 Database
Database
 Mysql Tutorial
Mysql Tutorial
 How to correctly use AES_ENCRYPT() and AES_DECRYPT() for encryption and decryption in MySQL
How to correctly use AES_ENCRYPT() and AES_DECRYPT() for encryption and decryption in MySQL
How to correctly use AES_ENCRYPT() and AES_DECRYPT() for encryption and decryption in MySQL
This article mainly introduces you to the correct method of encryption and decryption using AES_ENCRYPT() and AES_DECRYPT() in MySQL. The AES_ENCRYPT('password','key') function in MySQL can encrypt field values. AES_DECRYPT(table's Field name, 'key') function decryption processing, the article gives detailed sample code, friends in need can refer to it, I hope it can help everyone.
Preface
I recently encountered a requirement at work: I need to use the AES_ENCRYPT() function The plaintext was encrypted and stored in MySQL, but some problems were encountered... Let's introduce it in detail below.
It is said that the encrypted ciphertext will be NULL after decryption.
took a look and found the table structure she sent:
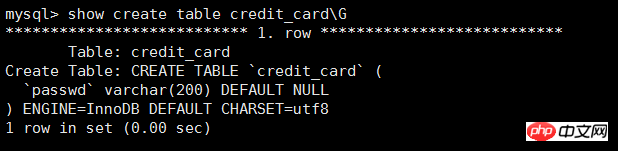
# After looking at it, she encrypted one through the AES_DECRYPT() function string, and then insert it. After successful execution, a warning is displayed: <br>Query OK, 1 row affected, 1 warning (0.00 sec)
(no The error was a warning, probably because of sql_mode)
At this time, she ignored the warning, and after decrypting it through AES_DECRYPT(), she found that the plaintext taken out was NULL.
Looking back at the table structure, we found that its field attribute is "varchar" && and the character set is ut8. The warning is as follows:
mysql> show warnings; +---------+------+------------------------------------------------------------------------+ | Level | Code | Message | +---------+------+------------------------------------------------------------------------+ | Warning | 1366 | Incorrect string value: '\xE3f767\x12...' for column 'passwd' at row 1 | +---------+------+------------------------------------------------------------------------+ 1 row in set (0.00 sec)
Checked it Document, take a look at the use of these two functions:
-- 将'hello world'加密,密钥为'key',加密后的串存在@pass中 mysql> SET @pass=AES_ENCRYPT('hello world', 'key'); Query OK, 0 rows affected (0.00 sec) -- 看一下加密后串的长度(都为2的整数次方) mysql> SELECT CHAR_LENGTH(@pass); +--------------------+ | CHAR_LENGTH(@pass) | +--------------------+ | 16 | +--------------------+ 1 row in set (0.00 sec) -- 使用AES_DECRYPT()解密 mysql> SELECT AES_DECRYPT(@pass, 'key'); +---------------------------+ | AES_DECRYPT(@pass, 'key') | +---------------------------+ | hello world | +---------------------------+ 1 row in set (0.00 sec)
So how to save it?
Method ①:
Set the field attributes to varbinary/binary/four blob types, and other binary field attributes.
Create three fields with attributes varbinary, binary, and blob.
Encrypt 'plaintext1', 'text2', 'plaintext_text3' with the key key and store them in the table.
Finally take it out.
mysql> CREATE TABLE t_passwd (pass1 varbinary(16), pass2 binary(16), pass3 blob); Query OK, 0 rows affected (0.00 sec) mysql> INSERT INTO t_passwd VALUES (AES_ENCRYPT('明文1', 'key'), AES_ENCRYPT('text2', 'key'), AES_ENCRYPT('明文_text3', 'key')); Query OK, 1 row affected (0.01 sec) mysql> SELECT AES_DECRYPT(pass1, 'key'), AES_DECRYPT(pass2, 'key'), AES_DECRYPT(pass3, 'key') FROM t_passwd; +---------------------------+---------------------------+---------------------------+ | AES_DECRYPT(pass1, 'key') | AES_DECRYPT(pass2, 'key') | AES_DECRYPT(pass3, 'key') | +---------------------------+---------------------------+---------------------------+ | 明文1 | text2 | 明文_text3 | +---------------------------+---------------------------+---------------------------+ 1 row in set (0.00 sec)
Of course, the length in the attribute brackets depends on the length of the plaintext. The plaintext here is shorter, so only 16 is given.
