 Java
Java
 javaTutorial
javaTutorial
 Introduction to Java Permission Framework: Shiro's Unified Authentication and Authorization
Introduction to Java Permission Framework: Shiro's Unified Authentication and Authorization
Introduction to Java Permission Framework: Shiro's Unified Authentication and Authorization
Shiro’s Unified Authentication and Authorization
Shiro is a simple, easy-to-use Java permissions framework under Apache. For single applications, Shiro can perfectly and quickly meet permission requirements. Therefore, Shiro will generally become the first choice of developers when working on projects.
However, if you need to make a second, third, or nth application that also requires the same authentication and authorization, you may need to extend Shiro or integrate other frameworks. It meets your needs very well.
How Shiro performs authentication and authorization
Shiro itself does not help you achieve authentication and authorization, but Shiro has well defined some concepts related to permissions, allowing you to complete specific implementations
Authentication
In Shiro, completing authentication is generally subject.login(token). Subject represents a user, and Token represents the authorization information submitted when a user requests authorization. Through AuthenticatingRealm .doGetAuthenticationInfo() obtains some information about the current Subject, such as Principals, Credentials, and verifies the submitted token. If the login is successful, save the current logged-in userAuthorization
in Shiro , Permission control is generally like @RequiresPermissions. When a user accesses a protected resource, Shiro will use AuthorizingRealm.doGetAuthorizationInfo() to obtain the user's permissions from the Principals of the currently authenticated Subject to determine whether the user can access the resource
In Shiro, the above two things are accomplished by implementing Realm. When you have a single application, it is very simple to complete the authentication and authorization of the application.
But what should you do when you have multiple applications and need to reuse the same set of users and permission information? You can reuse Realm and the user permissions are in the same db. This is possible, but The coupling is too high, and different applications must access the same data source; or the DAO related to user permissions can be stripped out and used as an RPC or Rest call, which can also be implemented; but a better way is to separate the entire authentication and authorization Come out and serve as an authentication and authorization service alone
Unified authentication and authorization based on Shiro
In order to achieve unified authentication and authorization, Shiro has CasFilter, which can integrate CAS, but CAS is another set of frameworks, which is more important , there is a separate learning cost, so here is a simpler, lightweight, easy-to-use, Shiro-based authentication and authorization service shiro-uaa
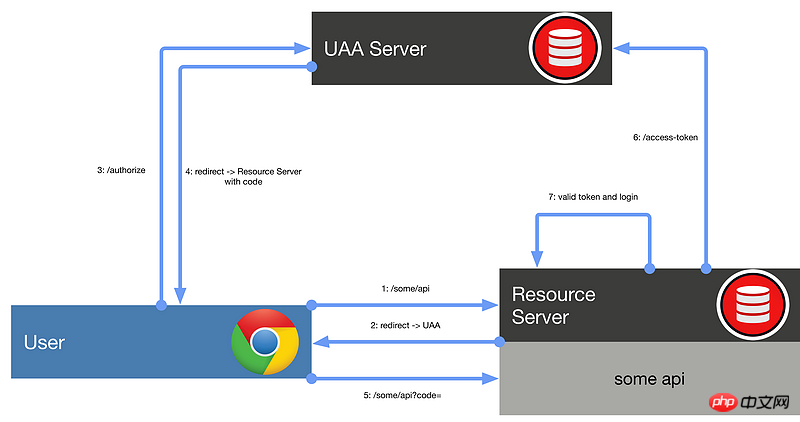
Authentication and authorization process
User requests protected resources Resource Server
Resource Server determines whether the user is logged in
If not logged in, Resource Server guides the user to UAA Server to log in
The user logs in to the UAA Server. If the login is successful, the UAA Server returns the code to the user and guides the user to the previously visited Resource Server
-
Resource Server uses code to obtain access-token from UAA Server. The token contains user authorization information
Resource Server verifies whether the accessToken is legal. If it is legal, saves the user information in Resource Server
As shown below:
Use
auth-server
Quote maven
Implement your own login
resource-server
Quote maven
Like shiro, use relevant annotations for permission control
Detailed explanation of Shiro authorization implementation
##Apache Shiro User Manual (1) Shiro Architecture IntroductionThe above is the detailed content of Introduction to Java Permission Framework: Shiro's Unified Authentication and Authorization. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Perfect Number in Java
Aug 30, 2024 pm 04:28 PM
Perfect Number in Java
Aug 30, 2024 pm 04:28 PM
Guide to Perfect Number in Java. Here we discuss the Definition, How to check Perfect number in Java?, examples with code implementation.
 Weka in Java
Aug 30, 2024 pm 04:28 PM
Weka in Java
Aug 30, 2024 pm 04:28 PM
Guide to Weka in Java. Here we discuss the Introduction, how to use weka java, the type of platform, and advantages with examples.
 Smith Number in Java
Aug 30, 2024 pm 04:28 PM
Smith Number in Java
Aug 30, 2024 pm 04:28 PM
Guide to Smith Number in Java. Here we discuss the Definition, How to check smith number in Java? example with code implementation.
 Java Spring Interview Questions
Aug 30, 2024 pm 04:29 PM
Java Spring Interview Questions
Aug 30, 2024 pm 04:29 PM
In this article, we have kept the most asked Java Spring Interview Questions with their detailed answers. So that you can crack the interview.
 Break or return from Java 8 stream forEach?
Feb 07, 2025 pm 12:09 PM
Break or return from Java 8 stream forEach?
Feb 07, 2025 pm 12:09 PM
Java 8 introduces the Stream API, providing a powerful and expressive way to process data collections. However, a common question when using Stream is: How to break or return from a forEach operation? Traditional loops allow for early interruption or return, but Stream's forEach method does not directly support this method. This article will explain the reasons and explore alternative methods for implementing premature termination in Stream processing systems. Further reading: Java Stream API improvements Understand Stream forEach The forEach method is a terminal operation that performs one operation on each element in the Stream. Its design intention is
 TimeStamp to Date in Java
Aug 30, 2024 pm 04:28 PM
TimeStamp to Date in Java
Aug 30, 2024 pm 04:28 PM
Guide to TimeStamp to Date in Java. Here we also discuss the introduction and how to convert timestamp to date in java along with examples.
 Java Program to Find the Volume of Capsule
Feb 07, 2025 am 11:37 AM
Java Program to Find the Volume of Capsule
Feb 07, 2025 am 11:37 AM
Capsules are three-dimensional geometric figures, composed of a cylinder and a hemisphere at both ends. The volume of the capsule can be calculated by adding the volume of the cylinder and the volume of the hemisphere at both ends. This tutorial will discuss how to calculate the volume of a given capsule in Java using different methods. Capsule volume formula The formula for capsule volume is as follows: Capsule volume = Cylindrical volume Volume Two hemisphere volume in, r: The radius of the hemisphere. h: The height of the cylinder (excluding the hemisphere). Example 1 enter Radius = 5 units Height = 10 units Output Volume = 1570.8 cubic units explain Calculate volume using formula: Volume = π × r2 × h (4
 How to Run Your First Spring Boot Application in Spring Tool Suite?
Feb 07, 2025 pm 12:11 PM
How to Run Your First Spring Boot Application in Spring Tool Suite?
Feb 07, 2025 pm 12:11 PM
Spring Boot simplifies the creation of robust, scalable, and production-ready Java applications, revolutionizing Java development. Its "convention over configuration" approach, inherent to the Spring ecosystem, minimizes manual setup, allo



