What does port scanning mean?
Since the ports on your computer are where information is sent and received, port scanning is similar to knocking on the door to see if anyone is home. Now let’s take you through port scanning, hoping it will be helpful to you.

Port scanning
Port scanning is used to identify open ports and services available on network hosts The name of a technology that checks all ports on an IP address to see if they are open or closed.
Security technicians sometimes use it to audit computers for vulnerabilities, but hackers also use it to attack their victims. It is considered an open hacking technique where hackers perform port scanning techniques to find vulnerabilities within specific computer ports. To an intruder, these weaknesses represent opportunities for attack.
There are 65,535 ports in each IP address, and hackers may scan each port to find any unsecured ports.
How does port scanning work?
Port scanning is very simple: send a request to connect to the target computer, and then keep track of which ports appear to be open or which respond to the request.
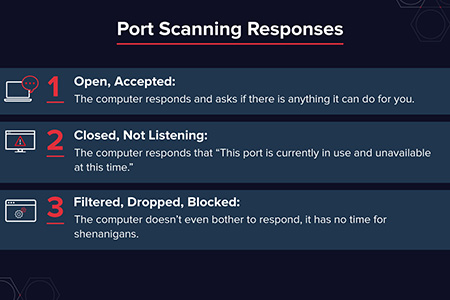
There are three possible responses:
1. Open, Accept: The computer responds and asks if there is anything it can do for you. things.
2. Closed, not listening: The computer responds "This port is currently in use and unavailable at this time."
3. Filter, discard, block: The computer doesn't even bother to respond, it doesn't have time for pranks.
Types of port scans
Ping scan:
The simplest port Scanning technology used to scan entire network blocks or individual targets to identify which computers on the network are active. It sends an ICMP echo request to the target, and if the response is an ICMP reply, it means the target is active.
vanilla scan:
The most basic type of scan, the scanner will try to connect to all 65,535 ports. It is a full connection scan, which sends the SYN flag (requesting a connection), and after receiving the SYN-ACK (connection confirmation) response, sends back the ACK flag. Full connection scans are accurate but very easy to detect because the firewall always logs full connections.
SYN Scan: Also known as Half-Open Scan (TCP Half-Open)
This is a quick and sneaky scan that attempts to find potentially open scans on the target computer port. This scan is fast because it never completes the full TCP 3-way handshake. The scanner sends a SYN message and only records the SYN-ACK response. The scanner does not complete the connection by sending a final ACK: it leaves the target dangling.
strobe scan: A more focused scan that only looks for known developed services
UDP: The scanner looks for open UDP Port
FTP Bounce Scanning: The scanner masquerades the scan source through an FTP server, allowing packets to be bounced through the FTP server to masquerade the sender's location.
Stealth Scan: Used to collect information without being logged by the target system, the scanner prevents the scanned computer from logging port scan activity.
Summary: Port scanning is the first step in any vulnerability analysis or penetration testing; knowing which ports are open is the beginning of being able to actively communicate with the target. Port scanning itself does not constitute a crime. We can protect port scanning through the use of firewalls.
This article ends here. I hope it will be helpful to everyone's study. For more exciting content, you can pay attention to the relevant tutorial columns of the PHP Chinese website! ! !
The above is the detailed content of What does port scanning mean?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Using Netty4 for TCP communication in Java API development
Jun 17, 2023 pm 11:18 PM
Using Netty4 for TCP communication in Java API development
Jun 17, 2023 pm 11:18 PM
TCP is a type of computer network communication protocol and a connection-oriented transmission protocol. In Java application development, TCP communication is widely used in various scenarios, such as data transmission between client and server, real-time transmission of audio and video, etc. Netty4 is a high-performance, highly scalable, and high-performance network programming framework that can optimize the data exchange process between the server and the client to make it more efficient and reliable. The specific implementation steps of using Netty4 for TCP communication are as follows: Introduction
 How to reset tcp/ip protocol in win10? How to reset the tcp/ip protocol stack in windows 10
Mar 16, 2024 am 11:07 AM
How to reset tcp/ip protocol in win10? How to reset the tcp/ip protocol stack in windows 10
Mar 16, 2024 am 11:07 AM
How to reset tcp/ip protocol in win10? In fact, the method is very simple. Users can directly enter the command prompt, and then press the ctrl shift enter key combination to perform the operation, or directly execute the reset command to set it up. Let this site do the following. Let us carefully introduce to users how to reset the TCP/IP protocol stack in Windows 10. Method 1 to reset the tcp/ip protocol stack in Windows 10. Administrator permissions 1. We use the shortcut key win R to directly open the run window, then enter cmd and hold down the ctrl shift enter key combination. 2. Or we can directly search for command prompt in the start menu and right-click
 How to use TCP to implement conversation between client and server in python
May 17, 2023 pm 03:40 PM
How to use TCP to implement conversation between client and server in python
May 17, 2023 pm 03:40 PM
TCP client A client sample code that uses the TCP protocol to achieve continuous dialogue: importsocket#Client configuration HOST='localhost'PORT=12345#Create a TCP socket and connect to the server client_socket=socket.socket(socket.AF_INET,socket .SOCK_STREAM)client_socket.connect((HOST,PORT))whileTrue:#Get user input message=input("Please enter the message to be sent:&
 See you soon! TCP waves twice, have you seen it? What about the four handshakes?