Method 2:
Convert the ciphertext to hexadecimal and then store it in the varchar/char column.
Here you need to use HEX() to deposit, and use UNHEX() to withdraw.
Create a field with a string attribute.
Encrypt 'hello world' with AES using the key 'key2', and then hexadecimalize the encrypted string through the HEX function.
Finally, take out the encrypted string through UNHEX, and then decrypt it through the AES key 'key2':
mysql> CREATE TABLE t_passwd_2(pass1 char(32)); Query OK, 0 rows affected (0.01 sec) mysql> INSERT INTO t_passwd_2 VALUES (HEX(AES_ENCRYPT('hello world', 'key2'))); Query OK, 1 row affected (0.00 sec) mysql> SELECT AES_DECRYPT(UNHEX(pass1), 'key2') FROM t_passwd_2; +-----------------------------------+ | AES_DECRYPT(UNHEX(pass1), 'key2') | +-----------------------------------+ | hello world | +-----------------------------------+ 1 row in set (0.00 sec)
Similarly, depending on the length of the plaintext, the AES_ENCRYPT encrypted string The string length will also change, so the string length after HEX will also change.
In actual use, a reasonable value needs to be evaluated based on the business.
Method ③:
is stored directly in varchar without hexadecimal conversion.
Going back to the beginning of the problem, it is not possible to store the encrypted string in the utf8 character set and the attribute is varchar.
In fact, just change the character set to latin1:
The warning will not be reported when inserting.
mysql> CREATE TABLE t_passwd_3(pass varchar(32)) CHARSET latin1; Query OK, 0 rows affected (0.00 sec) mysql> INSERT INTO t_passwd_3 SELECT AES_ENCRYPT('text', 'key3'); Query OK, 1 row affected (0.00 sec) Records: 1 Duplicates: 0 Warnings: 0 mysql> SELECT AES_DECRYPT(pass, 'key3') FROM t_passwd_3; +---------------------------+ | AES_DECRYPT(pass, 'key3') | +---------------------------+ | text | +---------------------------+ 1 row in set (0.00 sec)
Although this method is beautiful, it only needs to set the field character set to latin1, but it may bring hidden dangers:
The document writes this sentence:
Many encryption and compression functions return strings for which the result might contain arbitrary byte values. If you want to store these results, use a column with a VARBINARY or BLOB binary string data type. This will avoid potential problems with trailing space removal or character set conversion that would change data values, such as may occur if you use a nonbinary string data type (CHAR, VARCHAR, TEXT).
The general idea is that if you use method ③ , directly storing the encrypted string into the char/varchar/text type, which may have potential effects when converting characters or when spaces are deleted.
So if it must be stored in char/varchar/text, then refer to method ② and hexadecimalize it.
Or like method ①, store it directly in the binary field.
Related recommendations:
How to use OpenSSL instead of Mcrypt encryption and decryption in PHP?
WeChat applet development function introduction and encryption and decryption NODE-UUID introduction
Detailed explanation of PHP data compression, encryption and decryption (pack, unpack)
The above is the detailed content of How to correctly use AES_ENCRYPT() and AES_DECRYPT() for encryption and decryption in MySQL. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 How to open phpmyadmin
Apr 10, 2025 pm 10:51 PM
How to open phpmyadmin
Apr 10, 2025 pm 10:51 PM
You can open phpMyAdmin through the following steps: 1. Log in to the website control panel; 2. Find and click the phpMyAdmin icon; 3. Enter MySQL credentials; 4. Click "Login".
