
This article introduces in detail a simple symmetric encryption function in PHP to implement data encryption and decryption. It also introduces symmetric encryption and asymmetric encryption in detail. You can learn more if you need it.
There is a place in the project where the need to encrypt the user ID and transmit it to the next contact point for decryption is used. (Forgive me for not revealing too much -_-!) The first thing that came to mind was a function in Kangsheng Ucenter. Later I searched and found a simple method in Concise Magic, so I integrated it to form function that you use.
1. Symmetric encryption
The sender uses the key and algorithm to process the plaintext into ciphertext and sends it, and the receiver uses the key and algorithm to process the ciphertext into In plain text, both the sender and the receiver use the same key to encrypt and decrypt the data.

Because the same key is used for encryption and decryption, security is not only related to the algorithm, but also the security of the key is also very important.
Of course, it is not that the more complex the key, the better. On the contrary, the key is usually smaller, because although the larger the key, the stronger the encryption, but the slower the encryption and decryption process, so the size of the key is both Safety must be taken into consideration as well as efficiency.
After all, the characteristics of the symmetric encryption algorithm are that the algorithm is public, the amount of calculation is small, the encryption speed is fast, and the encryption efficiency is high. Without the advantage of high efficiency, it is better to use asymmetric encryption directly.
In addition, every time each pair of users uses a symmetric encryption algorithm, they need to use a unique key that is unknown to others. This will cause the number of keys owned by both senders and receivers to increase exponentially. Management becomes a burden on users.
Symmetric encryption algorithms are more difficult to use on distributed network systems, mainly because key management is difficult and the cost of use is high.
2. Asymmetric encryption
Asymmetric encryption is relatively safer. It uses a pair of keys, a public key and a private key. , used for encryption and decryption respectively. The private key can only be kept securely by one party and cannot be leaked, while the public key can be sent to anyone who requests it.
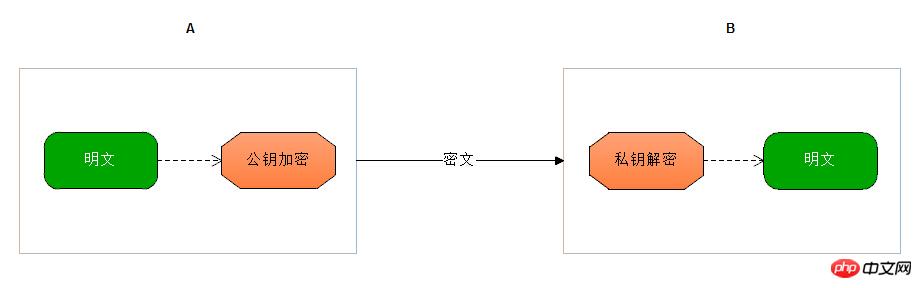
#The most common asymmetric encryption is probably the banking system and payment platform. For example, when we apply for an Alipay or UnionPay payment interface, we will get a public key. When making a payment in the mall, we use the public key to encrypt the information and submit it to the platform. The platform uses the key to decrypt your information and perform payment operations.
Although asymmetric encryption is very secure, it is very slow compared to symmetric encryption, so when we generally deal with it, most of us use symmetric encryption to transmit messages, but the key used in symmetric encryption is we It can be sent through asymmetric encryption. Think back to the payment interface you applied for. Did it give you a pair of keys? ^.^
3. Combined use
Symmetric encryption is fast and is better when sending large amounts of data. Asymmetric encryption encryption and decryption takes a long time and is slow, and is only suitable for encrypting a small amount of data. However, the security of asymmetric encryption is extremely high.
Maximize strengths and avoid weaknesses: Encrypt the symmetric encryption key using the asymmetric encryption public key, and then send it out. The recipient uses the private key to decrypt to obtain the symmetric encryption key, and then both parties can use symmetric encryption. communicate.

The methods used in the project should not be disclosed, but only two other examples are listed here. The first one is from ucenter, and the second one is seen in Concise Magic.
It should be noted that because it is a base64 algorithm, the encrypted string may appear \. If it is used in the URL, it is unfriendly. You can use external or modified methods to verify recursion. Remove it.
