 Java
Java
 javaTutorial
javaTutorial
 Spring+SpringMVC+MyBatis in-depth learning and construction (17) - SpringMVC interceptor
Spring+SpringMVC+MyBatis in-depth learning and construction (17) - SpringMVC interceptor
Spring+SpringMVC+MyBatis in-depth learning and construction (17) - SpringMVC interceptor
Please indicate the source:
As mentioned earlier: Spring+SpringMVC+MyBatis in-depth learning and construction (16) - SpringMVC annotation development (advanced)
1.Interceptor definition
Spring Web MVC's processor interceptor is similar to the filter Filter in Servlet development, which is used to pre-process and post-process the processor.
Define the interceptor and implement the HandlerInterceptor interface. Three methods are provided in the interface.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 |
|
2.Interceptor configuration
There is a large interceptor chain in struts. It is a common thing. You can add it to any action link and let it intercept. But spring's interceptor is not global.
2.1 Configure an interceptor for a certain mapping
The springmvc interceptor performs interception settings for HandlerMapping. If interception is set in a HandlerMapping, the handler that is successfully mapped by the HandlerMapping will eventually use the interceptor.
1 2 3 4 5 6 7 8 9 10 11 |
|
Generally not recommended.
2.2 Configure global interceptors for all mappings
springmvc can configure similar global interceptors, and the springmvc framework injects the configured global-like interceptors into each HandlerMapping.
1 2 3 4 5 6 7 8 9 10 11 12 13 |
|
3.Interception test
3.1 Testing requirements
Test the execution timing of each method of multiple interceptors.
3.2Write two interceptors
3.3 Both interceptors are allowed
Run log information:
1 2 3 4 5 6 7 8 |
|
Summarize:
The preHandle method is executed in order, and postHandle and afterCompletion are executed in the reverse order of the interceptor configuration.
3.4 Interceptor 1 is allowed, Interceptor 2 is not allowed
Run log information:
1 2 3 |
|
Summarize:
Interceptor 1 is released, and the preHandle of interceptor 2 will be executed.
The preHandle of interceptor 2 will not be released, and the postHandle and afterCompletion of interceptor 2 will not be executed.
As long as there is an interceptor that does not release, postHandle will not be executed.
3.5 Interceptor 1 is not allowed, Interceptor 2 is not allowed
Run log information:
1 |
|
The preHandle of interceptor 1 is not released, and postHandle and afterCompletion will not be executed.
The preHandle of interceptor 1 is not released, and interceptor 2 is not executed.
4. Summary
Apply the interceptor based on the test results.
For example: Unified log processing interceptor, if the interceptor preHandle needs to be changed, it must be released and placed at the first position in the interceptor chain.
For example: login authentication interceptor, placed at the first position in the interceptor chain. The permission verification interceptor is placed after the login interceptor. (Because the permissions are verified after the login is passed)
5.Interceptor application (implementing login authentication)
5.1 Requirements
(1) User request url
(2) Interceptor performs interception verification
If the requested URL is a public address (a URL that can be accessed without logging in), let it pass
If the user session does not exist, jump to the login page.
If the user session exists, release it and continue the operation.
5.2 Login and exit controller methods
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 |
|
5.3 Login authentication interception implementation
5.3.1LoginInterceptor
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 |
|
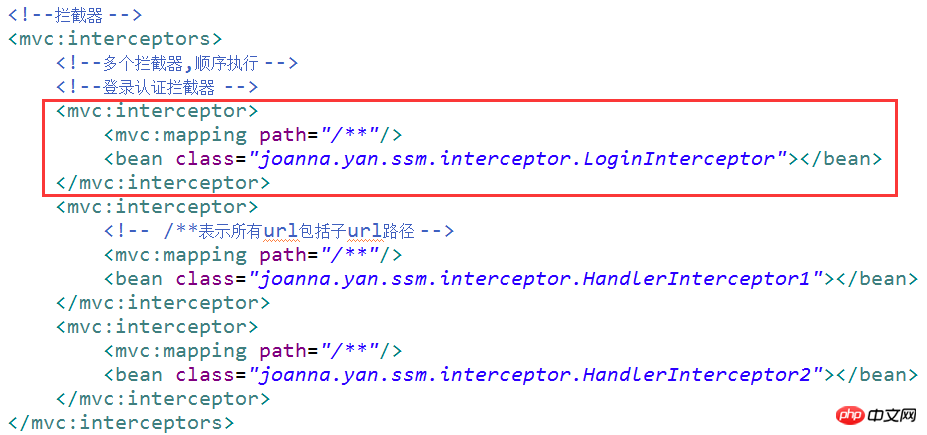
5.3.2 Interceptor configuration
Configuration in springmvc.xml under classpath:
If this article is helpful to you, please tip me on WeChat~
The above is the detailed content of Spring+SpringMVC+MyBatis in-depth learning and construction (17) - SpringMVC interceptor. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1423
1423
 52
52
 1317
1317
 25
25
 1268
1268
 29
29
 1247
1247
 24
24
 How to quickly build a statistical chart system under the Vue framework
Aug 21, 2023 pm 05:48 PM
How to quickly build a statistical chart system under the Vue framework
Aug 21, 2023 pm 05:48 PM
How to quickly build a statistical chart system under the Vue framework. In modern web applications, statistical charts are an essential component. As a popular front-end framework, Vue.js provides many convenient tools and components that can help us quickly build a statistical chart system. This article will introduce how to use the Vue framework and some plug-ins to build a simple statistical chart system. First, we need to prepare a Vue.js development environment, including installing Vue scaffolding and some related plug-ins. Execute the following command in the command line
 Can buildings be built in the wild in Mistlock Kingdom?
