Is it difficult to obtain secondary computer access?
From the perspective of the difficulty of the computer level exam; ACCESS secondary database is not difficult. The test papers over the years are repeated, the question types are basically the same, and most of the content is repeated. Generally, two or three months is enough to review. A passing score of 60 points is required for both the written test and the computer-based test.

But only when you are well prepared can you be more confident. Next, I will give you some advice. (Recommended learning: PHP video tutorial)
Because the national computer level two exam is divided into several types: one is language programming (C, C, Java, Visual Basic, Delphi ), the other is database programming (VisualFoxPro, Access). After we decide which one to take, we need to start buying books and materials. Examine Access in the database.

The National Computer Level 2 exam is divided into a written test and a computer-based exam. Different from the Computer Level 1 exam, the National Computer Level 2 written test and computer-based exam are both paperless exams. (taken on a computer).
We read the book we bought probably twice and highlighted the key points. Especially procedural questions must be drawn.
Then it’s time to take the real questions of the written test. National Computer Science Level 2 is much more difficult than Level 1, and there are many concepts that we don’t understand. We don’t have to worry about this because the written exams are all multiple-choice questions. Just look at the answers when you do the questions. But there’s one thing to note: write more. Write all the analysis in the answers into the real questions. It is best to write down each option clearly. Next time you encounter different questions, you will know which answer to choose.
After taking notes, review what you have written before each set of real questions before starting. This approach must be adhered to. After completing ten sets of real questions, there is no need to buy any more, just review them again and again.
The second step is the computer-based exam. There are four parts in the purchased materials. The following are what we need to read: The first part of the computer-based exam guide must be read. The second part is the compliance chapter. The third part is reference answers and analysis. We may or may not watch the fourth part. Because as long as you are familiar with the second part of the standard chapter, you will basically pass the exam.
Here I will talk about what you need to pay attention to when doing the standard article. Because the materials we purchased included video information, we watched other people’s steps before operating them, and then took notes on some operations we didn’t understand. Practice it repeatedly every day until you know how to operate it at a glance.
In addition to doing exercises on the computer, you can also read the real questions and think about how to operate on the computer.
As long as you do the above, I believe you will definitely pass the national computer level two exam.
For more PHP-related technical articles, please visit the PHP Graphic Tutorial column to learn!
The above is the detailed content of Is it difficult to obtain secondary computer access?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1381
1381
 52
52
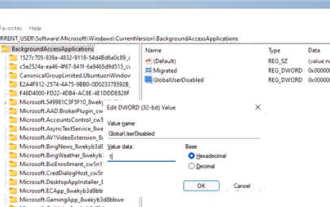 How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
1. Open settings in Windows 11. You can use Win+I shortcut or any other method. 2. Go to the Apps section and click Apps & Features. 3. Find the application you want to prevent from running in the background. Click the three-dot button and select Advanced Options. 4. Find the [Background Application Permissions] section and select the desired value. By default, Windows 11 sets power optimization mode. It allows Windows to manage how applications work in the background. For example, once you enable battery saver mode to preserve battery, the system will automatically close all apps. 5. Select [Never] to prevent the application from running in the background. Please note that if you notice that the program is not sending you notifications, failing to update data, etc., you can
 How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
DeepSeek cannot convert files directly to PDF. Depending on the file type, you can use different methods: Common documents (Word, Excel, PowerPoint): Use Microsoft Office, LibreOffice and other software to export as PDF. Image: Save as PDF using image viewer or image processing software. Web pages: Use the browser's "Print into PDF" function or the dedicated web page to PDF tool. Uncommon formats: Find the right converter and convert it to PDF. It is crucial to choose the right tools and develop a plan based on the actual situation.
 How to read dbf file in oracle
May 10, 2024 am 01:27 AM
How to read dbf file in oracle
May 10, 2024 am 01:27 AM
Oracle can read dbf files through the following steps: create an external table and reference the dbf file; query the external table to retrieve data; import the data into the Oracle table.
 Interpretation of Botanix: decentralized BTC L2 for network asset management (with interactive tutorial)
May 08, 2024 pm 06:40 PM
Interpretation of Botanix: decentralized BTC L2 for network asset management (with interactive tutorial)
May 08, 2024 pm 06:40 PM
Yesterday, BotanixLabs announced that it has completed a total of US$11.5 million in financing, with participation from Polychain Capital, Placeholder Capital and others. Financing will be used to build the decentralized EVM equivalent of BTCL2Botanix. Spiderchain combines the ease of use of EVM with the security of Bitcoin. Since the testnet went live in November 2023, there have been more than 200,000 active addresses. Odaily will analyze Botanix’s characteristic mechanism and testnet interaction process in this article. Botanix According to the official definition, Botanix is a decentralized Turing-complete L2EVM built on Bitcoin and consists of two core components: Ethereum Virtual Machine
 How to solve access violation error
May 07, 2024 pm 05:18 PM
How to solve access violation error
May 07, 2024 pm 05:18 PM
Access Violation error is a run-time error that occurs when a program accesses a memory location beyond its memory allocation, causing the program to crash or terminate abnormally. Solutions include: checking array boundaries; using pointers correctly; using appropriate memory allocation functions; freeing freed memory; checking for memory overflows; updating drivers and systems; checking third-party libraries; using a debugger to trace execution; contacting the software vendor for support.
 How to enable remote desktop control in Win11_How to enable remote desktop control in Win11
May 08, 2024 pm 12:19 PM
How to enable remote desktop control in Win11_How to enable remote desktop control in Win11
May 08, 2024 pm 12:19 PM
1. Search for the Control Panel page in the Start menu. 2. Then change the view to Category in the control panel and click System and Security. 3. Find and click the Allowremoteaccess button under System. 4. In the pop-up window, click the Remote system properties column, check the Allow remote connection to this computer button and click OK to save.
 How to solve the problem of third-party interface returning 403 in Node.js environment?
Mar 31, 2025 pm 11:27 PM
How to solve the problem of third-party interface returning 403 in Node.js environment?
Mar 31, 2025 pm 11:27 PM
Solve the problem of third-party interface returning 403 in Node.js environment. When we use Node.js to call third-party interfaces, we sometimes encounter an error of 403 from the interface returning 403...
 Laravel Redis connection sharing: Why does the select method affect other connections?
Apr 01, 2025 am 07:45 AM
Laravel Redis connection sharing: Why does the select method affect other connections?
Apr 01, 2025 am 07:45 AM
The impact of sharing of Redis connections in Laravel framework and select methods When using Laravel framework and Redis, developers may encounter a problem: through configuration...



