 Web Front-end
Web Front-end
 JS Tutorial
JS Tutorial
 Detailed explanation of Ajax method to achieve beautiful and secure login interface
Detailed explanation of Ajax method to achieve beautiful and secure login interface
Detailed explanation of Ajax method to achieve beautiful and secure login interface
The login interface is an essential function provided by the information system and is an interface that provides users with maintenance information. Next, I will lead you to create a beautiful and secure login interface. The technology used is ASP.NET+jQuery. This article mainly introduces in detail the Ajax method to implement a beautiful and secure login interface, which has certain reference value. Interested friends can refer to it.
Let’s take a look at the preview first
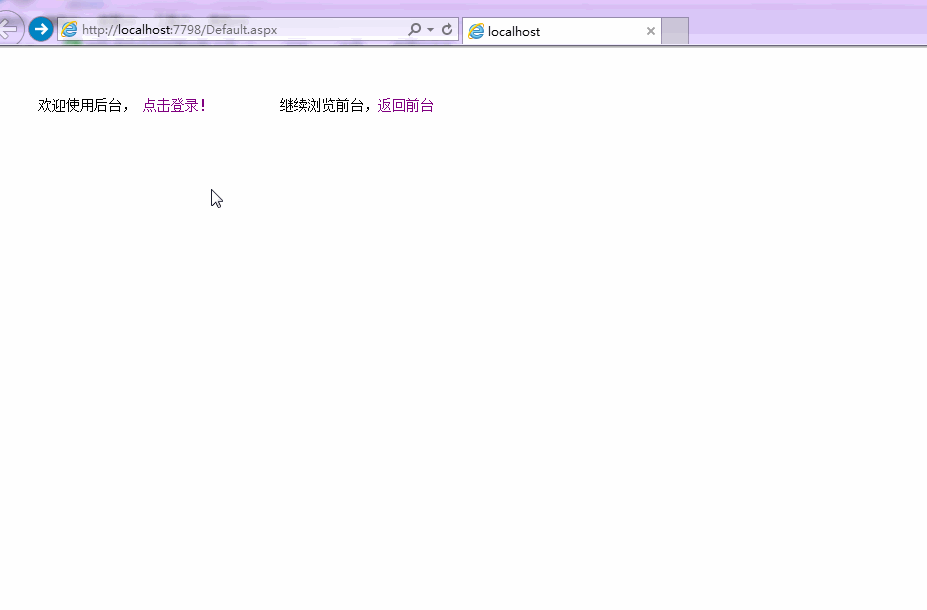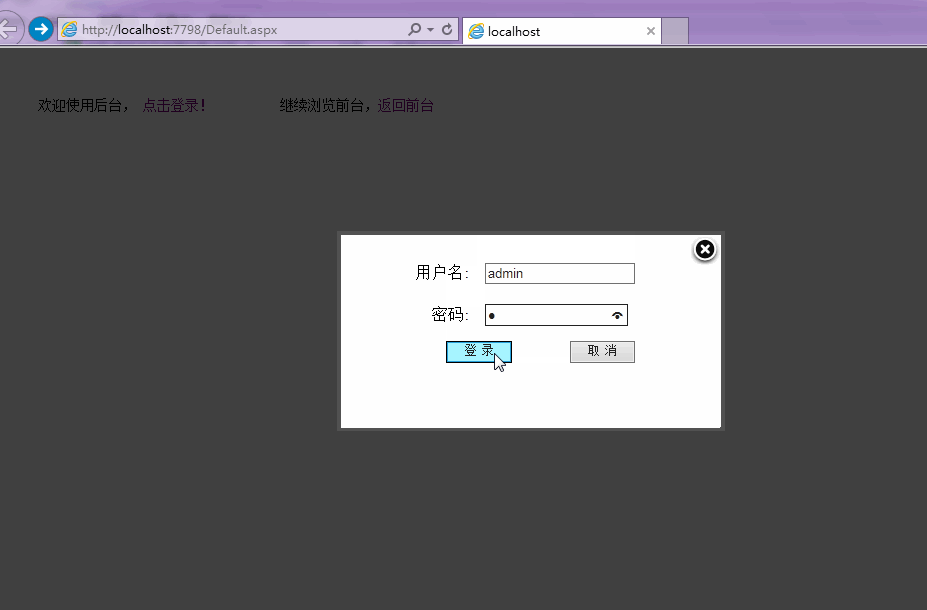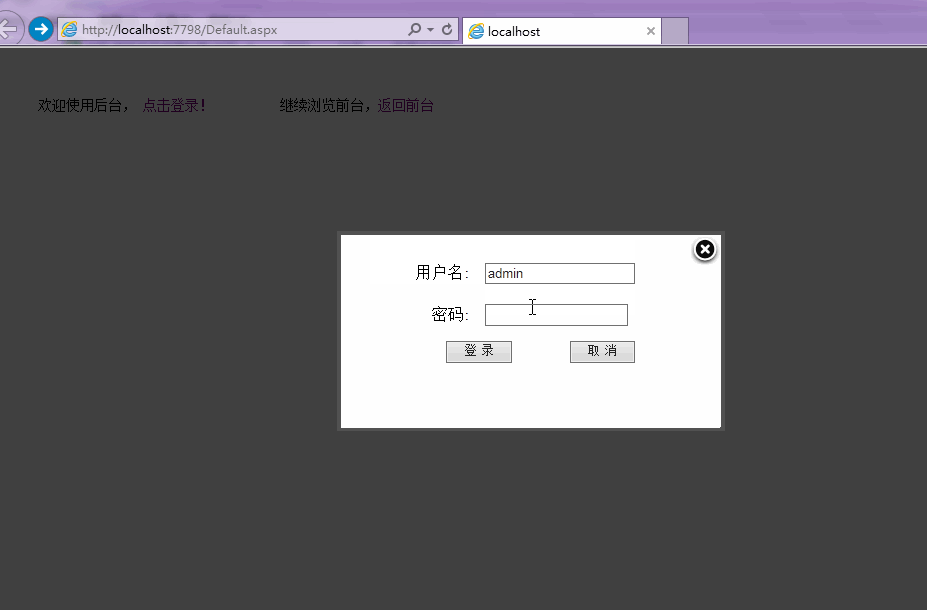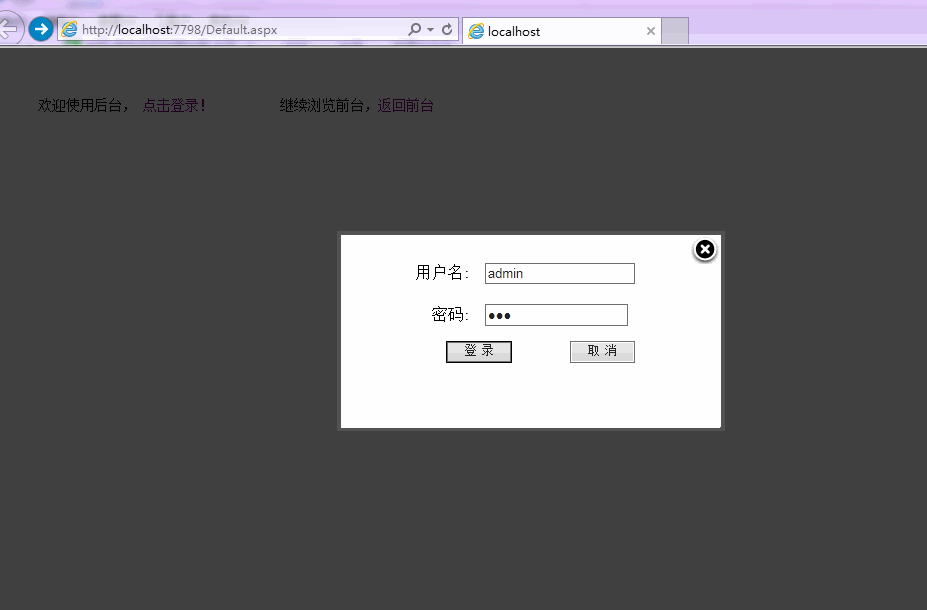
Ajax login focuses on Ajax. After entering the user name and password, use Ajax to submit the information to the server. The server The terminal determines that the user exists. If it exists, the login is successful and the user is redirected to the management interface (sometimes it is necessary to write cookies or use Session, which will not be discussed here). If it does not exist, it will prompt a login failure.
Basic flow chartAs follows
The above is the main idea. In order to create a secure login, we can use MD5 to pair the password before using ajax to transmit the password to the server. Encryption is performed. Of course, the encrypted string is also stored in the database. jQuery has such an MD5 encryption plug-in, which is very convenient to use.
