Detailed explanation of js injection usage
This time I will bring you a detailed explanation of the use of js injection. What are the precautions when using js injection? Here are practical cases, let’s take a look.
There has been news recently that four employees of Alibaba’s network security department used web page vulnerabilities to write js scripts to steal moon cakes, so I became interested and wanted to know how to write this js script, and how to swipe orders in various ways. How is the gun robbery accomplished?
What is a javascript injection attack?
1. Whenever user input is accepted and redisplayed, the website is vulnerable to JavaScript injection attacks. Let’s examine a specific application that is vulnerable to JavaScript injection attacks. Let's say you've created a customer feedback website. Customers can visit the website and enter feedback about the product. When a customer submits feedback, the feedback information reappears on the feedback page.
Customer Feedback Website is a simple website. Unfortunately, this site is vulnerable to JavaScript injection attacks.
Suppose the following text is being entered into a customer feedback form:
<script>alert("Attack!")</script>
This Text represents the JavaScript script that displays the warning message box. After someone submits this script to a customer feedback form, the message Attack! appears when anyone visits the customer feedback site in the future.
2. Another method is to enter a js code in the browser address bar to change the content of the page js variables and page tags.
Using Javascript injection, the user can change the content of the web page without closing or saving it, which is done on the browser's address bar. The syntax of the command is as follows:
javascript:alert(#command#)
For example, if you want to go to http://www.example.comIf you see an alert warning box on the site, first enter the URL in the address bar and wait for the page to load, then delete the URL and enter:
javascript:alert("Hello World")
as the new URL. This will pop up a "Hello World" alert box, and you can use this technique to change almost any content on the web page, such as an image. Suppose there is a website logo picture, and we find a piece of HTML code by looking at the page source file:

The image is named "hi", the source file is "hello.gif", we want to change it to "bye.jpeg" stored on our site (http://www.mysite.com) file, so the complete URL address of the image is http://www.mysite.com/bye.jpeg. Using Javascript injection, we only need to enter on the address bar:
javascript:alert(document .hi.src="http://www.mysite.com/bye.jpeg")
You will see the pop-up "http://www.mysite.com/bye.jpeg" "alert warning, and then the picture was changed. It’s important to note that these changes are only temporary! If you refresh the page or re-enter, your changes will disappear because you only made the changes on your PC, not on the web server.
Using the same method, we can view or change the value of the variable . For example, we find a piece of code like this on the web page:
<SCRIPT LANGUAGE="JavaScript"> var a="test" </SCRIPT>
means that the value of variable a is "test", now we enter:
javascript:alert(a)
Then we change its value to "hello":
javascript:alert(a="hello")
Javascript injection is usually used to change form properties. Suppose there is a piece of code like this:
<form name="format" action="send.php" method="post"> <input type="hidden" name="mail" value="someone@somewhere.com"> <input type="text" name="name"> <input type="submit" value="submit"></form>
We want the form to be sent to our email address, not someone@somewhere.com. You can use the following command:
javascript:alert(document.format.mail.value="me@hacker.com")
•也许你已经注意到了这些命令的层次关系:
•我们按照从左到右的顺序依次说明:
•1)最左边是document
•2)然后是我们想要更改的对象名(比如document.hi.src)或其包含的对象(比如document.format.mail.value)
•3)最后是我们想要更改的属性(比如源路径:document.hi.src,或变量值:document.format.mail.value)
•4)使用“.”号分隔
•5)当我们想要更改属性值的时候,我们使用“=”号和新的属性值
•*注释:当新的属性值为字符串时(比如:document.format.mail.value="me@hacker.com")需要用双引号把它括起来。
•如果我们想要把它作为一个变量的值,则不需要使用双引号""。例如我们想要将变量b的值赋予变量a,我们可以输入javascript:alert(a=b)。
•但是,页面中的大部分标签都没有名字,比如:
<form action="send.php" method="post"> <input type="hidden" name="mail" value="someone@somewhere.com"> <input type="text" name="name"> <input type="submit" value="submit"></form>
在这段代码中没有表单名,综合上面这些信息,可以使用此命令:
javascript:alert(document. .mail.value="me@hacker.com")
在这种情况下我们必须统计并找出表单序号,下面是一个例子:
<form action="send.php" method="post"> <input type="text" name="name"> <input type="submit" value="submit"> </form> <form action="send.php" method="post"> <input type="hidden" name="mail" value="someone@somewhere.com"> <input type="text" name="name"> <input type="submit" value="submit"> </form> <form action="send.php" method="post"> <input type="text" name="name"> <input type="submit" value="submit"> </form>