Jul 24, 2023 pm 05:18 PM
See you soon! TCP waves twice, have you seen it? What about the four handshakes?
Jul 24, 2023 pm 05:18 PM
The "connection-oriented" mentioned here means that you need to establish a connection, use the connection, and release the connection. Establishing a connection refers to the well-known TCP three-way handshake. When using a connection, data is transmitted in the form of one send and one confirmation. There is also the release of the connection, which is our common TCP four wave waves.
 How to send multiple files using a single TCP connection in Java?
Apr 27, 2023 am 08:49 AM
How to send multiple files using a single TCP connection in Java?
Apr 27, 2023 am 08:49 AM
Why is there this blog about using one TCP connection to send multiple files? I have been reading some related things recently. There is no problem in simply using Socket for programming, but this only establishes some basic concepts. Still nothing can be done about the real problem. When I need to transfer files, I find that I seem to have just sent the data (binary data), but some information about the file is lost (the file extension). And each time I can only use one Socket to send one file, there is no way to send files continuously (because I rely on closing the stream to complete sending files, which means that I actually don’t know the length of the file, so I can only send files as one Socket connection represents a file).
 Linux SIGPIPE signal
Feb 19, 2024 pm 04:00 PM
Linux SIGPIPE signal
Feb 19, 2024 pm 04:00 PM
Among the TCP communication parties, for the convenience of description, the communication parties are replaced by A and B in the following. According to the TCP protocol, if B continues to send data after A closes the connection, B will receive A's RST response. If B continues to send data, the system will send a SIGPIPE signal to inform that the connection has been disconnected and stop sending. The system's default processing behavior for the SIGPIPE signal is to let process B exit. The default processing behavior of the operating system for the SIGPIPE signal is very unfriendly. Let us analyze it. TCP communication is a full-duplex channel, which is equivalent to two simplex channels, and each end of the connection is responsible for one. When the opposite end "closes", although the intention is to close the entire two channels, the local end only receives the FIN packet. According to the provisions of the TCP protocol, when a
 What is the difference between tcp and ip
Sep 04, 2023 pm 02:19 PM
What is the difference between tcp and ip
Sep 04, 2023 pm 02:19 PM
TCP and IP are two different protocols in the Internet: 1. TCP is a transport layer protocol, while IP is a network layer protocol; 2. TCP provides functions such as segmentation, sorting, confirmation and retransmission of data packets. , and the IP protocol is responsible for providing source and destination addresses for data packets; 3. TCP is a connection-oriented protocol, while the IP protocol is connectionless; 4. TCP also provides flow control and congestion control.
 How to use Nginx to protect against port scanning attacks
Jun 10, 2023 pm 12:18 PM
How to use Nginx to protect against port scanning attacks
Jun 10, 2023 pm 12:18 PM
In the current Internet environment, security has always been one of the most concerning issues for network administrators and website developers. Among them, port scanning attacks are a common security vulnerability. Attackers scan open ports on a website to identify potential vulnerabilities. In order to avoid security threats caused by port scanning attacks, more and more enterprises and websites choose to use Nginx as their web server. This article will introduce how to use Nginx to prevent port scanning attacks. 1. What is a port scanning attack? Port scanning refers to an attacker using TCP or U






