
This article brings you what is hotlinking? How to forge Referer in PHP to request anti-leeching resources (with examples), it has certain reference value, friends in need can refer to it, I hope it will be helpful to you.
Some products will adopt anti-leeching measures in order to prevent their products from being accessed by stolen links, such as closed ecological music websites and video websites. They have already paid for copyrights, so naturally they don’t want you to use their products for free. resource. But because many people specialize in hotlinking, we also need to understand the principles of hotlinking, anti-hotlinking, and evasion of anti-hotlinking.
Hot links
Quoting Baidu Encyclopedia’s definition of hot links:
Hot links refer to content that the service provider itself does not provide services through Technical means bypass other beneficial end-user interfaces (such as advertisements), directly provide end-users with service content of other service providers on their own websites, and defraud end-users' browsing and click-through rates. The beneficiary provides no or very few resources, while the real service provider receives no benefit.
Conventional hotlinks
We know that the website provides services by requesting an html file from the server. This file contains css/js files and img/ video tag, these static resources will initiate requests in sequence and fill in the specified location when the html file is loaded, thus completing the loading of the entire page.
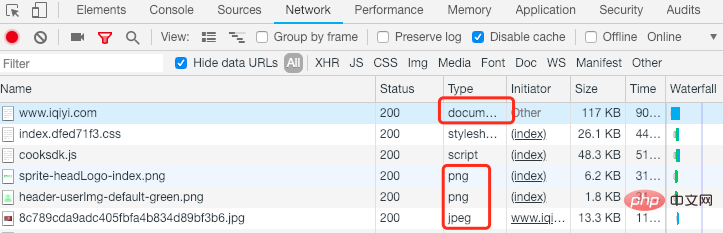
So as long as we get the URL of this image and embed it in our own html file, we can access it on our website, because the resources are accessed independently by different HTTP requests , so we can also filter the html files of the origin site. This is the simplest hotlinking.
Hazard: When the user visits, he is not accessing the stolen link website, but it will still occupy the bandwidth resources of the website, and the operator must pay for the bandwidth. At the same time, the website’s advertising, peripherals, publicity and other resources will not be accessed by users.
Distributed hotlinking
Distributed hotlinking is more complicated and requires special programs to be deployed on the server. It is not aimed at a single website or a single URL, but for All useful resources on the entire network are stolen and stored in its own database, and when the user actually accesses it, it is completely converted into its own traffic.
Hazards: The resources you obtain through labor, money, and copyright payment can be used for free by stolen link websites, such as online store photos, periodicals, TV series, etc. As a result, their members and services cannot be profitable.
Anti-hotlinking classification
After we understand the harm of hotlinking to the origin site, we naturally need to use some means to prevent this behavior and safeguard our own interests.
Add watermark
This is the simplest method. Use the back-end program to add watermarks to pictures and other resources in batches. This way, while hotlinking, it also provides To promote their own websites, they may even actively seek such hotlinks.
Resource renaming
Because the hot link is through the specified url, this url must contain the path and name of the resource, so by changing the file from time to time or The name of the directory can quickly avoid hot links, but it will also cause the resources being downloaded to be interrupted.
Limit reference page
In the header information of the http request, there is a field: referer, which represents which page the request is initiated from, if it is a separate If it is opened in the page or requested by the server, this field will be empty. Therefore, we can set restrictions through the value of the referer field. If it is a page that we recognize, the resource will be returned. Otherwise, the request will be prohibited. However, since a whitelisted file must be opened every time for URL matching, performance will be reduced.
Encryption Authentication
The client encrypts the user authentication information by combining it with the name of the resource, and uses the encrypted string as a parameter of the URL to initiate a request. The requested resource will be returned only after the server decrypts and authenticates it. This method is mainly used to prevent distributed hot links.
Anti-hotlinking program
Of the above three anti-hotlinking methods, we commonly use the third one, which uses the referer attribute to complete anti-hotlinking. Today, we also Mainly share this method of anti-leeching and anti-leeching.
Backend Program Limitation
This kind of limitation consumes server-side computing resources, so it is not as commonly used as Nginx limitation.
