 Web Front-end
Web Front-end
 JS Tutorial
JS Tutorial
 How to verify the user's account password, mobile phone number and ID card using regular expressions
How to verify the user's account password, mobile phone number and ID card using regular expressions
How to verify the user's account password, mobile phone number and ID card using regular expressions
这次给大家带来用正则验证用户的帐号密码以及手机号码与身份证的方法,用正则验证用户的帐号密码以及手机号码与身份证的注意事项有哪些,下面就是实战案例,一起来看一下。
废话不多说了,下面给大家介绍使用正则表达式验证用户名、密码、手机号码、身份证的写法,需要的的朋友参考下吧
//用户名
+ (BOOL) validateUserName:(NSString *)name
{
NSString *userNameRegex = @"^[A-Za-z0-9]{3,20}+$";
NSPredicate *userNamePredicate = [NSPredicate predicateWithFormat:@"SELF MATCHES %@",userNameRegex];
BOOL B = [userNamePredicate evaluateWithObject:name];
return B;
}
//密码
+ (BOOL) validatePassword:(NSString *)passWord
{
NSString *passWordRegex = @"^[a-zA-Z0-9]{6,20}+$";
NSPredicate *passWordPredicate = [NSPredicate predicateWithFormat:@"SELF MATCHES %@",passWordRegex];
return [passWordPredicate evaluateWithObject:passWord];
}
//判断手机号码格式是否正确
+ (BOOL)valiMobile:(NSString *)mobile
{
mobile = [mobile stringByReplacingOccurrencesOfString:@" " withString:@""];
if (mobile.length != 11)
{
return NO;
}else{
/**
* 移动号段正则表达式
*/
NSString *CM_NUM = @"^((13[4-9])|(147)|(15[0-2,7-9])|(178)|(18[2-4,7-8]))\\d{8}|(1705)\\d{7}$";
/**
* 联通号段正则表达式
*/
NSString *CU_NUM = @"^((13[0-2])|(145)|(15[5-6])|(176)|(18[5,6]))\\d{8}|(1709)\\d{7}$";
/**
* 电信号段正则表达式
*/
NSString *CT_NUM = @"^((133)|(153)|(177)|(18[0,1,9]))\\d{8}$";
NSPredicate *pred1 = [NSPredicate predicateWithFormat:@"SELF MATCHES %@", CM_NUM];
BOOL isMatch1 = [pred1 evaluateWithObject:mobile];
NSPredicate *pred2 = [NSPredicate predicateWithFormat:@"SELF MATCHES %@", CU_NUM];
BOOL isMatch2 = [pred2 evaluateWithObject:mobile];
NSPredicate *pred3 = [NSPredicate predicateWithFormat:@"SELF MATCHES %@", CT_NUM];
BOOL isMatch3 = [pred3 evaluateWithObject:mobile];
if (isMatch1 || isMatch2 || isMatch3) {
return YES;
}else{
return NO;
}
}
}
/**
* 验证身份证号码是否正确的方法
*
* @param IDNumber 传进身份证号码字符串
*
* @return 返回YES或NO表示该身份证号码是否符合国家标准
*/
+ (BOOL)isCorrect:(NSString *)IDNumber
{
NSMutableArray *IDArray = [NSMutableArray array];
// 遍历身份证字符串,存入数组中
if (IDNumber.length == 18) {
for (int i = 0; i < 18; i++) {
NSRange range = NSMakeRange(i, 1);
NSString *subString = [IDNumber substringWithRange:range];
[IDArray addObject:subString];
}
}else{
for (int i = 0; i < 15; i++) {
NSRange range = NSMakeRange(i, 1);
NSString *subString = [IDNumber substringWithRange:range];
[IDArray addObject:subString];
}
}
// 系数数组
NSArray *coefficientArray = [NSArray arrayWithObjects:@"7", @"9", @"10", @"5", @"8", @"4", @"2", @"1", @"6", @"3", @"7", @"9", @"10", @"5", @"8", @"4", @"2", nil];
// 余数数组
NSArray *remainderArray = [NSArray arrayWithObjects:@"1", @"0", @"X", @"9", @"8", @"7", @"6", @"5", @"4", @"3", @"2", nil];
// 每一位身份证号码和对应系数相乘之后相加所得的和
int sum = 0;
if (IDNumber.length == 18) {
for (int i = 0; i < 17; i++) {
int coefficient = [coefficientArray[i] intValue];
int ID = [IDArray[i] intValue];
sum += coefficient * ID;
}
}else{
for (int i = 0; i < 14; i++) {
int coefficient = [coefficientArray[i] intValue];
int ID = [IDArray[i] intValue];
sum += coefficient * ID;
}
}
// 这个和除以11的余数对应的数
NSString *str = remainderArray[(sum % 11)];
// 身份证号码最后一位
NSString *string;
if (IDNumber.length == 18) {
string = [IDNumber substringFromIndex:17];
}else{
string = [IDNumber substringFromIndex:14];
}
// 如果这个数字和身份证最后一位相同,则符合国家标准,返回YES
if ([str isEqualToString:string]) {
return YES;
} else {
return NO;
}
}相信看了本文案例你已经掌握了方法,更多精彩请关注php中文网其它相关文章!
推荐阅读:
The above is the detailed content of How to verify the user's account password, mobile phone number and ID card using regular expressions. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to use Xiaohongshu account to find users? Can I find my mobile phone number?