•在以上代码中我们看见了3个表单,但我们只对第二个感兴趣,因此我们想要的表单序号就是2。不要忘记我们是从1开始计算的,比如1,2,3,4...而javascript却从0开始计算,比如0,1,2,3...所以真正的表单序号是1,不是2,通常我们要把找到的表单序号减一。我们将用这个序号来补全我们的命令:
javascript:alert(document.forms[1].mail.value="me@hacker.com")
•这样你就可以更改没有名字的图片或链接了,你可以把“forms”换成任何你想要的标签类型。对于图片就是
javascript:alert(document.images[3].src="#the url of the picture you want#")
对于链接就是
javascript:alert(document.links[0].href="#the url you want#")
最后,我们可以用这个技巧来编辑cookies。下面的命令由triviasecurity.net的Dr_aMado编写,我只修改了一点点,让它在用户编辑之前显示出来。你只要把它们复制到地址栏就可以了:
javascript:alert(window.c=function a(n,v,nv){c=document.cookie;c=c.substring(c.indexOf(n)+n.length,c.length);
c=c.substring(1,( (c.indexOf(";")>-1) ? c.indexOf(";") : c.length));nc=unescape(c).replace(v,nv);
document.cookie=n+"="+escape(nc);return unescape(document.cookie);});
alert('The cookie is: "'+document.cookie+'"');alert(c(prompt("The name of the cookie:",""),
prompt("Change this value:",""),prompt("with this:","")))//如果你想要手动更改你的cookie,可以使用下面这条命令:
javascript:alert(document.cookie)
这将显示你的当前cookie,假设是“userid=1”,如果你想把它改成“userid=2”,可以使用下列命令:
javascript:alert(document.cookie="userid=2")
最后我必须强调的是,所有的更改都只是在客户端!就像是把网页保存在你的PC上然后修改它。尽管如此,使用这一技巧你仍然可以欺骗页面(例如cookies)或绕过安全验证。例如一些网页会检测用户发送数据的位置,如果从http://www.test.com/form.php发送数据到http://www.test.com/check.php,check.php可能会检测数据是否来自http: //www.test.com/form.php上的表单。除此之外,如果你打算在页面中输入你自己的JavaScript代码,通过使用一些这样的技巧,你将能够更改图片并保持不变!
最后的最后,既然js注入这么可怕,我们自己写的网站有什么解决办法来防止js注入呢?
方法一:
阻止 JavaScript 注入攻击的一种简单方法是重新在视图中显示数据时,用 HTML 编码任何网站用户输入的数据
如:<%=Html.Encode(feedback.Message)%>
使用 HTML 编码一个字符串的含意是什么呢?使用 HTML 编码字符串时,危险字符如 < 和 > 被替换为 HTML 实体,如 < 和 >。所以,当使用 HTML 编码字符串 <script>alert("Boo!")</script> 时,它将转换为 <script>alert("Attack!")</script>。浏览器在解析编码的字符串时不再执行 JavaScript 脚本。而是显示无害的页面。
Method 2:
In addition to using HTML to encode the data when displaying it in the view, you can also use HTML to encode the data before submitting it to the database.
StringEscapeUtils.escapeHtml("Data submitted by the front desk");
Generally, people like to use the first method discussed in this tutorial rather than the second method. Two methods. The problem with the second approach is that you end up with HTML-encoded data in the database. In other words, the data in the database will contain strange characters. What's the harm? If you need to display database data in a form other than a web page, you will encounter problems. For example, data cannot be easily displayed in a Windows Forms application.
I believe you have mastered the method after reading the case in this article. For more exciting information, please pay attention to other related articles on the php Chinese website!
Recommended reading:
In JS Time unit comparison method
The above is the detailed content of Detailed explanation of js injection usage. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1393
1393
 52
52
 37
37
 110
110
 What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
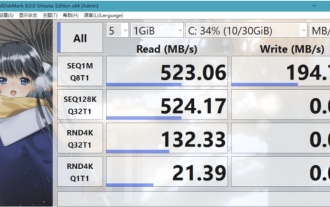
CrystalDiskMark is a small HDD benchmark tool for hard drives that quickly measures sequential and random read/write speeds. Next, let the editor introduce CrystalDiskMark to you and how to use crystaldiskmark~ 1. Introduction to CrystalDiskMark CrystalDiskMark is a widely used disk performance testing tool used to evaluate the read and write speed and performance of mechanical hard drives and solid-state drives (SSD). Random I/O performance. It is a free Windows application and provides a user-friendly interface and various test modes to evaluate different aspects of hard drive performance and is widely used in hardware reviews
 How to download foobar2000? -How to use foobar2000
Mar 18, 2024 am 10:58 AM
How to download foobar2000? -How to use foobar2000
Mar 18, 2024 am 10:58 AM
foobar2000 is a software that can listen to music resources at any time. It brings you all kinds of music with lossless sound quality. The enhanced version of the music player allows you to get a more comprehensive and comfortable music experience. Its design concept is to play the advanced audio on the computer The device is transplanted to mobile phones to provide a more convenient and efficient music playback experience. The interface design is simple, clear and easy to use. It adopts a minimalist design style without too many decorations and cumbersome operations to get started quickly. It also supports a variety of skins and Theme, personalize settings according to your own preferences, and create an exclusive music player that supports the playback of multiple audio formats. It also supports the audio gain function to adjust the volume according to your own hearing conditions to avoid hearing damage caused by excessive volume. Next, let me help you
 How to use NetEase Mailbox Master
Mar 27, 2024 pm 05:32 PM
How to use NetEase Mailbox Master
Mar 27, 2024 pm 05:32 PM