If you know the process, you can easily implement it. The following are some main codes
Default.aspx: mainly provide hyperlinks, click on which will call thickbox and open the pop-up page.
<p style="margin-left:50px; margin-top:50px; ">
欢迎使用后台,
<a href="Login.htm?TB_iframe&height=180&width=350&modal=true" class="thickbox" id="myToolTip" title="点击登录,进入后台管理" >
点击登录!</a>
继续浏览前台,<a href="../Default.aspx">返回前台</a>login.htm: The real login interface, responsible for login logic
<script type="text/javascript" src="js/jquery-1.3.2.js"></script>
<script type="text/javascript">
$().ready(function () {
$('#Login').click(function () {
if ($('#username').val() == "" || $('#password').val() == "") {
alert("用户名或密码不能为空!");
}
else {
$.ajax({
type: "POST",
url: "Ajax/LoginHandler.ashx",
data: "username=" + escape($('#username').val()) + "&password=" + escape($('#password').val()),
beforeSend: function () {
$("#loading").css("display", "block"); //点击登录后显示loading,隐藏输入框
$("#login").css("display", "none");
},
success: function (msg) {
$("#loading").hide(); //隐藏loading
if (msg == "success") {
//parent.tb_remove();
parent.document.location.href = "admin.htm"; //如果登录成功则跳到管理界面
parent.tb_remove();
}
if (msg == "fail") {
alert("登录失败!");
}
},
complete: function (data) {
$("#loading").css("display", "none"); //点击登录后显示loading,隐藏输入框
$("#login").css("display", "block");
},
error: function (XMLHttpRequest, textStatus, thrownError) {
}
});
}
});
});
</script>
<p id="loading" style="text-align: center; display: none; padding-top: 10%">
<img src="images/loadingajax.gif" alt="loading" />
</p>
<p id="login" style="text-align: center">
<p style="position:absolute; right:0; top:0"><img src="images/closebox.png" onclick="parent.tb_remove()" alt="点击关闭" style="cursor:pointer" /></p>
<table border="0" cellpadding="3" cellspacing="3" style="margin: 0 auto;">
<tr>
<td style="text-align: right; padding: 10px">
<label>
用户名:</label>
</td>
<td>
<input id="username" type="text" size="20" />
</td>
</tr>
<tr>
<td style="text-align: right; padding: 10px">
<label>
密码:</label>
</td>
<td>
<input id="password" type="password" size="20" />
</td>
</tr>
<tr align="right">
<td colspan="2">
<input type="submit" id="Login" value=" 登 录 " style="margin-right: 50px">
<input type="submit" id="LoginCancel" value=" 取 消 " onclick="parent.tb_remove()">
</td>
</tr>
</table>
</p>LoginHandler.ashx: ajax processing Class, simple logic
string username = context.Request["username"].ToString();
string password = context.Request["password"].ToString();
//context.Response.Write(password);如果使用加密,则写入数据库要加密后的字段,然后登陆的时候就用加密后的字符串匹配
//此处连接数据库查看是否有此用户,此处为了方便起见,直接判断
if (username == "admin" && password == "1")
{
context.Response.Write("success");
//存储session
}
else
{
context.Response.Write("fail");
}ok, a simple login function is completed, of course, the password is not encrypted when logging in.
Let’s take a look at jQuery’s encryption plug-in MD5 plug-in. It is very convenient to use. By adding a reference to md5.js, you can use the $.md5() function to encrypt the string.
The above code is as follows Make slight changes and you can see the encrypted string. In
login.htm:
##
data: "username=" + escape($('#username').val()) + "&password=" + $.md5(escape($('#password').val())),
success: function (msg) {
$("#loading").hide(); //隐藏loading
alert(msg);
if (msg == "success") {
//parent.tb_remove();
parent.document.location.href = "admin.htm"; //如果登录成功则跳到管理界面
parent.tb_remove();
}
if (msg == "fail") {
alert("登录失败!");
}
}context.Response.Write(password);
ok, running the program again will pop up the MD5 encrypted string of the entered password. Related recommendations:Detailed explanation of the function of using jQuery+Angular to implement the login interface verification code
PHP registration and login interface implementation case (Recommended)_php example
Very beautiful user login interface HTML template_html/css_WEB-ITnose
The above is the detailed content of Detailed explanation of Ajax method to achieve beautiful and secure login interface. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 PHP vs. Ajax: Solutions for creating dynamically loaded content
Jun 06, 2024 pm 01:12 PM
PHP vs. Ajax: Solutions for creating dynamically loaded content
Jun 06, 2024 pm 01:12 PM
Ajax (Asynchronous JavaScript and XML) allows adding dynamic content without reloading the page. Using PHP and Ajax, you can dynamically load a product list: HTML creates a page with a container element, and the Ajax request adds the data to that element after loading it. JavaScript uses Ajax to send a request to the server through XMLHttpRequest to obtain product data in JSON format from the server. PHP uses MySQL to query product data from the database and encode it into JSON format. JavaScript parses the JSON data and displays it in the page container. Clicking the button triggers an Ajax request to load the product list.
