Introduction to css: What do css grammar rules consist of?
When many people just get started with CSS, they don’t quite understand the rules of CSS grammar, and they don’t know what the rules of CSS grammar consist of. Let’s explain what the rules of CSS grammar consist of?
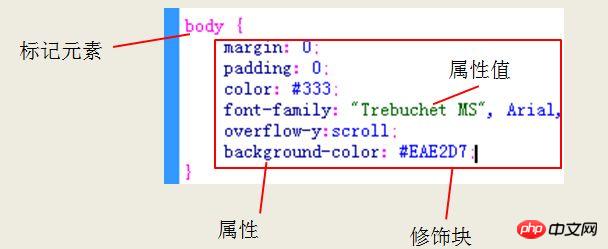
css is mainly composed of two parts. The first is the selector, and the second is the statement. The statement may be one or many, and the css selector is When we change the style of html, each statement consists of an attribute and a value. The main syntax of css is:
selector {declaration1; declaration2; ... declarationN }Below we can use a case to illustrate the rules of css:
h1 {color:red; font-size:16px;}In the above code, h1 represents the selector, and the statement inside the curly braces is the attribute. and value, where color is the attribute of css, and red is the value. There are several ways to write the value. We know that there are several ways to write red. We can also use hexadecimal #ff0000 to express it. Of course we want to use Less bytes can also be represented by CSS abbreviations. Sometimes we can also use RGB percentages. When using percentages, we have to write the percentage symbol.
The most important thing about css is multiple declarations. If we want to define several declarations, we can use the declaration symbols to separate them. The last attribute does not need to be added with a semicolon. The semicolon in English is A separator symbol is not an end symbol, but many experienced people like to add a separator symbol. This may reduce our chances of making mistakes. For example:
p {
text-align: center;
color: black;
font-family: arial;
}Finally we must pay attention to spaces and case. Many styles have more than one statement, so no spaces should appear. If css involves working with html, the class in css is very sensitive.
The above is a complete introduction to getting started with css: what css grammar rules consist of. If you want to know more about CSS tutorial and CSS3 tutorial, please pay attention to php Chinese website.
The above is the detailed content of Introduction to css: What do css grammar rules consist of?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Rules and exceptions for pointer comparisons?
Jun 04, 2024 pm 06:01 PM
Rules and exceptions for pointer comparisons?
Jun 04, 2024 pm 06:01 PM
In C/C++, the pointer comparison rules are as follows: pointers pointing to the same object are equal. Pointers to different objects are not equal. Exception: Pointers to null addresses are equal.
 Naming conventions and rules for PHP functions
May 19, 2023 am 08:14 AM
Naming conventions and rules for PHP functions
May 19, 2023 am 08:14 AM
As a very popular scripting language, PHP has powerful function library support. Its function naming conventions and rules have an important impact on development efficiency and code readability. This article will introduce the naming conventions and rules of PHP functions. 1. Naming style In PHP, function names need to strictly comply with naming specifications and rules. The specifications mainly include two aspects: naming style and naming rules. 1. Underline nomenclature Underline nomenclature is the most commonly used way to name PHP functions and is also an officially recommended way. Function names that follow this pattern
 A deep dive into the definition and specification of Python identifiers
Dec 29, 2023 am 08:34 AM
A deep dive into the definition and specification of Python identifiers
Dec 29, 2023 am 08:34 AM
An in-depth understanding of the definitions and rules of Python identifiers requires specific code examples. Python is a concise and powerful programming language with a wide range of applications. In Python programming, identifiers play a vital role. This article will delve into the definition and rules of Python identifiers and provide specific code examples to help readers better understand and apply them. First, let’s understand the definition of Python identifiers. In Python, an identifier can be the name of a variable, function, class, module, etc.