NetEase Mailbox, as an email address widely used by Chinese netizens, has always won the trust of users with its stable and efficient services. NetEase Mailbox Master is an email software specially created for mobile phone users. It greatly simplifies the process of sending and receiving emails and makes our email processing more convenient. So how to use NetEase Mailbox Master, and what specific functions it has. Below, the editor of this site will give you a detailed introduction, hoping to help you! First, you can search and download the NetEase Mailbox Master app in the mobile app store. Search for "NetEase Mailbox Master" in App Store or Baidu Mobile Assistant, and then follow the prompts to install it. After the download and installation is completed, we open the NetEase email account and log in. The login interface is as shown below
 How to use Baidu Netdisk app
Mar 27, 2024 pm 06:46 PM
How to use Baidu Netdisk app
Mar 27, 2024 pm 06:46 PM
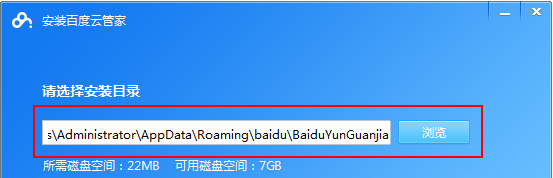
Cloud storage has become an indispensable part of our daily life and work nowadays. As one of the leading cloud storage services in China, Baidu Netdisk has won the favor of a large number of users with its powerful storage functions, efficient transmission speed and convenient operation experience. And whether you want to back up important files, share information, watch videos online, or listen to music, Baidu Cloud Disk can meet your needs. However, many users may not understand the specific use method of Baidu Netdisk app, so this tutorial will introduce in detail how to use Baidu Netdisk app. Users who are still confused can follow this article to learn more. ! How to use Baidu Cloud Network Disk: 1. Installation First, when downloading and installing Baidu Cloud software, please select the custom installation option.
 Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Windows operating system is one of the most popular operating systems in the world, and its new version Win11 has attracted much attention. In the Win11 system, obtaining administrator rights is an important operation. Administrator rights allow users to perform more operations and settings on the system. This article will introduce in detail how to obtain administrator permissions in Win11 system and how to effectively manage permissions. In the Win11 system, administrator rights are divided into two types: local administrator and domain administrator. A local administrator has full administrative rights to the local computer
 BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
MetaMask (also called Little Fox Wallet in Chinese) is a free and well-received encryption wallet software. Currently, BTCC supports binding to the MetaMask wallet. After binding, you can use the MetaMask wallet to quickly log in, store value, buy coins, etc., and you can also get 20 USDT trial bonus for the first time binding. In the BTCCMetaMask wallet tutorial, we will introduce in detail how to register and use MetaMask, and how to bind and use the Little Fox wallet in BTCC. What is MetaMask wallet? With over 30 million users, MetaMask Little Fox Wallet is one of the most popular cryptocurrency wallets today. It is free to use and can be installed on the network as an extension
 Detailed explanation of division operation in Oracle SQL
Mar 10, 2024 am 09:51 AM
Detailed explanation of division operation in Oracle SQL
Mar 10, 2024 am 09:51 AM
Detailed explanation of division operation in OracleSQL In OracleSQL, division operation is a common and important mathematical operation, used to calculate the result of dividing two numbers. Division is often used in database queries, so understanding the division operation and its usage in OracleSQL is one of the essential skills for database developers. This article will discuss the relevant knowledge of division operations in OracleSQL in detail and provide specific code examples for readers' reference. 1. Division operation in OracleSQL
 Teach you how to use the new advanced features of iOS 17.4 'Stolen Device Protection'
Mar 10, 2024 pm 04:34 PM
Teach you how to use the new advanced features of iOS 17.4 'Stolen Device Protection'
Mar 10, 2024 pm 04:34 PM
Apple rolled out the iOS 17.4 update on Tuesday, bringing a slew of new features and fixes to iPhones. The update includes new emojis, and EU users will also be able to download them from other app stores. In addition, the update also strengthens the control of iPhone security and introduces more "Stolen Device Protection" setting options to provide users with more choices and protection. "iOS17.3 introduces the "Stolen Device Protection" function for the first time, adding extra security to users' sensitive information. When the user is away from home and other familiar places, this function requires the user to enter biometric information for the first time, and after one hour You must enter information again to access and change certain data, such as changing your Apple ID password or turning off stolen device protection.




