What is the HTTP vs HTTPS handshake
Today I summarized what is the HTTP three-way handshake, the process of the HTTPS handshake and why HTTPS is secure.
Premise
When describing these two handshakes, there are some things that need to be explained in advance.
What is the difference between HTTP and TCP/IP?
TPC/IP protocol is a transport layer protocol, which mainly solves how to transmit data in the network, while HTTP is an application layer protocol, which mainly solves how to package data. WEB uses HTTP protocol as the application layer protocol to encapsulate HTTP text information, and then uses TCP/IP as the transport layer protocol to send it to the network.
The following diagram attempts to show the position of different TCP/IP and other protocols in the original OSI (Open System Interconnect) model:

PS: The form comes from online information
#What is the CA certificate?
CA (Certificate Authority) is a third-party authority responsible for managing and issuing certificates. It is trusted and recognized by all industries and the public.
CA certificate is a certificate issued by a CA. It can be used to verify whether a website is trustworthy (for HTTPS), to verify whether a file is trustworthy (whether it has been tampered with), etc. One certificate can also be used to prove another certificate. It is authentic and trustworthy, and the top-level certificate is called the root certificate. Except for the root certificate (which proves itself to be reliable), other certificates must rely on the higher-level certificate to prove themselves.
HTTP three-way handshake
HTTP (HyperText Transfer Protocol) Hypertext Transfer Protocol is the most widely used on the Internet A network protocol. Since the information is transmitted in clear text, it is considered insecure. As for the three-way handshake of HTTP, it actually uses the three-way TCP handshake to confirm the establishment of an HTTP connection.
As shown in the figure below, SYN (synchronous) is the handshake signal, Sequence number, and Acknowledge number used when TCP/IP establishes a connection. The three arrows pointing to it represent a three-way handshake. After the three-way handshake is completed, the client and server start transmitting data.

PS: The picture comes from online information
The first handshake: the client sends a syn packet (syn=j) to the server and enters the SYN_SEND state. Waiting for server confirmation;
Second handshake: The server receives the syn packet and must confirm the client's SYN (ack=j+1), and at the same time it also sends a SYN packet (syn=k), that is, SYN+ ACK packet, at this time the server enters the SYN_RECV state;
The third handshake: the client receives the SYN+ACK packet from the server and sends a confirmation packet ACK (ack=k+1) to the server. After the packet is sent, the client The client and server enter the ESTABLISHED state and complete the three-way handshake.
HTTPS handshake process
HTTPS adds the SSL protocol based on HTTP. SSL relies on certificates to verify the server. identity and encrypt communications between the browser and server. Specifically, how to perform encryption, decryption, and verification is shown in the figure below. The following is called a handshake. 