 How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
Java framework design enables security by balancing security needs with business needs: identifying key business needs and prioritizing relevant security requirements. Develop flexible security strategies, respond to threats in layers, and make regular adjustments. Consider architectural flexibility, support business evolution, and abstract security functions. Prioritize efficiency and availability, optimize security measures, and improve visibility.
 PHP and Ajax: Building an autocomplete suggestion engine
Jun 02, 2024 pm 08:39 PM
PHP and Ajax: Building an autocomplete suggestion engine
Jun 02, 2024 pm 08:39 PM
Build an autocomplete suggestion engine using PHP and Ajax: Server-side script: handles Ajax requests and returns suggestions (autocomplete.php). Client script: Send Ajax request and display suggestions (autocomplete.js). Practical case: Include script in HTML page and specify search-input element identifier.
 How to implement PHP security best practices
May 05, 2024 am 10:51 AM
How to implement PHP security best practices
May 05, 2024 am 10:51 AM
How to Implement PHP Security Best Practices PHP is one of the most popular backend web programming languages used for creating dynamic and interactive websites. However, PHP code can be vulnerable to various security vulnerabilities. Implementing security best practices is critical to protecting your web applications from these threats. Input validation Input validation is a critical first step in validating user input and preventing malicious input such as SQL injection. PHP provides a variety of input validation functions, such as filter_var() and preg_match(). Example: $username=filter_var($_POST['username'],FILTER_SANIT
 Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
To protect your Struts2 application, you can use the following security configurations: Disable unused features Enable content type checking Validate input Enable security tokens Prevent CSRF attacks Use RBAC to restrict role-based access
 Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
When implementing machine learning algorithms in C++, security considerations are critical, including data privacy, model tampering, and input validation. Best practices include adopting secure libraries, minimizing permissions, using sandboxes, and continuous monitoring. The practical case demonstrates the use of the Botan library to encrypt and decrypt the CNN model to ensure safe training and prediction.
 PHP and Ajax: Ways to Improve Ajax Security
Jun 01, 2024 am 09:34 AM
PHP and Ajax: Ways to Improve Ajax Security
Jun 01, 2024 am 09:34 AM
In order to improve Ajax security, there are several methods: CSRF protection: generate a token and send it to the client, add it to the server side in the request for verification. XSS protection: Use htmlspecialchars() to filter input to prevent malicious script injection. Content-Security-Policy header: Restrict the loading of malicious resources and specify the sources from which scripts and style sheets are allowed to be loaded. Validate server-side input: Validate input received from Ajax requests to prevent attackers from exploiting input vulnerabilities. Use secure Ajax libraries: Take advantage of automatic CSRF protection modules provided by libraries such as jQuery.
 Which wallet is safer for SHIB coins? (Must read for newbies)
Jun 05, 2024 pm 01:30 PM
Which wallet is safer for SHIB coins? (Must read for newbies)
Jun 05, 2024 pm 01:30 PM
SHIB coin is no longer unfamiliar to investors. It is a conceptual token of the same type as Dogecoin. With the development of the market, SHIB’s current market value has ranked 12th. It can be seen that the SHIB market is hot and attracts countless investments. investors participate in investment. In the past, there have been frequent transactions and wallet security incidents in the market. Many investors have been worried about the storage problem of SHIB. They wonder which wallet is safer for SHIB coins at the moment? According to market data analysis, the relatively safe wallets are mainly OKXWeb3Wallet, imToken, and MetaMask wallets, which will be relatively safe. Next, the editor will talk about them in detail. Which wallet is safer for SHIB coins? At present, SHIB coins are placed on OKXWe





