Detailed explanation of the difference between HTTP and HTTPS
Hypertext Transfer Protocol HTTP protocol is used to transfer information between web browsers and website servers. The HTTP protocol sends content in clear text and does not provide any If an attacker intercepts the transmission message between the web browser and the website server, he can directly read the information. Therefore, the HTTP protocol is not suitable for transmitting some sensitive information, such as credit card numbers, passwords, etc. Payment Information.
The data transmitted by the HTTP protocol is unencrypted, that is, in plain text. Therefore, it is very unsafe to use the HTTP protocol to transmit private information. In order to ensure that these private data can be encrypted and transmitted, the Internet Jing Company designed the SSL (Secure Sockets Layer) protocol to encrypt data transmitted by the HTTP protocol, thus giving birth to HTTPS.
In order to solve this defect of the HTTP protocol, another protocol needs to be used: Secure Sockets Layer Hypertext Transfer Protocol HTTPS. For the security of data transmission, HTTPS is based on HTTP The SSL protocol is added to the browser. SSL relies on certificates to verify the identity of the server and encrypt the communication between the browser and the server.
Basic concept:
HTTP: It is the most widely used network protocol on the Internet. It is a client-side and server-side request and The response standard (TCP) is a transmission protocol used to transmit hypertext from the WWW server to the local browser. It can make the browser more efficient and reduce network transmission.
HTTPS: It is an HTTP channel aimed at security. Simply put, it is a secure version of HTTP, that is, an SSL layer is added to HTTP. The security foundation of HTTPS is SSL, so the details of encryption require SSL.
The main function of HTTPS protocol
Encrypted transmission;
Authentication.
Difference
1. The https protocol requires applying for a certificate from ca. Generally, there are fewer free certificates, so a certain fee is required.
2. http is a hypertext transfer protocol, and information is transmitted in plain text, while https is a secure SSL encrypted transmission protocol.
3. http and https use completely different connection methods and use different ports. The former is 80 and the latter is 443.
4. The http connection is very simple and stateless; the HTTPS protocol is a secure channel built by the SSL+HTTP protocol that can perform encrypted transmission and identity authentication, and is safer than the http protocol.
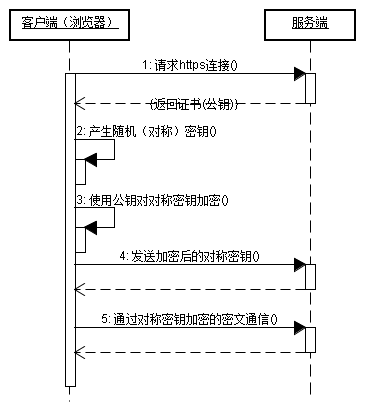
How HTTPS works
Customers use https URLs to access the web server and require an SSL connection to be established with the web server.
After the Web server receives the client's request, it will send a copy of the website's certificate information (the certificate contains the public key) to the client.
The client randomly creates a session key, then uses the website’s public key to encrypt the session key and transmits it to the website.
The Web server uses public key decryption to obtain the session key.
The web server and browser communicate through encryption and decryption of session key data
As shown in the figure:

Advantages of HTTPS
Using the HTTPS protocol can authenticate users and servers, ensuring that data is sent to the correct client and server;
HTTPS protocol is a network protocol built by SSL+HTTP protocol that can perform encrypted transmission and identity authentication. It is more secure than http protocol and can prevent data from being stolen or changed during transmission. Ensure data integrity.
HTTPS is the most secure solution under the current architecture. Although it is not absolutely safe, it greatly increases the cost of man-in-the-middle attacks.
Google adjusted its search engine algorithm in August 2014 and stated that "compared to equivalent HTTP websites, websites using HTTPS encryption will rank higher in search results."
Disadvantages of HTTPS
HTTPS protocol handshake phase is more time-consuming, which will extend the page loading time by nearly 50% and increase by 10 % to 20% of power consumption;
HTTPS connection caching is not as efficient as HTTP, which will increase data overhead and power consumption, and even existing security measures will be affected;
SSL certificates cost money. The more powerful the certificate, the higher the cost. Personal websites and small websites generally do not use it if it is not necessary.
SSL certificates usually need to be bound to an IP. Multiple domain names cannot be bound to the same IP. IPv4 resources cannot support this consumption.
http switches to HTTPS
Here you need to change all the links in the page, such as js, css, pictures, etc. Changed from http to https.
