 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 ThinkPHP5 core class Request remote code vulnerability analysis
ThinkPHP5 core class Request remote code vulnerability analysis
ThinkPHP5 core class Request remote code vulnerability analysis

1. Vulnerability introduction
On January 11, 2019, the ThinkPHP team released a patch update to fix A remote code execution vulnerability caused by unsafe dynamic function calls was discovered. This vulnerability is very harmful and can execute remote code by default. After conducting source code analysis and verification on multiple versions of ThinkPHP, Venus ADLab security researchers confirmed that the specifically affected version is the full version of ThinkPHP 5.0-5.0.23.
2. Vulnerability Reproduction
The local environment uses the full version of ThinkPHP 5.0.22 and PHP5.5.38 Apache to reproduce. After installing the environment, execute the POC to execute system commands, as shown in the figure:
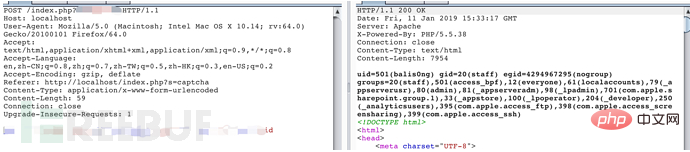
3. Vulnerability analysis
Based on the official website After analyzing the downloaded full version of 5.0.22, we first located the key point of the vulnerability:
thinkphp/library/think/Request.php:518
In the second if branch of the method function, an externally controllable data $_POST[Config::get is introduced ['var_method']. The value of var_method is _method.

The __construct function of the Request class is as follows:
Since the $options parameter is controllable, the attacker can overwrite the filter attribute, method attribute and get of the class The value of the attribute. In the param function of the Request class:
When $this->mergeParam is empty, $this->get(false) will be called here. Track the $this->get function:
The $this->input function is called at the end of the function and $this->get is passed in, and the value of $this->get is the attack controllable. Track the $this->input function:
This function calls $this->getFileter to obtain the filter. The function body is as follows:
$this->The value of filter is overridden and controlled by the attacker by calling the constructor. After returning the value, it will enter the input function:
View the filterValue function as follows :
In the call of the call_user_func function, $filter is controllable and $value is controllable. Therefore, code execution can be caused.
Vulnerability triggering process:
Start the analysis from the entry point of ThinkPHP5:
thinkphp/library/think/App.php:77
The first line of the run function instantiates a Request class. And assigned to $request. Then call routeCheck($request,$config):
Here call Route::check for route detection. The function is as follows:
