 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 What should I do if my website is attacked? How to find the source of website vulnerability attacks
What should I do if my website is attacked? How to find the source of website vulnerability attacks
What should I do if my website is attacked? How to find the source of website vulnerability attacks

Many corporate websites have been attacked, causing the website to jump to other websites, especially some lottery and other illegal websites. Some websites have even been attacked and cannot be opened, and customers cannot access the homepage. , causing great economic losses to customers. Many customers come to our SINE security company to seek solutions to prevent website attacks. In response to this situation, our security department’s technology will teach everyone how to find attacks after a website is attacked. sources and detect vulnerabilities in the website to prevent the website from being attacked again.
After the website is hacked and attacked, the first thing we need to check is to package and compress the website’s access logs, save them completely, and record them according to the time of the problem reported by the customer, the characteristics of the attack, etc. Then analyze the website logs one by one. The website access log records all users’ visits to the website, as well as the pages visited, and the error messages on the website, which can help us find the source of the attack and the vulnerabilities in the website. You can also find out and fix the website's vulnerabilities.
Let’s take the website of a certain enterprise customer some time ago as an example: first look at this log record:
2019-06-03 00:01:18 W3SVC6837 202.85.214.117 GET / Review.aspx class=1&byid=23571
80 - 101.89.239.230 Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; SLCC2; .NE
T CLR 2.0.50727; . NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6
.0; .NET4.0C; .NET4.0E; InfoPath.3; rv:11.0) like Gecko 200 0 0
Through the above website access log, we can see that the user’s access IP, the time of accessing the website, the Windows system used, the browser version used, and the status of accessing the website will be written 's very clear. So after the website is attacked, how to check the logs to trace the traces of the attack?
First of all, we need to communicate with the customer to determine the specific time period when the website was attacked, narrow down the log range through time, check the website logs one by one, and also detect the Trojan file names that exist on the website. , search the logs, find the file name, and then trace the attacker’s IP. Use the above clues to trace the source of the website’s attack and website vulnerabilities. The log opening tool uses notepad. Some websites use Linux servers and you can use some Linux commands to view the logs. The specific commands are as follows
Picture:

A webshell Trojan file was uploaded to a customer website. The attacker tampered with the website by accessing the script file. The title description on the homepage was tampered with the content of the lottery. Clicking on the website from Baidu jumped to other websites. The customer himself did After being promoted by Baidu, they suffered heavy losses and found us at SINE Security. We extracted the website's access logs based on the customer's attack characteristics, and traced the source of the website's attacks and the vulnerabilities in the website. We checked the access records of all user IPs on that day through time. First, we manually checked the webshell file in the root directory of the website. We searched the log through the demo.php and saw that there was an IP that was constantly accessing the file. , we extracted and analyzed all access records of the IP and found that the attacker visited the upload page of the website and uploaded the website Trojan backdoor through the upload function.
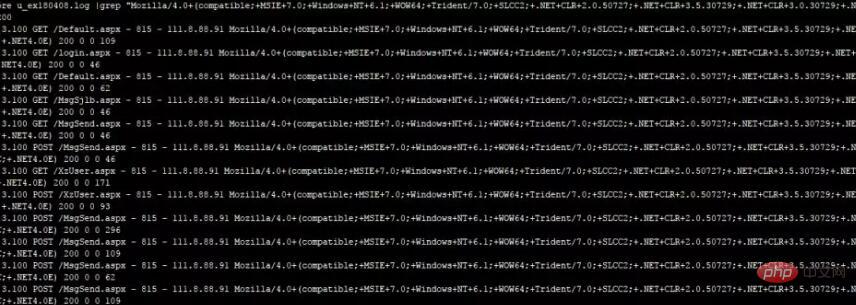 Through the IP traced through the above logs and the website access records, we found the loopholes in the website. The upload function of the website did not perform security judgment and filtering on the uploaded file format, resulting in When uploading aspx, php and other execution scripts, the upload directory of the website has not been set up for security, and the execution permission of the script has been cancelled. In response to the above situation, our SINE security repaired the customer's website vulnerability and restricted the execution of only images and other formats. File upload, secure deployment of the website's upload directory, and a series of website security reinforcements. After the website is attacked, don't panic first. You should analyze the website's logs as soon as possible to find the source of the attack and the vulnerabilities in the website. If you don’t know much about the website, you can also find a professional website security company to handle it. Let the professionals do the professional things. Whether it is the website’s logs or the website’s source code, we must use them to find them thoroughly. The root cause of website attacks.
Through the IP traced through the above logs and the website access records, we found the loopholes in the website. The upload function of the website did not perform security judgment and filtering on the uploaded file format, resulting in When uploading aspx, php and other execution scripts, the upload directory of the website has not been set up for security, and the execution permission of the script has been cancelled. In response to the above situation, our SINE security repaired the customer's website vulnerability and restricted the execution of only images and other formats. File upload, secure deployment of the website's upload directory, and a series of website security reinforcements. After the website is attacked, don't panic first. You should analyze the website's logs as soon as possible to find the source of the attack and the vulnerabilities in the website. If you don’t know much about the website, you can also find a professional website security company to handle it. Let the professionals do the professional things. Whether it is the website’s logs or the website’s source code, we must use them to find them thoroughly. The root cause of website attacks.
For more Linux articles, please visit the Linux Tutorial column to learn!
