With the development of technology, more and more users are beginning to use Internet of Things devices, and when users purchase these devices, they often choose products with more advanced and richer functions. But from the perspective of the security community, we are not paying enough "care" to these devices that are gradually "penetrating" into our lives.

Although many security researchers have conducted security analysis on Internet-connected devices in recent years, security threats still exist, and these things will definitely put users at security risks under. Today we will select for analysis a smart hub, a device that can be used for a variety of purposes, such as controlling sensors and devices in the home environment, for energy or water management, security monitoring or in security systems.
This small device can obtain information from all devices connected to it. If an unexpected situation occurs in the current environment, it will alert the user via mobile phone text message or email. Interestingly, it can also connect to local emergency services and send warning messages to users depending on the situation. So, if someone were able to hack into such a smart home system and take over the home controller, it would not only be a terrible nightmare for the user, but it would also impact the ability of emergency services to function.
During our analysis, we discovered multiple logic vulnerabilities that would serve as attack vectors for attackers.
Physical Access
First, we need to detect vulnerabilities that attackers can exploit from outside the network. The firmware for this hub was easily found online and can be downloaded directly. Therefore, anyone can directly analyze the firmware file and even modify the firmware content.
We also found that the password of the root account was stored in a hidden file and was encrypted using the DES algorithm. Some students may know that the DES encryption algorithm is not safe and is easy to crack. Therefore, an attacker can obtain the password hash through brute force and crack the password of the 'root' account.
In order to access the device with root privileges and modify files, or execute malicious commands, physical access is required.
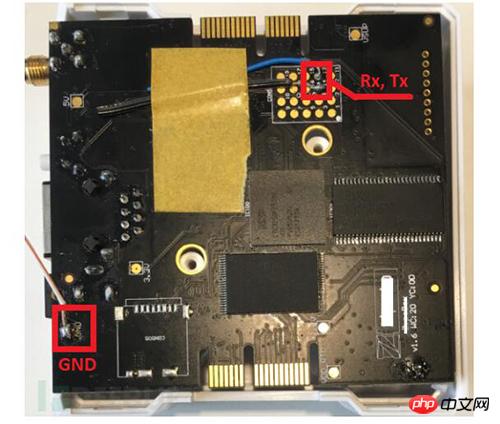
#We took apart the casing of the device, but this is not something all attackers are able to do. However, our further analysis showed that there were other ways to gain remote access to the device.
Remote Access
When configuring the hub and checking all connected devices, users can choose to use the mobile app or complete it through the web page. When the user settings are completed, all setting information will be encapsulated into the config.jar file, and the hub will download and execute these configurations.
But we can see that the config.jar file is sent via HTTP, and the device identifier uses the serial number of the device. Therefore, an attacker can use any serial number to send the same request and download the configuration file. Some students may think that the serial number is unique, but the developer said that the serial number is not well protected and can be obtained through brute force cracking. In order to obtain the serial number, a remote attacker can send a specially crafted forged request and use the server-side response information to determine whether the current serial number has been registered in the system.
In addition, our initial research also showed that many users will discuss their device issues in online forums or post photos of the hub on social networking sites, which may expose the device's serial number. , even if the attacker cannot crack the serial number, they can still try it through social engineering techniques.
When analyzing the config.jar file, we found that it contained the device's login name and password, which was enough information for an attacker to access user accounts through the web interface. Although the passwords in the file are encrypted, there are many open source tools or open source password databases that can help attackers decrypt the hashes. The most important thing is that when the user sets a password, the device does not require the user to enter a complex password (there are no requirements for length and mixture of English and digits), which reduces the difficulty of password cracking to a certain extent.
During our experiment, we successfully accessed the target user's smart home system. Not only did we obtain all configurations (including IP addresses) and sensor information, but we could also modify these data. In addition, the jar file also contains the user's private information, because users need to upload their mobile phone number to receive warnings and notifications.
Therefore, an attacker only needs to generate and send some fake requests to the server, and they may have remote access to the target user's smart home system, which does not use any two-factor authentication. In this way, the attacker can control the target user's "entire home", such as turning on and off the lights, turning on the faucet, or even opening the door, etc. From this point of view, smart home life is likely to become a nightmare for you.
Note: We have reported the details of the vulnerabilities to the relevant manufacturers, but these vulnerabilities have not been fixed yet.
Sunshine always comes after the storm
In addition to smart hubs, we also analyzed a smart light bulb. Although this product does not have very serious security vulnerabilities, there are still many security issues that surprised us.
Smart light bulbs can be connected to WiFi, and then users can control it through a mobile app. Therefore, users need to download the mobile App (Android or iOS), turn on the light bulb, connect to the WiFi hotspot created by the light bulb, and provide the light bulb with the SSID and password of the local WiFi network.
Through the App, users can turn lights on or off, set timers, or modify the brightness and color of lights. The goal of our research was to figure out how attackers could exploit vulnerabilities in smart light bulbs to gain access to local networks. After many attempts, we obtained the firmware of the light bulb through the mobile application. Interestingly, the light bulb does not directly interact with the mobile application. In fact, both the light bulb and the App need to be connected to a cloud service and interact through the cloud service.
We found that the light bulb will send a firmware update request to the server and download the update file through the HTTP protocol, which is obviously unsafe. If the attacker is on the same network, a man-in-the-middle attack becomes easy.
Through firmware reconnaissance and flash memory data extraction technology, we not only accessed the firmware files, but also obtained user data. However, further analysis showed that there was no sensitive data on the device or the internal network. However, we found credentials for all WiFi networks that the target bulb had previously connected to. This information is permanently stored in the device's flash memory, is not encrypted, and cannot be cleared even by pressing the "reset" button.
Summary
Our latest research shows that "smart home" does not mean "secure home." Many IoT devices currently have many logical vulnerabilities, and these vulnerabilities are likely to allow cybercriminals to "enter" your home.
 How to set up a secure VPS
How to set up a secure VPS
 Python online playback function implementation method
Python online playback function implementation method
 pr shortcut key
pr shortcut key
 How to open html files on ipad
How to open html files on ipad
 How to solve the problem of forgetting the power-on password of Windows 8 computer
How to solve the problem of forgetting the power-on password of Windows 8 computer
 Commonly used linux commands
Commonly used linux commands
 What should I do if my computer won't turn on?
What should I do if my computer won't turn on?
 delete folder in linux
delete folder in linux
 cad break line command
cad break line command