Mar 22, 2024 am 08:40 AM
How to use Xiaohongshu account to find users? Can I find my mobile phone number?
Mar 22, 2024 am 08:40 AM
With the rapid development of social media, Xiaohongshu has become one of the most popular social platforms. Users can create a Xiaohongshu account to show their personal identity and communicate and interact with other users. If you need to find a user’s Xiaohongshu number, you can follow these simple steps. 1. How to use Xiaohongshu account to find users? 1. Open the Xiaohongshu APP, click the "Discover" button in the lower right corner, and then select the "Notes" option. 2. In the note list, find the note posted by the user you want to find. Click to enter the note details page. 3. On the note details page, click the "Follow" button below the user's avatar to enter the user's personal homepage. 4. In the upper right corner of the user's personal homepage, click the three-dot button and select "Personal Information"
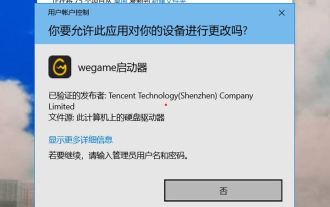 How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
How to solve the problem that Windows 11 prompts you to enter the administrator username and password to continue?
Apr 11, 2024 am 09:10 AM
When using Win11 system, sometimes you will encounter a prompt that requires you to enter the administrator username and password. This article will discuss how to deal with this situation. Method 1: 1. Click [Windows Logo], then press [Shift+Restart] to enter safe mode; or enter safe mode this way: click the Start menu and select Settings. Select "Update and Security"; select "Restart Now" in "Recovery"; after restarting and entering the options, select - Troubleshoot - Advanced Options - Startup Settings -&mdash
 Log in to Ubuntu as superuser
Mar 20, 2024 am 10:55 AM
Log in to Ubuntu as superuser
Mar 20, 2024 am 10:55 AM
In Ubuntu systems, the root user is usually disabled. To activate the root user, you can use the passwd command to set a password and then use the su- command to log in as root. The root user is a user with unrestricted system administrative rights. He has permissions to access and modify files, user management, software installation and removal, and system configuration changes. There are obvious differences between the root user and ordinary users. The root user has the highest authority and broader control rights in the system. The root user can execute important system commands and edit system files, which ordinary users cannot do. In this guide, I'll explore the Ubuntu root user, how to log in as root, and how it differs from a normal user. Notice
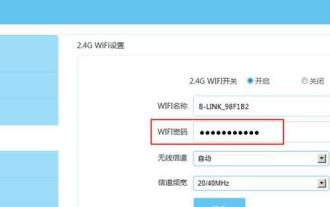 How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
Wireless networks have become an indispensable part of people's lives in today's digital world. Protecting the security of personal wireless networks is particularly important, however. Setting a strong password is key to ensuring that your WiFi network cannot be hacked by others. To ensure your network security, this article will introduce in detail how to use your mobile phone to change the router WiFi password. 1. Open the router management page - Open the router management page in the mobile browser and enter the router's default IP address. 2. Enter the administrator username and password - To gain access, enter the correct administrator username and password in the login page. 3. Navigate to the wireless settings page - find and click to enter the wireless settings page, in the router management page. 4. Find the current Wi
