 Daily Programming
Daily Programming
 Mysql Knowledge
Mysql Knowledge
 How to create foreign keys in mysql database? (Pictures + Videos)
How to create foreign keys in mysql database? (Pictures + Videos)
How to create foreign keys in mysql database? (Pictures + Videos)
This article mainly introduces how to create foreign keys in mysql database.
Regarding the basic introduction of foreign keys in mysql database, we provide this article [What are Mysql foreign keys? What are the uses? ], I have already introduced it to you, friends who need it can choose to refer to it.
Understanding the basic definition of foreign keys, how do we create foreign keys?
Below we will introduce to you through a simple example how to create a mysql foreign key.
First we can open the management tool through the cmd command and log in to the mysql database.
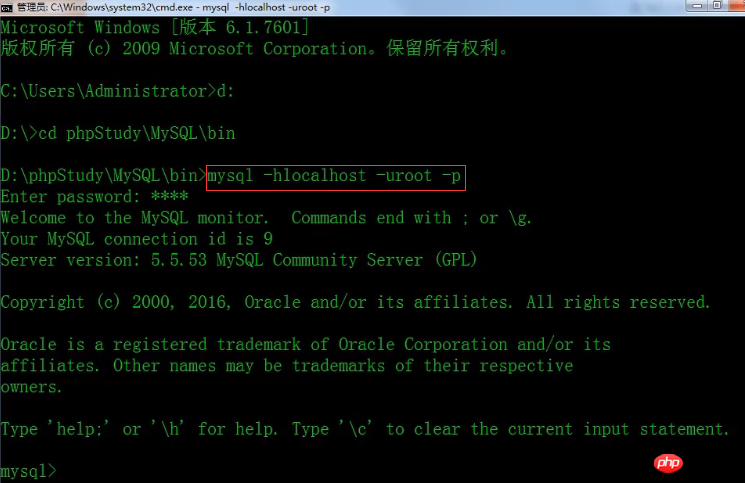
Then query the database through the show database statement.
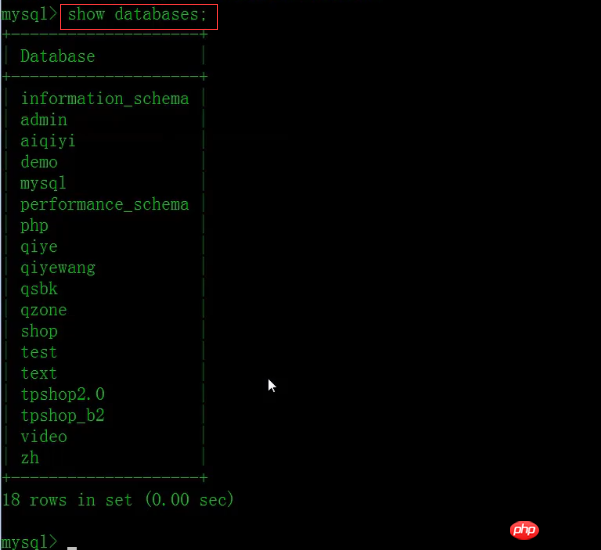
Then use test database and execute the following SQL statement written by ourselves. Here we create a data table stu1 and add a foreign key to the c_id field so that it can be associated with the class id.
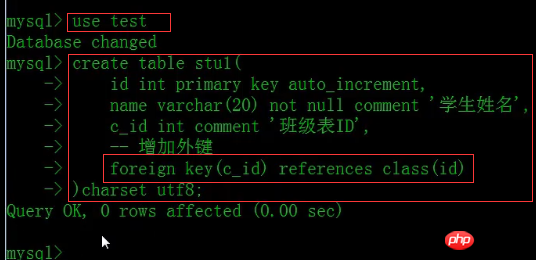
#We can check whether the data table stu1 is created successfully.
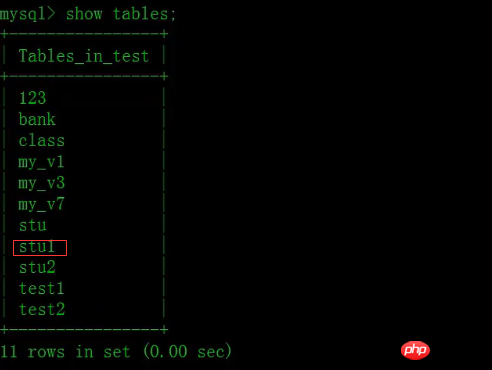
Finally, we can query the table structure or table information through the "show create table stu1" statement to see whether the foreign key is successfully created.