We can make http and https compatible when switching. The specific implementation method is to remove the http header in the page link, so that the http header and https header can be automatically matched. For example: change http://www.baidu.com to //www.baidu.com. Then when the user enters the access page from the http entrance, the page is http. If the user enters the access page from the https entrance, the page is https
Related recommendations:
PHP Http request http 500 The difference between http and https http 192.168.1.1
HTTP and HTTPS cross-domain sharing session solution
PHP simply implements HTTP and HTTPS cross-domain sharing session solutions
The above is the detailed content of Detailed explanation of the difference between HTTP and HTTPS. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Windows operating system is one of the most popular operating systems in the world, and its new version Win11 has attracted much attention. In the Win11 system, obtaining administrator rights is an important operation. Administrator rights allow users to perform more operations and settings on the system. This article will introduce in detail how to obtain administrator permissions in Win11 system and how to effectively manage permissions. In the Win11 system, administrator rights are divided into two types: local administrator and domain administrator. A local administrator has full administrative rights to the local computer
 Detailed explanation of division operation in Oracle SQL
Mar 10, 2024 am 09:51 AM
Detailed explanation of division operation in Oracle SQL
Mar 10, 2024 am 09:51 AM
Detailed explanation of division operation in OracleSQL In OracleSQL, division operation is a common and important mathematical operation, used to calculate the result of dividing two numbers. Division is often used in database queries, so understanding the division operation and its usage in OracleSQL is one of the essential skills for database developers. This article will discuss the relevant knowledge of division operations in OracleSQL in detail and provide specific code examples for readers' reference. 1. Division operation in OracleSQL
 Understand common application scenarios of web page redirection and understand the HTTP 301 status code
Feb 18, 2024 pm 08:41 PM
Understand common application scenarios of web page redirection and understand the HTTP 301 status code
Feb 18, 2024 pm 08:41 PM
Understand the meaning of HTTP 301 status code: common application scenarios of web page redirection. With the rapid development of the Internet, people's requirements for web page interaction are becoming higher and higher. In the field of web design, web page redirection is a common and important technology, implemented through the HTTP 301 status code. This article will explore the meaning of HTTP 301 status code and common application scenarios in web page redirection. HTTP301 status code refers to permanent redirect (PermanentRedirect). When the server receives the client's
 Detailed explanation of the role and usage of PHP modulo operator
Mar 19, 2024 pm 04:33 PM
Detailed explanation of the role and usage of PHP modulo operator
Mar 19, 2024 pm 04:33 PM
The modulo operator (%) in PHP is used to obtain the remainder of the division of two numbers. In this article, we will discuss the role and usage of the modulo operator in detail, and provide specific code examples to help readers better understand. 1. The role of the modulo operator In mathematics, when we divide an integer by another integer, we get a quotient and a remainder. For example, when we divide 10 by 3, the quotient is 3 and the remainder is 1. The modulo operator is used to obtain this remainder. 2. Usage of the modulo operator In PHP, use the % symbol to represent the modulus
 Detailed explanation of the linux system call system() function
Feb 22, 2024 pm 08:21 PM
Detailed explanation of the linux system call system() function
Feb 22, 2024 pm 08:21 PM
Detailed explanation of Linux system call system() function System call is a very important part of the Linux operating system. It provides a way to interact with the system kernel. Among them, the system() function is one of the commonly used system call functions. This article will introduce the use of the system() function in detail and provide corresponding code examples. Basic Concepts of System Calls System calls are a way for user programs to interact with the operating system kernel. User programs request the operating system by calling system call functions
 How to implement HTTP streaming using C++?
May 31, 2024 am 11:06 AM
How to implement HTTP streaming using C++?
May 31, 2024 am 11:06 AM
How to implement HTTP streaming in C++? Create an SSL stream socket using Boost.Asio and the asiohttps client library. Connect to the server and send an HTTP request. Receive HTTP response headers and print them. Receives the HTTP response body and prints it.
 Detailed explanation of Linux curl command
Feb 21, 2024 pm 10:33 PM
Detailed explanation of Linux curl command
Feb 21, 2024 pm 10:33 PM
Detailed explanation of Linux's curl command Summary: curl is a powerful command line tool used for data communication with the server. This article will introduce the basic usage of the curl command and provide actual code examples to help readers better understand and apply the command. 1. What is curl? curl is a command line tool used to send and receive various network requests. It supports multiple protocols, such as HTTP, FTP, TELNET, etc., and provides rich functions, such as file upload, file download, data transmission, proxy
 What does the https workflow look like?
Apr 07, 2024 am 09:27 AM
What does the https workflow look like?
Apr 07, 2024 am 09:27 AM
The https workflow includes steps such as client-initiated request, server response, SSL/TLS handshake, data transmission, and client-side rendering. Through these steps, the security and integrity of data during transmission can be ensured.