 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Implementation of RSA encryption and decryption algorithm functions
Implementation of RSA encryption and decryption algorithm functions
Implementation of RSA encryption and decryption algorithm functions
This time I will bring you the implementation of the RSA encryption and decryption algorithm function. What are the precautions for the implementation of the RSA encryption and decryption algorithm function. The following is a practical case, let's take a look.
You can first go to the website http://web.chacuo.net/netrsakeypair to generate public and private keys online
RSA asymmetric encryption algorithm, if it is public key encryption, just You have to use the private key to decrypt, and vice versa. If the private key is encrypted, use the public key to decrypt. The following are the relevant implementation functions
/**
* RSA私钥加密
* @param string $private_key 私钥
* @param string $data 要加密的字符串
* @return string $encrypted 返回加密后的字符串
* @author mosishu
*/
function privateEncrypt($private_key,$data){
$encrypted = '';
$pi_key = openssl_pkey_get_private($private_key);//这个函数可用来判断私钥是否是可用的,可用返回资源id Resource id
//最大允许加密长度为117,得分段加密
$plainData = str_split($data, 100);//生成密钥位数 1024 bit key
foreach($plainData as $chunk){
$partialEncrypted = '';
$encryptionOk = openssl_private_encrypt($chunk,$partialEncrypted,$pi_key);//私钥加密
if($encryptionOk === false){
return false;
}
$encrypted .= $partialEncrypted;
}
$encrypted = base64_encode($encrypted);//加密后的内容通常含有特殊字符,需要编码转换下,在网络间通过url传输时要注意base64编码是否是url安全的
return $encrypted;
}/**
* RSA公钥解密(私钥加密的内容通过公钥可以解密出来)
* @param string $public_key 公钥
* @param string $data 私钥加密后的字符串
* @return string $decrypted 返回解密后的字符串
* @author mosishu
*/
function publicDecrypt($public_key,$data){
$decrypted = '';
$pu_key = openssl_pkey_get_public($public_key);//这个函数可用来判断公钥是否是可用的
$plainData = str_split(base64_decode($data), 128);//生成密钥位数 1024 bit key
foreach($plainData as $chunk){
$str = '';
$decryptionOk = openssl_public_decrypt($chunk,$str,$pu_key);//公钥解密
if($decryptionOk === false){
return false;
}
$decrypted .= $str;
}
return $decrypted;
}//RSA公钥加密
function publicEncrypt($public_key,$data){
$encrypted = '';
$pu_key = openssl_pkey_get_public($public_key);
$plainData = str_split($data, 100);
foreach($plainData as $chunk){
$partialEncrypted = '';
$encryptionOk = openssl_public_encrypt($chunk,$partialEncrypted,$pu_key);//公钥加密
if($encryptionOk === false){
return false;
}
$encrypted .= $partialEncrypted;
}
$encrypted = base64_encode($encrypted);
return $encrypted;
}//RSA私钥解密
function privateDecrypt($private_key,$data){
$decrypted = '';
$pi_key = openssl_pkey_get_private($private_key);
$plainData = str_split(base64_decode($data), 128);
foreach($plainData as $chunk){
$str = '';
$decryptionOk = openssl_private_decrypt($chunk,$str,$pi_key);//私钥解密
if($decryptionOk === false){
return false;
}
$decrypted .= $str;
}
return $decrypted;
}I believe you have mastered the method after reading the case in this article. For more exciting information, please pay attention to php Other related articles on the Chinese website!
Recommended reading:
##phpStudy2018 installation tutorial
ThinkPHP implements WeChat payment (jsapi payment) process tutorial detailed explanation_php example
The above is the detailed content of Implementation of RSA encryption and decryption algorithm functions. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 The difference between vivox100s and x100: performance comparison and function analysis
Mar 23, 2024 pm 10:27 PM
The difference between vivox100s and x100: performance comparison and function analysis
Mar 23, 2024 pm 10:27 PM
Both vivox100s and x100 mobile phones are representative models in vivo's mobile phone product line. They respectively represent vivo's high-end technology level in different time periods. Therefore, the two mobile phones have certain differences in design, performance and functions. This article will conduct a detailed comparison between these two mobile phones in terms of performance comparison and function analysis to help consumers better choose the mobile phone that suits them. First, let’s look at the performance comparison between vivox100s and x100. vivox100s is equipped with the latest
 How to implement dual WeChat login on Huawei mobile phones?
Mar 24, 2024 am 11:27 AM
How to implement dual WeChat login on Huawei mobile phones?
