 Backend Development
Backend Development
 Python Tutorial
Python Tutorial
 Introduction to the method of Python simulating Weibo login (with code)
Introduction to the method of Python simulating Weibo login (with code)
Introduction to the method of Python simulating Weibo login (with code)
This article brings you an introduction to the method of simulating Weibo login in Python (with code). It has certain reference value. Friends in need can refer to it. I hope it will be helpful to you. Helps.
Today I want to make a tool for crawling personal pages on Weibo to satisfy some ulterior secrets. Then do that must-do thing first! Simulated login...
I optimized the code, refactored it into Python 3.6 version, and added a lot of comments to facilitate everyone's learning.
When logging in to Sina Weibo on PC, the user name and password are pre-encrypted using js on the client, and a set of parameters will be GET before POST, which will also be used as part of POST_DATA. In this way, you cannot use the usual simple method to simulate POST login (such as Renren).
1. Before submitting the POST request, you need to obtain two parameters through GET.
The address is:
http://login.sina.com.cn/sso/login.php?client=ssologin.js(v1.3.18)
In the obtained data There are servertime and nonce values, which are random, and other values seem to be of no use.
def get_servertime():
url = 'http://login.sina.com.cn/sso/prelogin.php?entry=weibo&callback=sinaSSOController.preloginCallBack&su=dW5kZWZpbmVk&client=ssologin.js(v1.3.18)&_=1329806375939'
# 返回出来的是一个Response对象,无法直接获取,text后,可以通过正则匹配到
# 大概长这样子的:sinaSSOController.preloginCallBack({"retcode":0,"servertime":1545606770, ...})
data = requests.request('GET', url).text
p = re.compile('\((.*)\)')
try:
json_data = p.search(data).group(1)
data = json.loads(json_data)
servertime = str(data['servertime'])
nonce = data['nonce']
return servertime, nonce
except:
print('获取 severtime 失败!')
return None2. Observe the POST data through httpfox. The parameters are more complex, where "su" is the encrypted username, and sp is the encrypted password. servertime and nonce are obtained from the previous step. Other parameters are unchanged.
username has been calculated by BASE64:
username = base64.encodestring( urllib.quote(username) )[:-1]
password has been SHA1 encrypted three times, and the values of servertime and nonce have been added to interfere.
That is: After SHA1 encryption twice, add the servertime and nonce values to the result, and then SHA1 is calculated again.
def get_pwd(pwd, servertime, nonce): # 第一次计算,注意Python3 的加密需要encode,使用bytes pwd1 = hashlib.sha1(pwd.encode()).hexdigest() # 使用pwd1的结果在计算第二次 pwd2 = hashlib.sha1(pwd1.encode()).hexdigest() # 使用第二次的结果再加上之前计算好的servertime和nonce值,hash一次 pwd3_ = pwd2 + servertime + nonce pwd3 = hashlib.sha1(pwd3_.encode()).hexdigest() return pwd3 def get_user(username): # 将@符号转换成url中能够识别的字符 _username = urllib.request.quote(username) # Python3中的base64计算也是要字节 # base64出来后,最后有一个换行符,所以用了切片去了最后一个字符 username = base64.encodebytes(_username.encode())[:-1] return username