Pay attention to the red font part. Corresponds to the first step at the beginning, which is to call the method function for variable coverage. The properties that need to be overridden here are $this->filter, $this->method, $this->get. Because the return value of $request->method() is $this->method, this value also needs to be controlled. The return value here is assigned to $method, and then the value of self::$rules[$method] is taken out and given to $rules. Note here: THINKPHP5 has an automatic class loading mechanism, which will automatically load some files in the vendor directory. However, the vendor directory structure of the full version and the core version is different.
The directory structure of the full version is as follows:
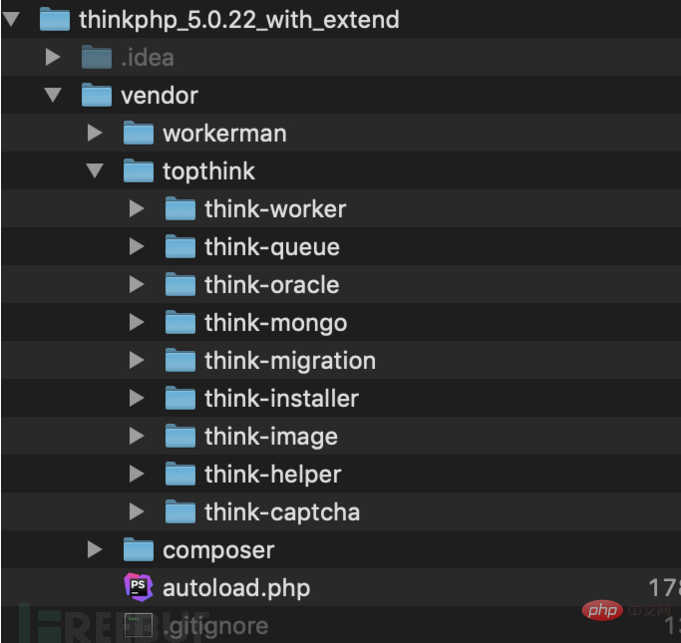
and the directory structure of the core version is as follows:
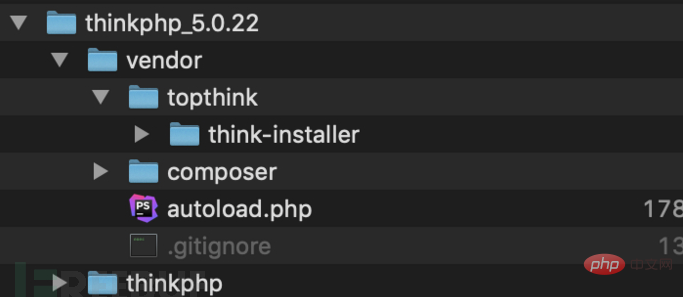
You can see that the full version has several more folders than the core version. What needs special attention is that there is a helper.php file in the think-captcha/src folder:
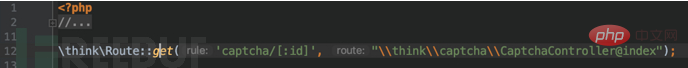
The \think\Route::get function is called here to register the route. operate. The impact of this step is to change the value of self::$rules mentioned above. Only with this route can RCE be performed, otherwise it will not succeed. This is why it only affects the full version and not the core version. At this time, the value of self::$rules is:
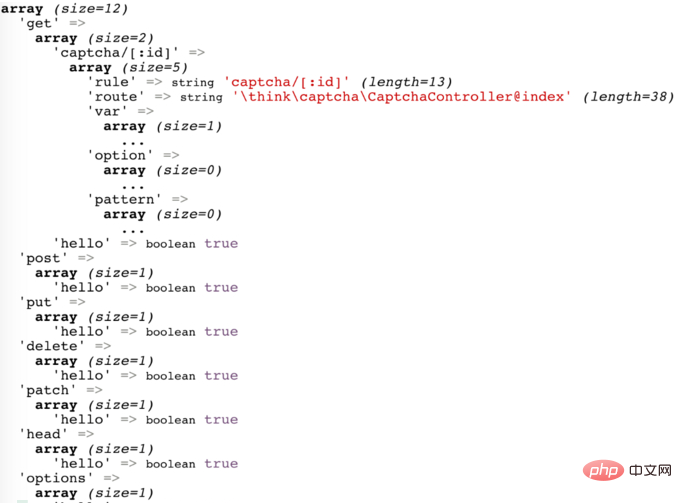
# Then, when the attacker controls the value of $method returned to be get, the value of $rules is this routing rules. Then go back to the above to get $rules, and get the value of $item according to the incoming URL, so that the value of $rules[$item] is the captcha routing array, and you can further call the self::parseRule function. The function body is slightly longer, here are the key points:
The value of $route passed in at this time is \think\captcha\CaptchaController@index. Therefore, we enter the if branch marked in red. In this branch, the value corresponding to the 'type' key of $result is 'method'. Then $result is returned layer by layer to the run function and assigned to $dispatch.
Then bring $dispatch into the self::exec function:
Enter the branch marked in red, which calls the param method of the Request class. Therefore, the third step of the exploit chain is satisfied, causing the command to be executed.
Venstar ADLab security researchers analyzed each version of ThinkPHP5.0-5.0.23 and found that ThinkPHP5.0.2-5.0.23 can use the same POC, while ThinkPHP5.0-5.0.1 needs to be changed. Let’s take a look at the POC. The reason lies in a small implementation difference of the rule function of Route.php.
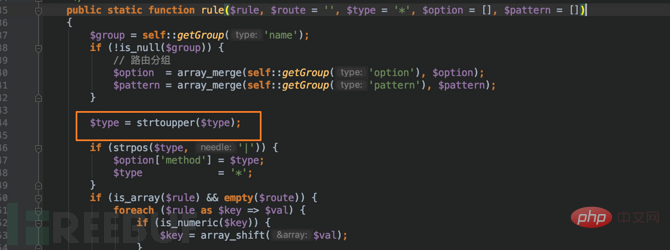
ThinkPHP5.0-5.0.1 version thinkphp/library/think/Route.php:235, convert $type to uppercase:
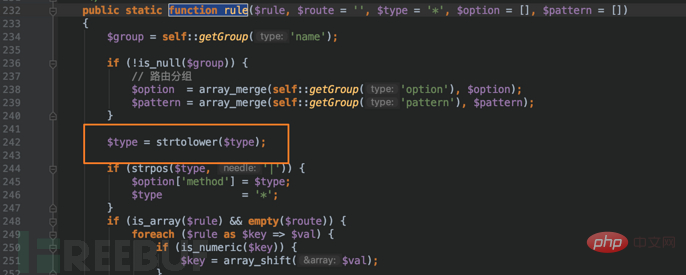
In ThinkPHP5.0.2-5.0.23 version, $type is converted to lowercase in the rule function:
4. Patch Analysis
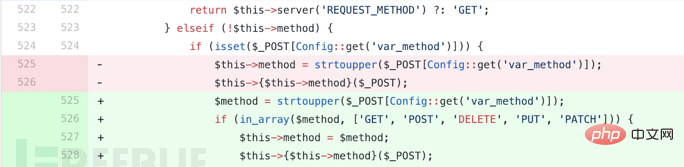
In ThinkPHP5.0.24, the judgment of $this->method has been added, and free calling of class functions is no longer allowed.
