How to store user passwords securely
1: Basic knowledge: Hashing with Salt
We already know how easy it is for malicious attackers to use lookup tables and rainbow tables to crack ordinary hash encryption. quick. We have also
learned that using randomly salted hashes can solve this problem. But what kind of salt do we use, and how do we
mix it into a password?
The salt value should be generated using a cryptographically secure pseudo-random number generator (Cryptographically Secure Pseudo-Random
Number Generator, CSPRNG). CSPRNG is very different from ordinary pseudo-random number generators, such as the rand() function of the "C" language. As the name suggests, CSPRNG is designed to be cryptographically secure, meaning it provides highly random, completely unpredictable random numbers. We don't want the salt value to be predictable, so CSPRNG must be used.
The following table lists some CSPRNG methods of current mainstream programming platforms.
Platform| Java | |
| ##Dot NET (C#, VB) | System.Security.Cryptography.RNGCryptoServiceProvider |
| Ruby | SecureRandom |
| Python | os.urandom |
| Perl | Math::Random::Secure |
| C/C++ (Windows API) | CryptGenRandom |
| Any language on GNU/Linux or Unix | Read from /dev/random or /dev/urandom |
|
A unique salt value must be used for each password of each user. Each time a user creates an account or changes their password, the password should have a new random salt value. |
Use CSPRNG to generate a random salt value long enough.
Mix the salt into the password and encrypt it using a standard password hashing function, such as Argon2, bcrypt, scrypt, or PBKDF2.- Store the salt value and the corresponding hash value together in the user database.
- Steps to verify password:
Retrieve the user’s salt value from the database and the corresponding hash value.
Mix the salt value into the password entered by the user and encrypt it using a common hash function.- Compare the result of the previous step to see if it is the same as the hash value stored in the database. If they are the same, the password is correct; otherwise, the password is wrong.
The above is the detailed content of How to store user passwords securely. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
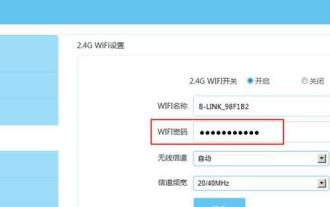 How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
Wireless networks have become an indispensable part of people's lives in today's digital world. Protecting the security of personal wireless networks is particularly important, however. Setting a strong password is key to ensuring that your WiFi network cannot be hacked by others. To ensure your network security, this article will introduce in detail how to use your mobile phone to change the router WiFi password. 1. Open the router management page - Open the router management page in the mobile browser and enter the router's default IP address. 2. Enter the administrator username and password - To gain access, enter the correct administrator username and password in the login page. 3. Navigate to the wireless settings page - find and click to enter the wireless settings page, in the router management page. 4. Find the current Wi
 Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Wireless networks have become an indispensable part of our lives with the rapid development of the Internet. In order to protect personal information and network security, it is very important to change your wifi password regularly, however. To help you better protect your home network security, this article will introduce you to a detailed tutorial on how to use your mobile phone to change your WiFi password. 1. Understand the importance of WiFi passwords. WiFi passwords are the first line of defense to protect personal information and network security. In the Internet age, understanding its importance can better understand why passwords need to be changed regularly. 2. Confirm that the phone is connected to wifi. First, make sure that the phone is connected to the wifi network whose password you want to change before changing the wifi password. 3. Open the phone’s settings menu and enter the phone’s settings menu.
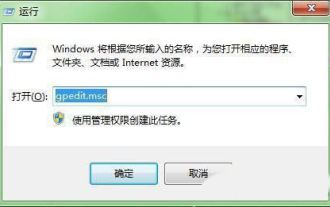 What should I do if my Win10 password does not meet the password policy requirements? What to do if my computer password does not meet the policy requirements?
Jun 25, 2024 pm 04:59 PM
What should I do if my Win10 password does not meet the password policy requirements? What to do if my computer password does not meet the policy requirements?
Jun 25, 2024 pm 04:59 PM
In the Windows 10 system, the password policy is a set of security rules to ensure that the passwords set by users meet certain strength and complexity requirements. If the system prompts that your password does not meet the password policy requirements, it usually means that your password does not meet the requirements set by Microsoft. standards for complexity, length, or character types, so how can this be avoided? Users can directly find the password policy under the local computer policy to perform operations. Let’s take a look below. Solutions that do not comply with password policy specifications: Change the password length: According to the password policy requirements, we can try to increase the length of the password, such as changing the original 6-digit password to 8-digit or longer. Add special characters: Password policies often require special characters such as @, #, $, etc. I
 How to easily get the WiFi password of a connected mobile phone (quickly find the WiFi password saved in the mobile phone)
May 08, 2024 pm 01:10 PM
How to easily get the WiFi password of a connected mobile phone (quickly find the WiFi password saved in the mobile phone)
May 08, 2024 pm 01:10 PM
Our mobile phones have become an integral part of our lives in modern society. Wireless network connections have also become an indispensable tool in our daily lives. However, sometimes we face such a situation: we want to connect to other devices but are unable to do so, we connect to WiFi but forget the password. How to easily get the WiFi password of a connected mobile phone? Find the saved WiFi password on the phone 1. Find the "WiFi" option in the settings, find and click it, and enter the phone's settings interface "WiFi" to enter the WiFi settings page, option. 2. Open the connected WiFi network details, find the name of the connected WiFi network, click to enter the detailed information page of the network, in the WiFi settings page. 3.
 How to reset WiFi password through router (simple steps to help you protect your home network security)
May 03, 2024 pm 03:01 PM
How to reset WiFi password through router (simple steps to help you protect your home network security)
May 03, 2024 pm 03:01 PM
Wireless networks have become an integral part of our lives in modern society. Securing your home WiFi network is also becoming increasingly important, however. Resetting your WiFi password is a critical task to ensure network security. To protect your home network security, this article will introduce you how to reset your WiFi password through your router. Understand the router login interface. Connect to the router and open the management page. Enter the administrator username and password. Enter the wireless settings option. Find the current WiFi name and password. Back up the network settings. Select the modify password option. Enter the new WiFi password. Set a strong password. Save the settings and exit. Reconnect the device to Test the new WiFi network to see if the connection is successful. Configure other security settings. Change the WiFi password regularly to learn the route.
 How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
Java framework design enables security by balancing security needs with business needs: identifying key business needs and prioritizing relevant security requirements. Develop flexible security strategies, respond to threats in layers, and make regular adjustments. Consider architectural flexibility, support business evolution, and abstract security functions. Prioritize efficiency and availability, optimize security measures, and improve visibility.
 PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
PHP Microframework: Security Discussion of Slim and Phalcon
Jun 04, 2024 am 09:28 AM
In the security comparison between Slim and Phalcon in PHP micro-frameworks, Phalcon has built-in security features such as CSRF and XSS protection, form validation, etc., while Slim lacks out-of-the-box security features and requires manual implementation of security measures. For security-critical applications, Phalcon offers more comprehensive protection and is the better choice.
 Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
When implementing machine learning algorithms in C++, security considerations are critical, including data privacy, model tampering, and input validation. Best practices include adopting secure libraries, minimizing permissions, using sandboxes, and continuous monitoring. The practical case demonstrates the use of the Botan library to encrypt and decrypt the CNN model to ensure safe training and prediction.




