 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 How can the CPU protect your data and privacy from being stolen by malicious code? Basic introduction to Intel SGX
How can the CPU protect your data and privacy from being stolen by malicious code? Basic introduction to Intel SGX
How can the CPU protect your data and privacy from being stolen by malicious code? Basic introduction to Intel SGX
This article brings you a basic introduction to Intel SGX. It has certain reference value. Friends in need can refer to it. I hope it will be helpful to you.
Basic introduction to Intel SGX
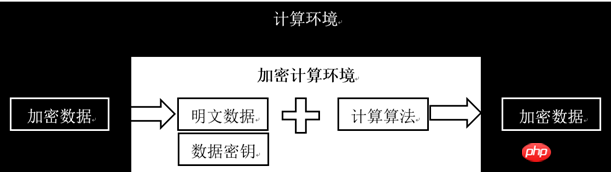
Intel SGX (Intel Software Guard Extension) is an extension of the Intel instruction set architecture. SGX provides you with an Enclave, an encrypted trusted execution area in memory, where the CPU protects your data and privacy from being stolen by malicious code.
Principle
SGX uses the new processor instructions to allocate a part of the area EPC (Enclave Page Cache) in the memory, through the CPU The encryption engine MEE (Memory Encryption Engine) encrypts the data in it. The encrypted content in EPC will not be decrypted into plaintext until it enters the CPU. Therefore, in SGX, you do not need to trust the operating system, VMM, or even BIOS. You only need to trust the CPU to ensure that private data will not be leaked.
Application
In actual application, you can encrypt the private data and transfer it to the circle on the cloud in the form of ciphertext, and The corresponding secret key is also transmitted to the circle through remote certification. The data is then used to perform calculations under the encryption protection of the CPU, and the results are returned to you in ciphertext. In this mode, you can take advantage of the powerful computing power of cloud computing without worrying about data leakage.
EDL (Enclave Definition Language)
EDL is the core of SGX programming, which defines all Functions for reading, writing, and processing data in the circle. During the compilation phase, the Edger8r tool provided by the SDK will generate the bridging function between the encirclement and ordinary memory based on the functions defined in the EDL, and perform corresponding security detection.
Functions are divided into trusted functions (ecall) and untrusted functions (ocall):
ecall: defined in the trusted area (trusted), called outside the circle, and within the circle implement.
ocall: defined in the untrusted area (untrusted), called within the circle, and executed outside the circle.
// demo.edl
enclave {
// Add your definition of "secret_t" here
trusted {
public void get_secret([out] secret_t* secret);
};
untrusted {
// This OCALL is for illustration purposes only.
// It should not be used in a real enclave,
// unless it is during the development phase
// for debugging purposes.
void dump_secret([in] const secret_t* secret);
};
};Installing SGX
You can install SGX through the installation file or source code, including drivers, PSW and SDK, etc. Both installation methods require the installation of header files corresponding to the Linux kernel version.
The above is the detailed content of How can the CPU protect your data and privacy from being stolen by malicious code? Basic introduction to Intel SGX. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to start apache
Apr 13, 2025 pm 01:06 PM
How to start apache
Apr 13, 2025 pm 01:06 PM
The steps to start Apache are as follows: Install Apache (command: sudo apt-get install apache2 or download it from the official website) Start Apache (Linux: sudo systemctl start apache2; Windows: Right-click the "Apache2.4" service and select "Start") Check whether it has been started (Linux: sudo systemctl status apache2; Windows: Check the status of the "Apache2.4" service in the service manager) Enable boot automatically (optional, Linux: sudo systemctl
 What to do if the apache80 port is occupied
Apr 13, 2025 pm 01:24 PM
What to do if the apache80 port is occupied
Apr 13, 2025 pm 01:24 PM
When the Apache 80 port is occupied, the solution is as follows: find out the process that occupies the port and close it. Check the firewall settings to make sure Apache is not blocked. If the above method does not work, please reconfigure Apache to use a different port. Restart the Apache service.
 How to restart the apache server
Apr 13, 2025 pm 01:12 PM
How to restart the apache server
Apr 13, 2025 pm 01:12 PM
To restart the Apache server, follow these steps: Linux/macOS: Run sudo systemctl restart apache2. Windows: Run net stop Apache2.4 and then net start Apache2.4. Run netstat -a | findstr 80 to check the server status.
 How to learn Debian syslog
Apr 13, 2025 am 11:51 AM
How to learn Debian syslog
Apr 13, 2025 am 11:51 AM
This guide will guide you to learn how to use Syslog in Debian systems. Syslog is a key service in Linux systems for logging system and application log messages. It helps administrators monitor and analyze system activity to quickly identify and resolve problems. 1. Basic knowledge of Syslog The core functions of Syslog include: centrally collecting and managing log messages; supporting multiple log output formats and target locations (such as files or networks); providing real-time log viewing and filtering functions. 2. Install and configure Syslog (using Rsyslog) The Debian system uses Rsyslog by default. You can install it with the following command: sudoaptupdatesud
 How to solve the problem that apache cannot be started
Apr 13, 2025 pm 01:21 PM
How to solve the problem that apache cannot be started
Apr 13, 2025 pm 01:21 PM
Apache cannot start because the following reasons may be: Configuration file syntax error. Conflict with other application ports. Permissions issue. Out of memory. Process deadlock. Daemon failure. SELinux permissions issues. Firewall problem. Software conflict.
 Does the internet run on Linux?
Apr 14, 2025 am 12:03 AM
Does the internet run on Linux?
Apr 14, 2025 am 12:03 AM
The Internet does not rely on a single operating system, but Linux plays an important role in it. Linux is widely used in servers and network devices and is popular for its stability, security and scalability.
 How to fix apache vulnerability
Apr 13, 2025 pm 12:54 PM
How to fix apache vulnerability
Apr 13, 2025 pm 12:54 PM
Steps to fix the Apache vulnerability include: 1. Determine the affected version; 2. Apply security updates; 3. Restart Apache; 4. Verify the fix; 5. Enable security features.
 How to start nginx in Linux
Apr 14, 2025 pm 12:51 PM
How to start nginx in Linux
Apr 14, 2025 pm 12:51 PM
Steps to start Nginx in Linux: Check whether Nginx is installed. Use systemctl start nginx to start the Nginx service. Use systemctl enable nginx to enable automatic startup of Nginx at system startup. Use systemctl status nginx to verify that the startup is successful. Visit http://localhost in a web browser to view the default welcome page.



