
In general development, I often see that many students only use some basic methods in dealing with the Java concurrent development model. For example, Volatile, synchronized. Advanced concurrency packages like Lock and atomic are not often used by many people. I think most of the reasons are caused by the lack of attributes of the principle. In busy development work, who can accurately grasp and use the correct concurrency model? So based on this idea recently, I plan to organize this part of the concurrency control mechanism into an article. It is not only a memory of the knowledge I have mastered, but also I hope that the content mentioned in this article can help most developers. Parallel program development inevitably involves issues such as multi-threading, multi-task collaboration and data sharing. In the JDK, multiple ways are provided to achieve concurrency control between multiple threads. For example, commonly used ones: internal locks, reentrant locks, read-write locks and semaphores. Java memory model In Java, each thread has a working memory area, which stores a copy of the value of the variable in the main memory shared by all threads. When a thread executes, it operates on these variables in its own working memory. In order to access a shared variable, a thread usually first
1. Java concurrency control mechanism detailed explanation

Introduction: In general development, I often see that many students only use some basic methods in dealing with the Java concurrent development model. For example, Volatile, synchronized. Advanced concurrency packages like Lock and atomic are not often used by many people. I think most of the reasons are caused by the lack of attributes of the principle. In the busy development work, who can accurately grasp and use the correct concurrency model
2. Use PHP's OOP features to achieve data protection (1)

Introduction: In PHP 4, var is usually used to declare variables, but in PHP 5, you can use The feature of object-oriented programming (OOP) comes from customizing the visibility of data - that is, accessibility. Visibility here is very similar to variable scope, but provides a better control mechanism. There are the following three types of visibility modifications Symbol:
3. PHP object-oriented access type control
Introduction: public, protected, private A modifier is an access control mechanism introduced in PHP5. By using modifiers, developers can restrict access to members in a class. Literally, these three modifiers are translated into Chinese as public, protected, and private. Let's use code examples to see how public, protected, and private restrict members in a class. Public
4. High-speed development of php applications with cakephp - user and permission control
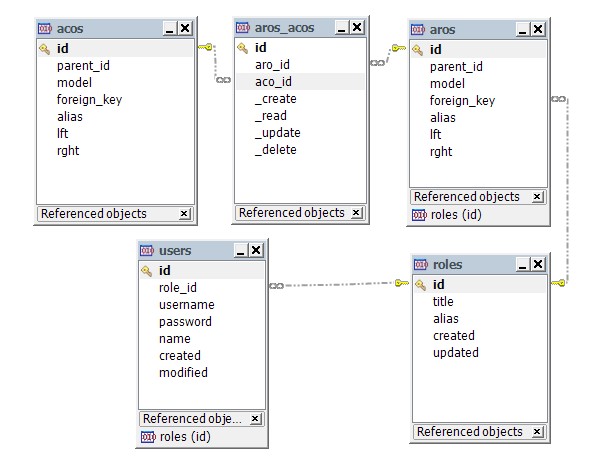
##Introduction: Use cakephp to quickly develop php applications - user and permission control The cakephp framework provides a set of Acl-based access control mechanisms. By using the AuthComponent and AclComponent components, you can quickly implement permission control. ? Permission design based on access control list As can be seen from the ER diagram above, the business object of the aro object is role (role, which is the same concept as group). In the database data, there is no control of
##5.High-speed development of php applications with cakephp - user and permission control
 ##Introduction: Use cakephp to quickly develop php applications - user and permission control The cakephp framework provides a set of Acl-based access control mechanisms. By using the AuthComponent and AclComponent components, you can quickly implement permission control. ?Permission design based on access control list As can be seen from the ER diagram above, the business object of the aro object is role (role and group are the same concept). In the database data, there is no aco operation
##Introduction: Use cakephp to quickly develop php applications - user and permission control The cakephp framework provides a set of Acl-based access control mechanisms. By using the AuthComponent and AclComponent components, you can quickly implement permission control. ?Permission design based on access control list As can be seen from the ER diagram above, the business object of the aro object is role (role and group are the same concept). In the database data, there is no aco operation
##6. Summary of the basic concepts of transactions and locks in sqlserver
Introduction: .1 Basic concepts Concurrency control: Mainly considering the situation where multiple users access the same data in the database at the same time. SQL Server is designed with two concurrent access control mechanisms: locks and row version control. Lock: Mainly used to ensure database integrity and consistency in a multi-user environment. Each transaction will request different types of locks for the resources it depends on, which can prevent it 7. Account scheme system role takes a multi-pronged approach to ensure the security of Oracle Introduction: Account is a name defined in the database system, which is the basic access control mechanism of the database. When connecting to an Oracle database, like other databases, user 8 is required. Oracle Database Writing Effective Transaction Guidelines Introduction: In the Oracle database, a control mechanism called "transaction" is provided. Through things, effective and safe modification operations on data can be completed, making the database Introduction: MySQL Lab 1.? Concurrency and isolation control mechanism in MySQL Meta-data metadata lock: implemented in the table cache cache , providing isolation operations for DDL (Data Definition Language). A special meta-data metadata type called Name Lock. (SQL layer) Table-level data lock (SQL layer) Storage engine-specific mechanism ro 10. Redis source code learning-AOF Introduction: Preface There are many articles on the Internet that introduce the AOF mechanism of redis, but they introduce the AOF process from a macro perspective and there is no specific analysis. The data structures and control mechanisms involved in the AOF process. I especially looked at the 2.8 source code last night, and I feel that many details in the source code are worthy of careful study. Especially the list *aof_rewrite_buf_blocks structure. If you look at the source code carefully, you will find [Related Q&A recommendations]: How does the security control mechanism of MySQL database work? 


The above is the detailed content of 10 recommended courses on control mechanisms. For more information, please follow other related articles on the PHP Chinese website!