/**
* 字符串加密以及解密函数
* @param string $string 原文或者密文
* @param string $operation 操作(ENCODE | DECODE), 默认为 DECODE
* @param string $key 密钥
* @param int $expiry 密文有效期, 加密时候有效, 单位 秒,0 为永久有效
* @return string 处理后的 原文或者 经过 base64_encode 处理后的密文
*/
function _authcode ($string, $operation = 'DECODE', $key = 'Ruesin', $expiry = 0)
{
$ckey_length = 4;
$key = md5($key);
$keya = md5(substr($key, 0, 16));
$keyb = md5(substr($key, 16, 16));
$keyc = $ckey_length ? ($operation == 'DECODE' ? substr($string, 0,
$ckey_length) : substr(md5(microtime()), - $ckey_length)) : '';
$cryptkey = $keya . md5($keya . $keyc);
$key_length = strlen($cryptkey);
$string = $operation == 'DECODE' ? base64_decode(
substr($string, $ckey_length)) : sprintf('%010d',
$expiry ? $expiry + time() : 0) . substr(md5($string . $keyb), 0, 16) .
$string;
$string_length = strlen($string);
$result = '';
$box = range(0, 255);
$rndkey = array();
for ($i = 0; $i <= 255; $i ++) {
$rndkey[$i] = ord($cryptkey[$i % $key_length]);
}
for ($j = $i = 0; $i < 256; $i ++) {
$j = ($j + $box[$i] + $rndkey[$i]) % 256;
$tmp = $box[$i];
$box[$i] = $box[$j];
$box[$j] = $tmp;
}
for ($a = $j = $i = 0; $i < $string_length; $i ++) {
$a = ($a + 1) % 256;
$j = ($j + $box[$a]) % 256;
$tmp = $box[$a];
$box[$a] = $box[$j];
$box[$j] = $tmp;
$result .= chr(ord($string[$i]) ^ ($box[($box[$a] + $box[$j]) % 256]));
}
if ($operation == 'DECODE') {
if ((substr($result, 0, 10) == 0 || substr($result, 0, 10) - time() > 0) &&
substr($result, 10, 16) ==
substr(md5(substr($result, 26) . $keyb), 0, 16)) {
return substr($result, 26);
} else {
return '';
}
} else {
return $keyc . str_replace('=', '', base64_encode($result));
}
}/*********************************************************************
函数名称:encrypt
函数作用:加密解密字符串
使用方法:
加密 :encrypt('str','E','nowamagic');
解密 :encrypt('被加密过的字符串','D','nowamagic');
参数说明:
$string :需要加密解密的字符串
$operation:判断是加密还是解密:E:加密 D:解密
$key :加密的钥匙(密匙);
*********************************************************************/
function encrypt($string,$operation,$key='')
{
$key=md5($key);
$key_length=strlen($key);
$string=$operation=='D'?base64_decode($string):substr(md5($string.$key),0,8).$string;
$string_length=strlen($string);
$rndkey=$box=array();
$result='';
for($i=0;$i<=255;$i++)
{
$rndkey[$i]=ord($key[$i%$key_length]);
$box[$i]=$i;
}
for($j=$i=0;$i<256;$i++)
{
$j=($j+$box[$i]+$rndkey[$i])%256;
$tmp=$box[$i];
$box[$i]=$box[$j];
$box[$j]=$tmp;
}
for($a=$j=$i=0;$i<$string_length;$i++)
{
$a=($a+1)%256;
$j=($j+$box[$a])%256;
$tmp=$box[$a];
$box[$a]=$box[$j];
$box[$j]=$tmp;
$result.=chr(ord($string[$i])^($box[($box[$a]+$box[$j])%256]));
}
if($operation=='D')
{
if(substr($result,0,8)==substr(md5(substr($result,8).$key),0,8))
{
return substr($result,8);
}
else
{
return'';
}
}
else
{
return str_replace('=','',base64_encode($result));
}
}The above is the entire content of this article, I hope it will be helpful to everyone’s study .
Related recommendations:
Redis multi-database selection function singleton class implemented in PHP (detailed explanation)
PHP strategy mode definition and usage (detailed explanation)
The above is the detailed content of Detailed explanation of PHP symmetric encryption function to implement data encryption and decryption. For more information, please follow other related articles on the PHP Chinese website!




