() function is provide