Mar 24, 2024 am 11:27 AM
How to implement dual WeChat login on Huawei mobile phones? With the rise of social media, WeChat has become one of the indispensable communication tools in people's daily lives. However, many people may encounter a problem: logging into multiple WeChat accounts at the same time on the same mobile phone. For Huawei mobile phone users, it is not difficult to achieve dual WeChat login. This article will introduce how to achieve dual WeChat login on Huawei mobile phones. First of all, the EMUI system that comes with Huawei mobile phones provides a very convenient function - dual application opening. Through the application dual opening function, users can simultaneously
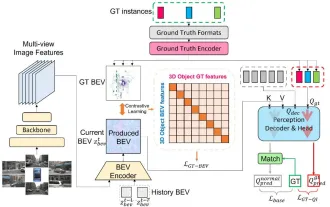 CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
Written above & the author’s personal understanding: At present, in the entire autonomous driving system, the perception module plays a vital role. The autonomous vehicle driving on the road can only obtain accurate perception results through the perception module. The downstream regulation and control module in the autonomous driving system makes timely and correct judgments and behavioral decisions. Currently, cars with autonomous driving functions are usually equipped with a variety of data information sensors including surround-view camera sensors, lidar sensors, and millimeter-wave radar sensors to collect information in different modalities to achieve accurate perception tasks. The BEV perception algorithm based on pure vision is favored by the industry because of its low hardware cost and easy deployment, and its output results can be easily applied to various downstream tasks.
 Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Common challenges faced by machine learning algorithms in C++ include memory management, multi-threading, performance optimization, and maintainability. Solutions include using smart pointers, modern threading libraries, SIMD instructions and third-party libraries, as well as following coding style guidelines and using automation tools. Practical cases show how to use the Eigen library to implement linear regression algorithms, effectively manage memory and use high-performance matrix operations.
 What exactly is self-media? What are its main features and functions?
Mar 21, 2024 pm 08:21 PM
What exactly is self-media? What are its main features and functions?
Mar 21, 2024 pm 08:21 PM
With the rapid development of the Internet, the concept of self-media has become deeply rooted in people's hearts. So, what exactly is self-media? What are its main features and functions? Next, we will explore these issues one by one. 1. What exactly is self-media? We-media, as the name suggests, means you are the media. It refers to an information carrier through which individuals or teams can independently create, edit, publish and disseminate content through the Internet platform. Different from traditional media, such as newspapers, television, radio, etc., self-media is more interactive and personalized, allowing everyone to become a producer and disseminator of information. 2. What are the main features and functions of self-media? 1. Low threshold: The rise of self-media has lowered the threshold for entering the media industry. Cumbersome equipment and professional teams are no longer needed.
 Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
The bottom layer of the C++sort function uses merge sort, its complexity is O(nlogn), and provides different sorting algorithm choices, including quick sort, heap sort and stable sort.
 PHP Programming Guide: Methods to Implement Fibonacci Sequence
Mar 20, 2024 pm 04:54 PM
PHP Programming Guide: Methods to Implement Fibonacci Sequence
Mar 20, 2024 pm 04:54 PM
The programming language PHP is a powerful tool for web development, capable of supporting a variety of different programming logics and algorithms. Among them, implementing the Fibonacci sequence is a common and classic programming problem. In this article, we will introduce how to use the PHP programming language to implement the Fibonacci sequence, and attach specific code examples. The Fibonacci sequence is a mathematical sequence defined as follows: the first and second elements of the sequence are 1, and starting from the third element, the value of each element is equal to the sum of the previous two elements. The first few elements of the sequence
 What are the functions of Xiaohongshu account management software? How to operate a Xiaohongshu account?
Mar 21, 2024 pm 04:16 PM
What are the functions of Xiaohongshu account management software? How to operate a Xiaohongshu account?
Mar 21, 2024 pm 04:16 PM
As Xiaohongshu becomes popular among young people, more and more people are beginning to use this platform to share various aspects of their experiences and life insights. How to effectively manage multiple Xiaohongshu accounts has become a key issue. In this article, we will discuss some of the features of Xiaohongshu account management software and explore how to better manage your Xiaohongshu account. As social media grows, many people find themselves needing to manage multiple social accounts. This is also a challenge for Xiaohongshu users. Some Xiaohongshu account management software can help users manage multiple accounts more easily, including automatic content publishing, scheduled publishing, data analysis and other functions. Through these tools, users can manage their accounts more efficiently and increase their account exposure and attention. In addition, Xiaohongshu account management software has