PS: The following description of the picture is taken from: http://zhuqil.cnblogs.com
1. Client Initiating an HTTPS request
2. Server configuration
The server using the HTTPS protocol must have a set of digital certificates. You can make it yourself or use a CA certificate. The difference is that the certificate issued by yourself needs to be verified by the client before you can continue to access, while using the CA certificate will not pop up the prompt page. This set of certificates is actually a pair of public and private keys. The public key is used for encryption by others, and the private key is used for decryption by yourself.
3. Transfer the certificate
This certificate is actually a public key, but it contains a lot of information, such as the issuing authority of the certificate, expiration time, etc. .
4. Client parsing certificate
#This part of the work is completed by the client's TLS. First, it will verify whether the public key is valid. For example, the issuing authority, expiration time, etc. If an abnormality is found, a warning box will pop up indicating that there is a problem with the certificate. If there is no problem with the certificate, then a random value is generated and then the random value is encrypted with the certificate.
5. Transmitting encrypted information
#This part transmits a random value encrypted with a certificate. The purpose is to let the server get this random value. value, future communication between the client and the server can be encrypted and decrypted through this random value.
6. Service segment decryption information
After the server decrypts with the private key, it obtains the random value (private key) passed by the client, and then symmetrically encrypts the content using this value. The so-called symmetric encryption is to mix information and private keys through a certain algorithm, so that unless the private key is known, the content cannot be obtained, and both the client and the server know the private key, so as long as the encryption algorithm is strong enough, The private key is complex enough and the data is secure enough.
7. Transmitting encrypted information
This part of the information is the information encrypted by the private key in the service segment, which can be used on the client. reduction.
8. The client decrypts the information
#The client uses the previously generated private key to decrypt the information passed by the service segment, and then obtains the decryption the following content.
PS: Even if the third party monitors the data during the entire handshake process, it is helpless.
Summary
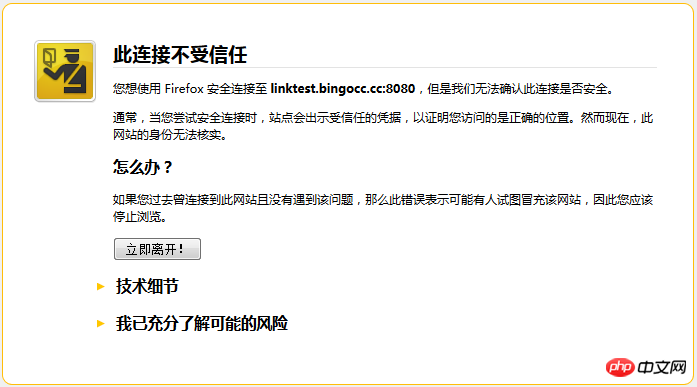
Why is HTTPS secure?
In the fourth step of the HTTPS handshake, if the site's certificate is not trusted, the following confirmation interface will be displayed to confirm the authenticity of the website. In addition, steps six and eight use the client's private key to encrypt and decrypt, ensuring the security of data transmission.
The difference between HTTPS and HTTP
1. The https protocol requires applying for a certificate from ca or a self-made certificate .
2. http information is transmitted in clear text, while https uses secure SSL encryption.
3. http transmits data directly with TCP, while https passes through a layer of SSL (OSI presentation layer) and uses different ports. The former is 80 (requires domestic filing) and the latter is 443. .
4. The http connection is very simple and stateless; the HTTPS protocol is a network protocol built from the SSL+HTTP protocol that can perform encrypted transmission and identity authentication, and is more secure than the http protocol.
Note that https encryption is completed at the transport layer
The https message is encrypted when it is packaged into a tcp message, whether it is Both the header domain and the body domain of https will be encrypted.
When using tcp layer tools such as tcpdump or wireshark to capture packets, the encrypted content is obtained, and if the application layer is used to capture Package, use Charels(Mac), Fildder(Windows) packet capture tool, then of course you will see it in clear text.
PS: HTTPS itself is for network transmission security.
Example, use wireshark to capture the packet:
http, you can see that the capture is in plain text:

https, you can see The one caught is ciphertext:

Appendix
The encryption and HASH algorithms generally used by HTTPS are as follows :
Asymmetric encryption algorithm: RSA, DSA/DSS
Symmetric encryption algorithm: AES, RC4, 3DES
HASH algorithm: MD5, SHA1, SHA256
The above is the detailed content of What is the HTTP vs HTTPS handshake. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1392
1392
 52
52
 What does http status code 520 mean?
Oct 13, 2023 pm 03:11 PM
What does http status code 520 mean?
Oct 13, 2023 pm 03:11 PM
HTTP status code 520 means that the server encountered an unknown error while processing the request and cannot provide more specific information. Used to indicate that an unknown error occurred when the server was processing the request, which may be caused by server configuration problems, network problems, or other unknown reasons. This is usually caused by server configuration issues, network issues, server overload, or coding errors. If you encounter a status code 520 error, it is best to contact the website administrator or technical support team for more information and assistance.
 What is http status code 403?
Oct 07, 2023 pm 02:04 PM
What is http status code 403?
Oct 07, 2023 pm 02:04 PM
HTTP status code 403 means that the server rejected the client's request. The solution to http status code 403 is: 1. Check the authentication credentials. If the server requires authentication, ensure that the correct credentials are provided; 2. Check the IP address restrictions. If the server has restricted the IP address, ensure that the client's IP address is restricted. Whitelisted or not blacklisted; 3. Check the file permission settings. If the 403 status code is related to the permission settings of the file or directory, ensure that the client has sufficient permissions to access these files or directories, etc.
 How to use Nginx Proxy Manager to implement reverse proxy under HTTPS protocol
Sep 26, 2023 am 08:40 AM
How to use Nginx Proxy Manager to implement reverse proxy under HTTPS protocol
Sep 26, 2023 am 08:40 AM
How to use NginxProxyManager to implement reverse proxy under HTTPS protocol. In recent years, with the popularity of the Internet and the diversification of application scenarios, the access methods of websites and applications have become more and more complex. In order to improve website access efficiency and security, many websites have begun to use reverse proxies to handle user requests. The reverse proxy for the HTTPS protocol plays an important role in protecting user privacy and ensuring communication security. This article will introduce how to use NginxProxy
 Understand common application scenarios of web page redirection and understand the HTTP 301 status code
Feb 18, 2024 pm 08:41 PM
Understand common application scenarios of web page redirection and understand the HTTP 301 status code
Feb 18, 2024 pm 08:41 PM
Understand the meaning of HTTP 301 status code: common application scenarios of web page redirection. With the rapid development of the Internet, people's requirements for web page interaction are becoming higher and higher. In the field of web design, web page redirection is a common and important technology, implemented through the HTTP 301 status code. This article will explore the meaning of HTTP 301 status code and common application scenarios in web page redirection. HTTP301 status code refers to permanent redirect (PermanentRedirect). When the server receives the client's
 How to use Nginx Proxy Manager to implement automatic jump from HTTP to HTTPS
Sep 26, 2023 am 11:19 AM
How to use Nginx Proxy Manager to implement automatic jump from HTTP to HTTPS
Sep 26, 2023 am 11:19 AM
How to use NginxProxyManager to implement automatic jump from HTTP to HTTPS. With the development of the Internet, more and more websites are beginning to use the HTTPS protocol to encrypt data transmission to improve data security and user privacy protection. Since the HTTPS protocol requires the support of an SSL certificate, certain technical support is required when deploying the HTTPS protocol. Nginx is a powerful and commonly used HTTP server and reverse proxy server, and NginxProxy
 Quick Application: Practical Development Case Analysis of PHP Asynchronous HTTP Download of Multiple Files
Sep 12, 2023 pm 01:15 PM
Quick Application: Practical Development Case Analysis of PHP Asynchronous HTTP Download of Multiple Files
Sep 12, 2023 pm 01:15 PM
Quick Application: Practical Development Case Analysis of PHP Asynchronous HTTP Download of Multiple Files With the development of the Internet, the file download function has become one of the basic needs of many websites and applications. For scenarios where multiple files need to be downloaded at the same time, the traditional synchronous download method is often inefficient and time-consuming. For this reason, using PHP to download multiple files asynchronously over HTTP has become an increasingly common solution. This article will analyze in detail how to use PHP asynchronous HTTP through an actual development case.
 Common network communication and security problems and solutions in C#
Oct 09, 2023 pm 09:21 PM
Common network communication and security problems and solutions in C#
Oct 09, 2023 pm 09:21 PM
Common network communication and security problems and solutions in C# In today's Internet era, network communication has become an indispensable part of software development. In C#, we usually encounter some network communication problems, such as data transmission security, network connection stability, etc. This article will discuss in detail common network communication and security issues in C# and provide corresponding solutions and code examples. 1. Network communication problems Network connection interruption: During the network communication process, the network connection may be interrupted, which may cause
 HTTP 200 OK: Understand the meaning and purpose of a successful response
Dec 26, 2023 am 10:25 AM
HTTP 200 OK: Understand the meaning and purpose of a successful response
Dec 26, 2023 am 10:25 AM
HTTP Status Code 200: Explore the Meaning and Purpose of Successful Responses HTTP status codes are numeric codes used to indicate the status of a server's response. Among them, status code 200 indicates that the request has been successfully processed by the server. This article will explore the specific meaning and use of HTTP status code 200. First, let us understand the classification of HTTP status codes. Status codes are divided into five categories, namely 1xx, 2xx, 3xx, 4xx and 5xx. Among them, 2xx indicates a successful response. And 200 is the most common status code in 2xx