 MySQL: An Introduction to the World's Most Popular Database
Apr 12, 2025 am 12:18 AM
MySQL: An Introduction to the World's Most Popular Database
Apr 12, 2025 am 12:18 AM
MySQL is an open source relational database management system, mainly used to store and retrieve data quickly and reliably. Its working principle includes client requests, query resolution, execution of queries and return results. Examples of usage include creating tables, inserting and querying data, and advanced features such as JOIN operations. Common errors involve SQL syntax, data types, and permissions, and optimization suggestions include the use of indexes, optimized queries, and partitioning of tables.
 How to use single threaded redis
Apr 10, 2025 pm 07:12 PM
How to use single threaded redis
Apr 10, 2025 pm 07:12 PM
Redis uses a single threaded architecture to provide high performance, simplicity, and consistency. It utilizes I/O multiplexing, event loops, non-blocking I/O, and shared memory to improve concurrency, but with limitations of concurrency limitations, single point of failure, and unsuitable for write-intensive workloads.
 MySQL's Place: Databases and Programming
Apr 13, 2025 am 12:18 AM
MySQL's Place: Databases and Programming
Apr 13, 2025 am 12:18 AM
MySQL's position in databases and programming is very important. It is an open source relational database management system that is widely used in various application scenarios. 1) MySQL provides efficient data storage, organization and retrieval functions, supporting Web, mobile and enterprise-level systems. 2) It uses a client-server architecture, supports multiple storage engines and index optimization. 3) Basic usages include creating tables and inserting data, and advanced usages involve multi-table JOINs and complex queries. 4) Frequently asked questions such as SQL syntax errors and performance issues can be debugged through the EXPLAIN command and slow query log. 5) Performance optimization methods include rational use of indexes, optimized query and use of caches. Best practices include using transactions and PreparedStatemen
 Why Use MySQL? Benefits and Advantages
Apr 12, 2025 am 12:17 AM
Why Use MySQL? Benefits and Advantages
Apr 12, 2025 am 12:17 AM
MySQL is chosen for its performance, reliability, ease of use, and community support. 1.MySQL provides efficient data storage and retrieval functions, supporting multiple data types and advanced query operations. 2. Adopt client-server architecture and multiple storage engines to support transaction and query optimization. 3. Easy to use, supports a variety of operating systems and programming languages. 4. Have strong community support and provide rich resources and solutions.
 Monitor Redis Droplet with Redis Exporter Service
Apr 10, 2025 pm 01:36 PM
Monitor Redis Droplet with Redis Exporter Service
Apr 10, 2025 pm 01:36 PM
Effective monitoring of Redis databases is critical to maintaining optimal performance, identifying potential bottlenecks, and ensuring overall system reliability. Redis Exporter Service is a powerful utility designed to monitor Redis databases using Prometheus. This tutorial will guide you through the complete setup and configuration of Redis Exporter Service, ensuring you seamlessly build monitoring solutions. By studying this tutorial, you will achieve fully operational monitoring settings
 How to view sql database error
Apr 10, 2025 pm 12:09 PM
How to view sql database error
Apr 10, 2025 pm 12:09 PM
The methods for viewing SQL database errors are: 1. View error messages directly; 2. Use SHOW ERRORS and SHOW WARNINGS commands; 3. Access the error log; 4. Use error codes to find the cause of the error; 5. Check the database connection and query syntax; 6. Use debugging tools.
 How to connect to the database of apache
Apr 13, 2025 pm 01:03 PM
How to connect to the database of apache
Apr 13, 2025 pm 01:03 PM
Apache connects to a database requires the following steps: Install the database driver. Configure the web.xml file to create a connection pool. Create a JDBC data source and specify the connection settings. Use the JDBC API to access the database from Java code, including getting connections, creating statements, binding parameters, executing queries or updates, and processing results.