5. Conclusion
It is strongly recommended that users upgrade to ThinkPHP5.0.24 version and do not enable debug mode to avoid being attacked.
Related recommendations: "PHP Tutorial"
The above is the detailed content of ThinkPHP5 core class Request remote code vulnerability analysis. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1384
1384
 52
52
 What should I do if I get an error when deploying thinkphp5 in Pagoda?
Dec 19, 2022 am 11:04 AM
What should I do if I get an error when deploying thinkphp5 in Pagoda?
Dec 19, 2022 am 11:04 AM
Solution to the error reported when deploying thinkphp5 in Pagoda: 1. Open the Pagoda server, install the php pathinfo extension and enable it; 2. Configure the ".access" file with the content "RewriteRule ^(.*)$ index.php?s=/$1 [QSA ,PT,L]”; 3. In website management, just enable thinkphp’s pseudo-static.
 What should I do if thinkphp5 url rewriting fails?
Dec 12, 2022 am 09:31 AM
What should I do if thinkphp5 url rewriting fails?
Dec 12, 2022 am 09:31 AM
Solution to thinkphp5 url rewriting not working: 1. Check whether the mod_rewrite.so module is loaded in the httpd.conf configuration file; 2. Change None in AllowOverride None to All; 3. Modify the Apache configuration file .htaccess to "RewriteRule ^ (.*)$ index.php [L,E=PATH_INFO:$1]" and save it.
 How to get the requested URL in thinkphp5
Dec 20, 2022 am 09:48 AM
How to get the requested URL in thinkphp5
Dec 20, 2022 am 09:48 AM
Methods for thinkphp5 to obtain the requested URL: 1. Use the "$request = Request::instance();" method of the "\think\Request" class to obtain the current URL information; 2. Use the built-in helper function "$request-> url()" to obtain the complete URL address including the domain name.
 What should I do if thinkphp5 post cannot get the value?
Dec 06, 2022 am 09:29 AM
What should I do if thinkphp5 post cannot get the value?
Dec 06, 2022 am 09:29 AM
thinkphp5 post cannot get a value because TP5 uses the strpos function to find the app/json string in the content-type value of the Header. The solution is to set the content-type value of the Header to app/json.
 How to remove thinkphp5 title bar icon
Dec 20, 2022 am 09:24 AM
How to remove thinkphp5 title bar icon
Dec 20, 2022 am 09:24 AM
How to remove the thinkphp5 title bar icon: 1. Find the favicon.ico file under the thinkphp5 framework public; 2. Delete the file or choose another picture to rename it to favicon.ico and replace the original favicon.ico file.
 What should I do if thinkphp5 prompts that the controller does not exist?
Dec 06, 2022 am 10:43 AM
What should I do if thinkphp5 prompts that the controller does not exist?
Dec 06, 2022 am 10:43 AM
Solution to thinkphp5 prompting that the controller does not exist: 1. Check whether the namespace in the corresponding controller is written correctly and change it to the correct namespace; 2. Open the corresponding tp file and modify the class name.
 How to query yesterday's data in ThinkPHP5
Dec 05, 2022 am 09:20 AM
How to query yesterday's data in ThinkPHP5
Dec 05, 2022 am 09:20 AM
How to query yesterday's data in ThinkPHP5: 1. Open ThinkPHP5 related files; 2. Query yesterday's data through the expression "db('table')->whereTime('c_time', 'yesterday')->select();" Can.
 How to set error prompts in thinkphp5
Dec 07, 2022 am 10:31 AM
How to set error prompts in thinkphp5
Dec 07, 2022 am 10:31 AM
How to set error prompts in thinkphp5: 1. Enter the public folder in the project root directory and open the index.php entry file; 2. View the comments on the debug mode switch; 3. Adjust the value of the "APP_DEBUG" constant to true to display Error message prompt.