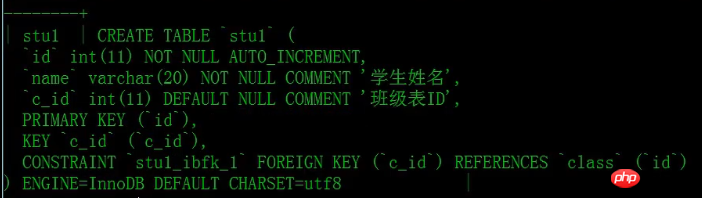
The picture shows that the foreign key has been successfully created.
Note: Only the InnoDB storage engine supports creating foreign keys!
This article is an introduction to how to create foreign keys in mysql database. It is simple and easy to understand. I hope it will be helpful to friends in need!
If you want to know more about mysql, you can follow the PHP Chinese website mysql video tutorial, everyone is welcome to refer to and learn!
The above is the detailed content of How to create foreign keys in mysql database? (Pictures + Videos). For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1385
1385
 52
52
 What are stored procedures and functions in MySQL?
Mar 20, 2025 pm 03:04 PM
What are stored procedures and functions in MySQL?
Mar 20, 2025 pm 03:04 PM
The article discusses stored procedures and functions in MySQL, focusing on their definitions, performance benefits, and usage scenarios. Key differences include return values and invocation methods.
 How do you secure your MySQL server against unauthorized access?
Mar 20, 2025 pm 03:20 PM
How do you secure your MySQL server against unauthorized access?
Mar 20, 2025 pm 03:20 PM
The article discusses securing MySQL servers against unauthorized access through password management, limiting remote access, using encryption, and regular updates. It also covers monitoring and detecting suspicious activities to enhance security.
 How do you use roles to manage user permissions?
Mar 20, 2025 pm 03:19 PM
How do you use roles to manage user permissions?
Mar 20, 2025 pm 03:19 PM
The article discusses using roles to manage user permissions efficiently, detailing role definition, permission assignment, and dynamic adjustments. It emphasizes best practices for role-based access control and how roles simplify user management acr
 How do you set passwords for user accounts in MySQL?
Mar 20, 2025 pm 03:18 PM
How do you set passwords for user accounts in MySQL?
Mar 20, 2025 pm 03:18 PM
The article discusses methods for setting and securing MySQL user account passwords, best practices for password security, remote password changes, and ensuring compliance with password policies.
 How do you grant permissions to execute stored procedures and functions?
Mar 20, 2025 pm 03:12 PM
How do you grant permissions to execute stored procedures and functions?
Mar 20, 2025 pm 03:12 PM
Article discusses granting execute permissions on stored procedures and functions, focusing on SQL commands and best practices for secure, multi-user database management.
 How do you grant privileges to a user using the GRANT statement?
Mar 20, 2025 pm 03:15 PM
How do you grant privileges to a user using the GRANT statement?
Mar 20, 2025 pm 03:15 PM
The article explains the use of the GRANT statement in SQL to assign various privileges like SELECT, INSERT, and UPDATE to users or roles on specific database objects. It also covers revoking privileges with the REVOKE statement and granting privileg
 How do you use variables in stored procedures and functions?
Mar 20, 2025 pm 03:08 PM
How do you use variables in stored procedures and functions?
Mar 20, 2025 pm 03:08 PM
The article discusses using variables in SQL stored procedures and functions to enhance flexibility and reusability, detailing declaration, assignment, usage, scope, and output. It also covers best practices and common pitfalls to avoid when using va
 What are the different types of privileges in MySQL?
Mar 20, 2025 pm 03:16 PM
What are the different types of privileges in MySQL?
Mar 20, 2025 pm 03:16 PM
Article discusses MySQL privileges: global, database, table, column, routine, and proxy user types. It explains granting, revoking privileges, and best practices for secure management. Over-privileging risks are highlighted.