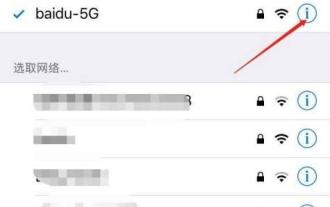 Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Wireless networks have become an indispensable part of our lives with the rapid development of the Internet. In order to protect personal information and network security, it is very important to change your wifi password regularly, however. To help you better protect your home network security, this article will introduce you to a detailed tutorial on how to use your mobile phone to change your WiFi password. 1. Understand the importance of WiFi passwords. WiFi passwords are the first line of defense to protect personal information and network security. In the Internet age, understanding its importance can better understand why passwords need to be changed regularly. 2. Confirm that the phone is connected to wifi. First, make sure that the phone is connected to the wifi network whose password you want to change before changing the wifi password. 3. Open the phone’s settings menu and enter the phone’s settings menu.
 What is sudo and why is it important?
Feb 21, 2024 pm 07:01 PM
What is sudo and why is it important?
Feb 21, 2024 pm 07:01 PM
sudo (superuser execution) is a key command in Linux and Unix systems that allows ordinary users to run specific commands with root privileges. The function of sudo is mainly reflected in the following aspects: Providing permission control: sudo achieves strict control over system resources and sensitive operations by authorizing users to temporarily obtain superuser permissions. Ordinary users can only obtain temporary privileges through sudo when needed, and do not need to log in as superuser all the time. Improved security: By using sudo, you can avoid using the root account during routine operations. Using the root account for all operations may lead to unexpected system damage, as any mistaken or careless operation will have full permissions. and
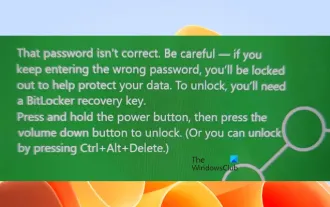 Incorrect password, beware BitLocker warning
Mar 26, 2024 am 09:41 AM
Incorrect password, beware BitLocker warning
Mar 26, 2024 am 09:41 AM
This article will explore how to solve the problem of wrong password, especially the need to be careful when dealing with BitLocker warnings. This warning is triggered when an incorrect password is entered multiple times in BitLocker to unlock the drive. Usually, this warning occurs because the system has a policy that limits incorrect login attempts (usually three login attempts are allowed). In this case, the user will receive an appropriate warning message. The complete warning message is as follows: The password entered is incorrect. Please note that continuously entering incorrect passwords will cause the account to be locked. This is to protect the security of your data. If you need to unlock your account, you will need to use a BitLocker recovery key. The password is incorrect, beware the BitLocker warning you receive when you log in to your computer
 How to use Passkey for your Microsoft account
Feb 19, 2024 am 11:03 AM
How to use Passkey for your Microsoft account
Feb 19, 2024 am 11:03 AM
Passkey is a more advanced and secure way to log in and can be used with a Microsoft account. This article will guide you how to use Passkey in your Microsoft account, introduce its advantages and the differences with passwords. Before we get into the details, we emphasize that if you frequently forget your passwords or need to log in quickly, Passkey will generally be better for you. What is Passkey? How are they different from passwords? Passwords are an advanced and secure authentication method that can replace traditional password logins. Each application has a unique key, ensuring security and preventing threats like phishing. Users can confirm their identity via email and password, or use facial recognition, fingerprint or security key