$from = parse_url($_SERVER['HTTP_REFERER']);
if ($from['host']!='xxx.com' && $from['host']!='www.xxx.com') {
die('你丫在盗链');
}Nginx Limitation
This can be done by modifying the nginx configuration file. Remember to restart nginx after the modification is completed:
// 这里指定需要防盗链的资源,如gif/jpg等
location ~* \.(gif|jpg|png|jpeg)$ {
// 设置资源的过期时间
expires 30d;
// 设置合法的引用页,也就是防盗链的白名单;
// none blocked保证用户在新页面打开时依然能够打开,如果不希望用户能够保存删掉这两项
valid_referers none blocked *.hugao8.com *.baidu.com *.google.com;
// 对于非法的引用页,可以重写图片,也可以直接返回403或404页面
if ($invalid_referer) {
rewrite ^/http://www.it300.com/static/images/404.jpg;
#return 404;
}
}Referer-Policy
Referer 首部包含了当前请求页面的来源页面的地址,即表示当前页面是通过此来源页面里的链接进入的。服务端一般使用 Referer 首部识别访问来源,可能会以此进行统计分析、日志记录以及缓存优化等。
Referer属性出现在请求头中,也在请求头中被设置,但是在浏览器的安全策略里,该值无法被js所指定:
$.ajax({
url: 'http://www.baidu.com',
beforeSend(xhr) {
// 在发送ajax请求前设置header头部
xhr.setRequestHeader("Referer", "http://translate.google.com/");
xhr.setRequestHeader("User-Agent", "stagefright/1.2 (Linux;Android 5.0)");
},
success(data) {
console.log(data);
},
error(err) {
console.log(err);
}
});然而浏览器会报错:
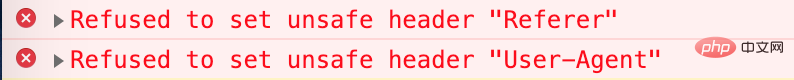
<meta> <a> </a><a></a>
防反盗链
前端JS不能在头部设置Referer字段,和跨域一样是因为浏览器的安全策略,那么同样的在服务端进行请求就不会有这些限制,我们在服务端请求时就可以自由的修改Referer字段。
我们通过简单的PHP例子来完成这个功能:
<?php $url = 'http://t11.baidu.com/it/u=3008889497,862090385&fm=77';
$refer = 'https://www.baidu.com';
$ch = curl_init();
//以url的形式 进行请求
curl_setopt($ch, CURLOPT_URL, $url);
//以文件流的形式 进行返回 不直接输出到浏览器
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
//浏览器发起请求 超时设置
curl_setopt($ch, CURLOPT_CONNECTTIMEOUT, 30);
//伪造来源地址
curl_setopt ($ch, CURLOPT_REFERER, $refer);
$file = curl_exec($ch);
curl_close($ch);
header('Content-Type: text/html');
// 对图片进行base64编码,然后返回给前端展示
$file = base64_encode($file);
echo "<img src="/static/imghw/default1.png" data-src="https://img.php.cn/upload/image/896/819/432/1548469206662260.png" class="lazy" src='data:image/jpeg;base64,{$file}' / alt="What is hotlinking? How to forge Referer in PHP to request anti-leeching resources (with example)" >";
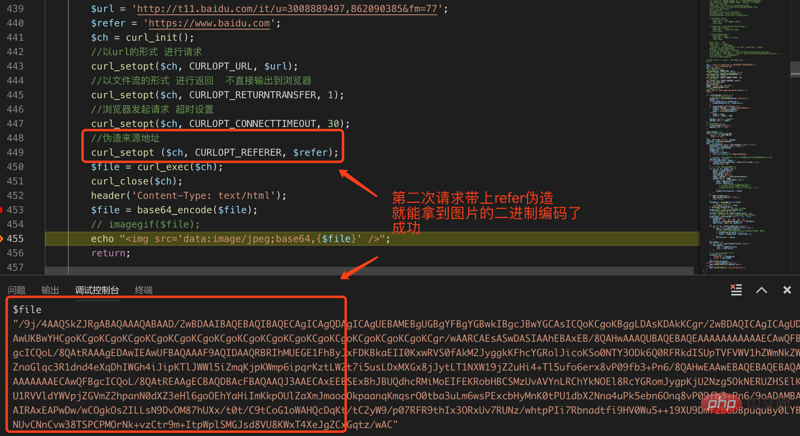
?>我们第一次请求注释了伪造来源地址这一行,第二次请求不注释这一行,这样可以验证执行结果: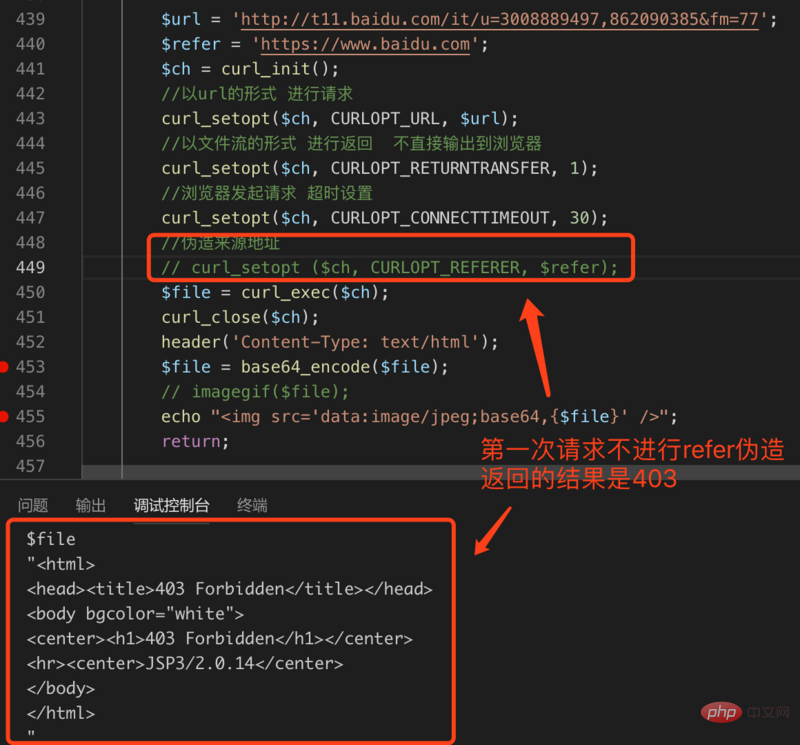
总结
盗链和反盗链是一个对立面,技术不断升级,最终的目标也是为了开放资源和保护知识产权。在互联网生态里,我们通过反盗链保护我们的利益,也使用防反盗链的这种方式来扩大我们的内容,无论站在哪一方,都需要做到知己知彼。
The above is the detailed content of What is hotlinking? How to forge Referer in PHP to request anti-leeching resources (with example). For more information, please follow other related articles on the PHP Chinese website!