Mar 07, 2024 pm 08:28 PM
Can buildings be built in the wild in Mistlock Kingdom?
Mar 07, 2024 pm 08:28 PM
Players can collect different materials to build buildings when playing in the Mistlock Kingdom. Many players want to know whether to build buildings in the wild. Buildings cannot be built in the wild in the Mistlock Kingdom. They must be within the scope of the altar. . Can buildings be built in the wild in Mistlock Kingdom? Answer: No. 1. Buildings cannot be built in the wild areas of the Mist Lock Kingdom. 2. The building must be built within the scope of the altar. 3. Players can place the Spirit Fire Altar by themselves, but once they leave the range, they will not be able to construct buildings. 4. We can also directly dig a hole in the mountain as our home, so we don’t need to consume building materials. 5. There is a comfort mechanism in the buildings built by players themselves, that is to say, the better the interior, the higher the comfort. 6. High comfort will bring attribute bonuses to players, such as
 Best practices and precautions for building a web server under CentOS 7
Aug 25, 2023 pm 11:33 PM
Best practices and precautions for building a web server under CentOS 7
Aug 25, 2023 pm 11:33 PM
Best practices and precautions for building web servers under CentOS7 Introduction: In today's Internet era, web servers are one of the core components for building and hosting websites. CentOS7 is a powerful Linux distribution widely used in server environments. This article will explore the best practices and considerations for building a web server on CentOS7, and provide some code examples to help you better understand. 1. Install Apache HTTP server Apache is the most widely used w
 Quickly install PyTorch in PyCharm: an easy guide
Feb 24, 2024 pm 09:54 PM
Quickly install PyTorch in PyCharm: an easy guide
Feb 24, 2024 pm 09:54 PM
PyTorch Installation Guide: Quickly set up a development environment in PyCharm PyTorch is one of the most popular frameworks in the current field of deep learning. It has the characteristics of ease of use and flexibility, and is favored by developers. This article will introduce how to quickly set up the PyTorch development environment in PyCharm, so that you can start the development of deep learning projects. Step 1: Install PyTorch First, we need to install PyTorch. The installation of PyTorch usually needs to take into account the system environment
 What's the best way to set up a Douyin account? What is the five-piece account creation kit?
Apr 02, 2024 am 09:52 AM
What's the best way to set up a Douyin account? What is the five-piece account creation kit?
Apr 02, 2024 am 09:52 AM
With the rapid development of mobile Internet, the short video application Douyin has become an indispensable part of people's daily lives. Having a popular Douyin account can not only attract the attention of fans, but also bring commercial value. So, how to set up the best Douyin account? 1. What is the best way to set up a Douyin account? 1. Clear positioning When creating a Douyin account, you must first clarify your positioning. Do you want to be a funny joker or a professional knowledge sharer? Clear positioning can help attract precise fans, thereby increasing the value of your account. 2. Account naming: A good account name can make fans remember you at a glance. The account name should be concise and clear, related to your positioning, and have a certain degree of creativity. Avoid using names that are too common to avoid confusion with others
 How to build an account matrix? What are the functions of matrix construction?
Mar 23, 2024 pm 06:46 PM
How to build an account matrix? What are the functions of matrix construction?
Mar 23, 2024 pm 06:46 PM
In today's information-rich era, social media platforms have become the main way for people to obtain and share information. For individuals and enterprises, establishing an effective account network to achieve maximum dissemination of information and enhance influence has become an urgent challenge that needs to be solved. 1. How to build an account matrix? 1. Clarify the target audience. Before building an account matrix, the key is to clearly define the target audience and gain an in-depth understanding of their needs, interests, and consumption habits, so that a more targeted content strategy can be developed. 2. Choose the appropriate platform. According to the characteristics of the target group, choose the appropriate social media platform for layout. Currently, the mainstream social media platforms include Weibo, WeChat, Douyin, Kuaishou, etc. Each platform has its own unique user groups and communication characteristics, and the selection needs to be based on the actual situation.
 Network security reinforcement techniques for building web servers under CentOS 7
Aug 05, 2023 pm 01:12 PM
Network security reinforcement techniques for building web servers under CentOS 7
Aug 05, 2023 pm 01:12 PM
Network security reinforcement techniques for building web servers under CentOS7 The web server is an important part of the modern Internet, so it is very important to protect the security of the web server. By hardening network security, you can reduce risks and avoid potential attacks. This article will introduce network security reinforcement techniques commonly used when building web servers on CentOS7, and provide corresponding code examples. Update your system and software First, make sure your system and software are up to date. You can use the following command to update
 How to build a simple file management system using Node.js
Nov 08, 2023 pm 06:19 PM
How to build a simple file management system using Node.js
Nov 08, 2023 pm 06:19 PM
Node.js is a very popular server-side running environment. It is written in JavaScript and allows developers to use the same programming language for front-end and back-end development. The efficiency and flexibility of Node.js make it an important part of web development. In this article, we will learn how to use Node.js to build a simple file management system. In order to achieve this function, we need to use the basic modules fs (filesystem) and h of Node.js



