
SQL injection attack is one of the common means used by hackers to attack databases. The following article will introduce you to SQL injection attacks. I hope it will be helpful to you.
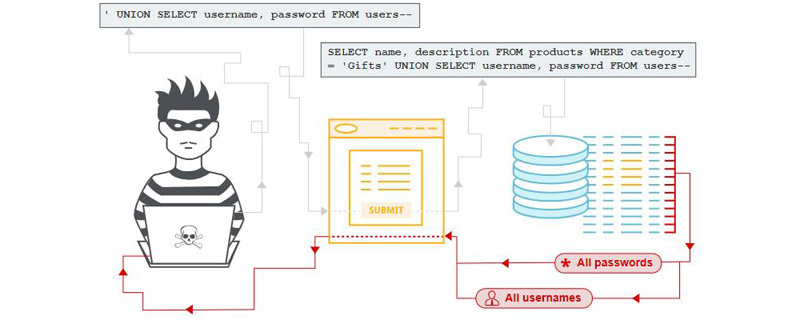
With the development of B/S mode application development, more and more programmers use this mode to write applications. However, due to the uneven level and experience of programmers, a considerable number of programmers do not judge the legality of user input data when writing code, causing security risks in applications. The user can submit a database query code and obtain some data he wants to know based on the results returned by the program. This is the so-called SQL Injection, that is, SQL injection.
SQL injection attack is one of the database security attack methods. Hackers can insert arbitrary malicious SQL code into database queries, allowing the attacker to fully control the database server behind the web application. Attackers can use SQL injection vulnerabilities to bypass application security measures; they can bypass authentication and authorization of a web page or web application and retrieve the contents of an entire SQL database; they can also use SQL injection to add, modify, and delete items in the database. Record.
SQL injection vulnerabilities can affect any website or web application that uses a SQL database such as MySQL, Oracle, SQL Server, or others. Criminals may use it to gain unauthorized access to users' sensitive data: customer information, personal data, trade secrets, intellectual property, etc. SQL injection attacks are one of the oldest, most popular, and most dangerous web application vulnerabilities.
SQL injection attacks can be effectively protected through database security protection technologies. Database security protection technologies include: database leak scanning, database encryption, database firewall, data desensitization, and database security audit system.
The above is the detailed content of What is sql injection attack. For more information, please follow other related articles on the PHP Chinese website!