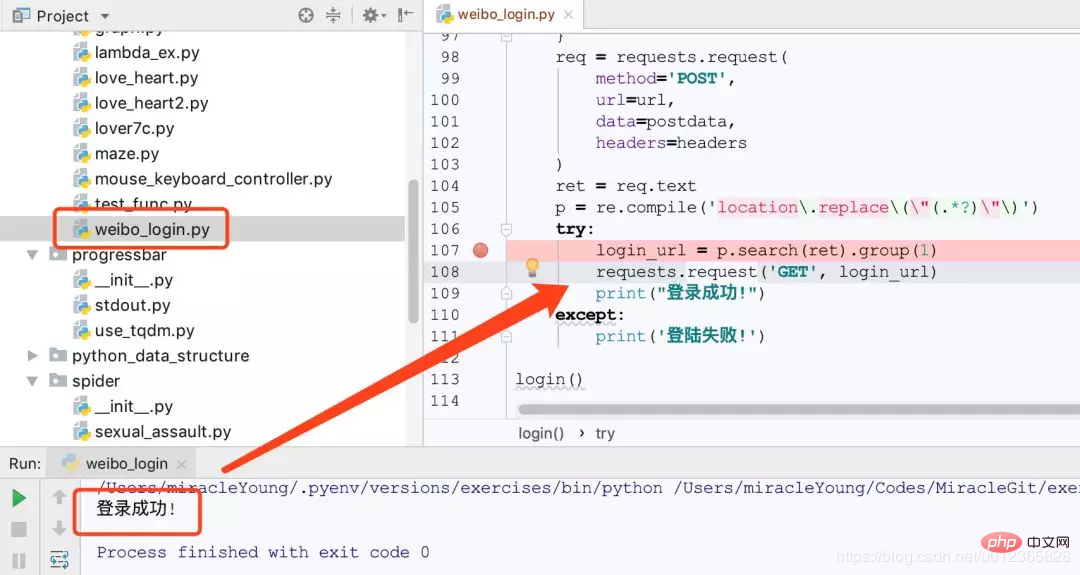
3. Organize the parameters and make a POST request. There has been no successful login since then.
The content obtained after POST contains the sentence:
location.replace("http://weibo.com/ajaxlogin.php?framelogin=1&callback=parent.sinaSSOController.feedBackUrlCallBack&retcode=101&reason=%B5%C7%C2%BC%C3%FB%BB%F2%C3%DC%C2%EB%B4%ED%CE%F3")This is the result when the login fails. The result after the login is successful is similar, but the value of retcode is 0.
Next, request this URL again, and you will successfully log in to Weibo.
Remember to build the cache in advance.
The above is the detailed content of Introduction to the method of Python simulating Weibo login (with code). For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Google AI announces Gemini 1.5 Pro and Gemma 2 for developers
Jul 01, 2024 am 07:22 AM
Google AI announces Gemini 1.5 Pro and Gemma 2 for developers
Jul 01, 2024 am 07:22 AM
Google AI has started to provide developers with access to extended context windows and cost-saving features, starting with the Gemini 1.5 Pro large language model (LLM). Previously available through a waitlist, the full 2 million token context windo
 How to download deepseek Xiaomi
Feb 19, 2025 pm 05:27 PM
How to download deepseek Xiaomi
Feb 19, 2025 pm 05:27 PM
How to download DeepSeek Xiaomi? Search for "DeepSeek" in the Xiaomi App Store. If it is not found, continue to step 2. Identify your needs (search files, data analysis), and find the corresponding tools (such as file managers, data analysis software) that include DeepSeek functions.
 How do you ask him deepseek
Feb 19, 2025 pm 04:42 PM
How do you ask him deepseek
Feb 19, 2025 pm 04:42 PM
The key to using DeepSeek effectively is to ask questions clearly: express the questions directly and specifically. Provide specific details and background information. For complex inquiries, multiple angles and refute opinions are included. Focus on specific aspects, such as performance bottlenecks in code. Keep a critical thinking about the answers you get and make judgments based on your expertise.
 How to search deepseek
Feb 19, 2025 pm 05:18 PM
How to search deepseek
Feb 19, 2025 pm 05:18 PM
Just use the search function that comes with DeepSeek. Its powerful semantic analysis algorithm can accurately understand the search intention and provide relevant information. However, for searches that are unpopular, latest information or problems that need to be considered, it is necessary to adjust keywords or use more specific descriptions, combine them with other real-time information sources, and understand that DeepSeek is just a tool that requires active, clear and refined search strategies.
 How to program deepseek
Feb 19, 2025 pm 05:36 PM
How to program deepseek
Feb 19, 2025 pm 05:36 PM
DeepSeek is not a programming language, but a deep search concept. Implementing DeepSeek requires selection based on existing languages. For different application scenarios, it is necessary to choose the appropriate language and algorithms, and combine machine learning technology. Code quality, maintainability, and testing are crucial. Only by choosing the right programming language, algorithms and tools according to your needs and writing high-quality code can DeepSeek be successfully implemented.
 How to use deepseek to settle accounts
Feb 19, 2025 pm 04:36 PM
How to use deepseek to settle accounts
Feb 19, 2025 pm 04:36 PM
Question: Is DeepSeek available for accounting? Answer: No, it is a data mining and analysis tool that can be used to analyze financial data, but it does not have the accounting record and report generation functions of accounting software. Using DeepSeek to analyze financial data requires writing code to process data with knowledge of data structures, algorithms, and DeepSeek APIs to consider potential problems (e.g. programming knowledge, learning curves, data quality)
 The Key to Coding: Unlocking the Power of Python for Beginners
Oct 11, 2024 pm 12:17 PM
The Key to Coding: Unlocking the Power of Python for Beginners
Oct 11, 2024 pm 12:17 PM
Python is an ideal programming introduction language for beginners through its ease of learning and powerful features. Its basics include: Variables: used to store data (numbers, strings, lists, etc.). Data type: Defines the type of data in the variable (integer, floating point, etc.). Operators: used for mathematical operations and comparisons. Control flow: Control the flow of code execution (conditional statements, loops).
 Problem-Solving with Python: Unlock Powerful Solutions as a Beginner Coder
Oct 11, 2024 pm 08:58 PM
Problem-Solving with Python: Unlock Powerful Solutions as a Beginner Coder
Oct 11, 2024 pm 08:58 PM
Pythonempowersbeginnersinproblem-solving.Itsuser-friendlysyntax,extensivelibrary,andfeaturessuchasvariables,conditionalstatements,andloopsenableefficientcodedevelopment.Frommanagingdatatocontrollingprogramflowandperformingrepetitivetasks,Pythonprovid





