 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Newbies should develop some good security habits in PHP: turning off error prompts and strict data verification, etc.
Newbies should develop some good security habits in PHP: turning off error prompts and strict data verification, etc.
Newbies should develop some good security habits in PHP: turning off error prompts and strict data verification, etc.
When you use PHP for web development, you need to pay attention to some security configuration items and turn off certain functions to prevent users from inadvertently causing various problems.
1. Turn off the php error prompt function
Change display_errors to OFF in php.ini, or add # before the php file ##error_reporting(0).
Use error_reporting(0); Failure example:<?php error_reporting(0); echo 555 echo 444; ?>
Put magic_quotes_gpc = OFF in php.ini
Avoid and
addslashesWait for repeated escaping
<?php //$bloger = $_GET['bloger'] //因为register_globals = ON 所以这步不用了直接可以用$bloger echo $bloger; ?>
configure file permissions.
Assign permissions to the corresponding folders. For example, files containing uploaded images cannot have execution permissions and can only be read3. Strict data verification, what we need to do is to strictly verify the control data Flow, even if one of the 100 million users is a bad user, it is enough to be fatal. Besides, good users sometimes become "bad" inadvertently when they accidentally enter Chinese in the data input box. In order to ensure the security and robustness of the program, data verification should include(1) Whether key data exists. For example, whether the deleted data id exists(2)
The data typeis correct. For example, whether the deleted data id is an integer(3) Data length. If the field is of char(10) type, strlen must be used to determine the data length
(4) Whether the data has dangerous characters
The above is the detailed content of Newbies should develop some good security habits in PHP: turning off error prompts and strict data verification, etc.. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 brings several new features, security improvements, and performance improvements with healthy amounts of feature deprecations and removals. This guide explains how to install PHP 8.4 or upgrade to PHP 8.4 on Ubuntu, Debian, or their derivati
 CakePHP Date and Time
Sep 10, 2024 pm 05:27 PM
CakePHP Date and Time
Sep 10, 2024 pm 05:27 PM
To work with date and time in cakephp4, we are going to make use of the available FrozenTime class.
 Discuss CakePHP
Sep 10, 2024 pm 05:28 PM
Discuss CakePHP
Sep 10, 2024 pm 05:28 PM
CakePHP is an open-source framework for PHP. It is intended to make developing, deploying and maintaining applications much easier. CakePHP is based on a MVC-like architecture that is both powerful and easy to grasp. Models, Views, and Controllers gu
 CakePHP File upload
Sep 10, 2024 pm 05:27 PM
CakePHP File upload
Sep 10, 2024 pm 05:27 PM
To work on file upload we are going to use the form helper. Here, is an example for file upload.
 CakePHP Creating Validators
Sep 10, 2024 pm 05:26 PM
CakePHP Creating Validators
Sep 10, 2024 pm 05:26 PM
Validator can be created by adding the following two lines in the controller.
 How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
Visual Studio Code, also known as VS Code, is a free source code editor — or integrated development environment (IDE) — available for all major operating systems. With a large collection of extensions for many programming languages, VS Code can be c
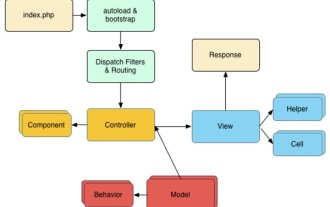 CakePHP Quick Guide
Sep 10, 2024 pm 05:27 PM
CakePHP Quick Guide
Sep 10, 2024 pm 05:27 PM
CakePHP is an open source MVC framework. It makes developing, deploying and maintaining applications much easier. CakePHP has a number of libraries to reduce the overload of most common tasks.
 How do you parse and process HTML/XML in PHP?
Feb 07, 2025 am 11:57 AM
How do you parse and process HTML/XML in PHP?
Feb 07, 2025 am 11:57 AM
This tutorial demonstrates how to efficiently process XML documents using PHP. XML (eXtensible Markup Language) is a versatile text-based markup language designed for both human readability and machine parsing. It's commonly used for data storage an