 Analyze the components of a Linux process
Mar 21, 2024 am 10:12 AM
Analyze the components of a Linux process
Mar 21, 2024 am 10:12 AM
Components and code examples of Linux processes In Linux systems, processes are one of the most important concepts in the operating system. Understanding the components of a process is critical to a deep understanding of how an operating system works. This article will introduce the components of the Linux process, including process control block (PCB), process identifier (PID), process status, process address space, etc., and provide specific code examples to help readers better understand. Process Control Block (PCB) The process control block is used in the operating system kernel to maintain process information.
 Linux firewall-iptables detailed explanation
Feb 20, 2024 am 11:57 AM
Linux firewall-iptables detailed explanation
Feb 20, 2024 am 11:57 AM
Project introduction iptables is a free packet filtering firewall software under Linux system, which can realize packet filtering, packet redirection and network address translation and other functions. It is an efficient and flexible solution that replaces expensive commercial firewalls. iptables has powerful configuration options and rule settings, allowing users to finely control network traffic according to their own needs and improve network security and performance. The rules of iptables actually refer to the conditions predefined by the network administrator. The rules are generally defined as "If the data packet header meets such conditions, process the data packet in this way." The rules are stored in the packet filtering table in the kernel space. These rules respectively specify the source address, destination address, transmission protocol (such as TCP, U
 Detailed explanation of the representation methods and rules of character constants in various programming languages
Dec 27, 2023 am 11:56 AM
Detailed explanation of the representation methods and rules of character constants in various programming languages
Dec 27, 2023 am 11:56 AM
How are character constants represented in different programming languages? Introduction: In the programming process, character constants are immutable values that represent a single character. Different programming languages have different ways of representing character constants. This article will introduce the ways to represent character constants in several common programming languages and give specific code examples. 1. C language represents character constants: In C language, character constants are represented by single quotes ('). Here are some examples: Representing a character: chach='a'; Representing an escape character: cha
 Detailed explanation of ZKSync airdrop rules: How are ZK tokens distributed? Who is eligible?
Jun 14, 2024 pm 10:13 PM
Detailed explanation of ZKSync airdrop rules: How are ZK tokens distributed? Who is eligible?
Jun 14, 2024 pm 10:13 PM
Detailed explanation of ZKSync airdrop rules: How are ZK tokens distributed? Who is eligible? The much-anticipated ZKsync airdrop distribution plan has been finalized. The ZKsync Association will conduct a one-time airdrop of 3.6 billion ZK tokens to early ZKsync users and adopters next week, with 695,232 eligible wallets. The snapshot is on March 24, and community members can check airdrop eligibility on the Claim.zknation.io website and claim airdrops starting next week until January 3, 2025. This airdrop represents 17.5% of the total supply of ZK tokens. Users will be able to claim their tokens starting next week until January 3, 2025. Contributors can claim it starting from June 24th. Who is eligible for
 AI Contract Theory ⑤: Generative AI is racing with thousands of sails, how to use rules to 'steer'
Jun 02, 2023 pm 08:21 PM
AI Contract Theory ⑤: Generative AI is racing with thousands of sails, how to use rules to 'steer'
Jun 02, 2023 pm 08:21 PM
21st Century Business Herald reporter Cai Shuyue, Guo Meiting, intern Tan Yanwen, Mai Zihao, reporting from Shanghai and Guangzhou Editor's note: In the past few months of 2023, major companies have rushed to seize large models, explore the commercialization of GPT, and the computing infrastructure has been bullish... Just like 15 In the Age of Discovery that opened in the 20th century, human exchanges, trade, and wealth experienced explosive growth, and the space revolution swept the world. At the same time, change also brings challenges to order, such as data leakage, personal privacy risks, copyright infringement, false information... In addition, the post-humanist crisis brought by AI is already on the table. What attitude should people take? Are you facing the myths caused by the mixture of humans and machines? At this moment, seeking consensus on AI governance and reshaping a new order have become issues faced by all countries. Nancai Compliance Technology Research Institute will launch AI