The above is the detailed content of What should I do if my website is attacked? How to find the source of website vulnerability attacks. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Jailbreak any large model in 20 steps! More 'grandma loopholes' are discovered automatically
Nov 05, 2023 pm 08:13 PM
Jailbreak any large model in 20 steps! More 'grandma loopholes' are discovered automatically
Nov 05, 2023 pm 08:13 PM
In less than a minute and no more than 20 steps, you can bypass security restrictions and successfully jailbreak a large model! And there is no need to know the internal details of the model - only two black box models need to interact, and the AI can fully automatically defeat the AI and speak dangerous content. I heard that the once-popular "Grandma Loophole" has been fixed: Now, facing the "Detective Loophole", "Adventurer Loophole" and "Writer Loophole", what response strategy should artificial intelligence adopt? After a wave of onslaught, GPT-4 couldn't stand it anymore, and directly said that it would poison the water supply system as long as... this or that. The key point is that this is just a small wave of vulnerabilities exposed by the University of Pennsylvania research team, and using their newly developed algorithm, AI can automatically generate various attack prompts. Researchers say this method is better than existing
 Buffer overflow vulnerability in Java and its harm
Aug 09, 2023 pm 05:57 PM
Buffer overflow vulnerability in Java and its harm
Aug 09, 2023 pm 05:57 PM
Buffer overflow vulnerabilities in Java and their harm Buffer overflow means that when we write more data to a buffer than its capacity, it will cause data to overflow to other memory areas. This overflow behavior is often exploited by hackers, which can lead to serious consequences such as abnormal code execution and system crash. This article will introduce buffer overflow vulnerabilities and their harm in Java, and give code examples to help readers better understand. The buffer classes widely used in Java include ByteBuffer, CharBuffer, and ShortB
 How to solve common file upload vulnerabilities in PHP language development?
Jun 10, 2023 am 11:10 AM
How to solve common file upload vulnerabilities in PHP language development?
Jun 10, 2023 am 11:10 AM
In the development of web applications, the file upload function has become a basic requirement. This feature allows users to upload their own files to the server and then store or process them on the server. However, this feature also makes developers need to pay more attention to a security vulnerability: the file upload vulnerability. Attackers can attack the server by uploading malicious files, causing the server to suffer varying degrees of damage. PHP language is one of the languages widely used in web development, and file upload vulnerabilities are also one of the common security issues. This article will introduce
 The OpenAI DALL-E 3 model has a vulnerability that generates 'inappropriate content.' A Microsoft employee reported it and was slapped with a 'gag order.'
Feb 04, 2024 pm 02:40 PM
The OpenAI DALL-E 3 model has a vulnerability that generates 'inappropriate content.' A Microsoft employee reported it and was slapped with a 'gag order.'
Feb 04, 2024 pm 02:40 PM
According to news on February 2, Shane Jones, manager of Microsoft’s software engineering department, recently discovered a vulnerability in OpenAI’s DALL-E3 model, which is said to be able to generate a series of inappropriate content. Shane Jones reported the vulnerability to the company, but was asked to keep it confidential. However, he eventually decided to disclose the vulnerability to the outside world. ▲Image source: Report disclosed by ShaneJones. This site noticed that ShaneJones discovered through independent research in December last year that there was a vulnerability in the DALL-E3 model of OpenAI text-generated images. This vulnerability can bypass the AI Guardrail (AIGuardrail), resulting in the generation of a series of NSFW inappropriate content. This discovery attracted widespread attention
 Comma operator vulnerabilities and protective measures in Java
Aug 10, 2023 pm 02:21 PM
Comma operator vulnerabilities and protective measures in Java
Aug 10, 2023 pm 02:21 PM
Overview of Comma Operator Vulnerabilities and Defense Measures in Java: In Java programming, we often use the comma operator to perform multiple operations at the same time. However, sometimes we may overlook some potential vulnerabilities of the comma operator that may lead to unexpected results. This article will introduce the vulnerabilities of the comma operator in Java and provide corresponding protective measures. Usage of comma operator: The syntax of comma operator in Java is expr1, expr2, which can be said to be a sequence operator. Its function is to first calculate ex
 Lenovo has issued a patch in May, Phoenix UEFI firmware vulnerability disclosed: affecting hundreds of Intel PC CPU models
Jun 22, 2024 am 10:27 AM
Lenovo has issued a patch in May, Phoenix UEFI firmware vulnerability disclosed: affecting hundreds of Intel PC CPU models
Jun 22, 2024 am 10:27 AM
According to news from this site on June 21, the Phoenix Secure Core UEFI firmware was exposed to a security vulnerability, affecting hundreds of Intel CPU devices. Lenovo has released a new firmware update to fix the vulnerability. This site learned from reports that the vulnerability tracking number is CVE-2024-0762, known as "UEFICANHAZBUFFEROVERFLOW", which exists in the Trusted Platform Module (TPM) configuration of Phoenix UEFI firmware. It is a buffer overflow vulnerability that can be Exploit to execute arbitrary code on a vulnerable device. The vulnerability was discovered by Eclypsium in Lenovo ThinkPad X1 Carbon 7th generation and X1Yoga 4th generation
 Zerodium announces $400,000 payout for Microsoft Outlook Zero-Click RCE security vulnerability
Apr 29, 2023 pm 09:28 PM
Zerodium announces $400,000 payout for Microsoft Outlook Zero-Click RCE security vulnerability
Apr 29, 2023 pm 09:28 PM
<ul><li><strong>Click to enter:</strong>ChatGPT tool plug-in navigation</li></ul><figureclass="imageimage--expandable"><imgsrc ="/uploads/2023041
 HTTP response splitting vulnerability in Java and its fix
Aug 08, 2023 am 08:19 AM
HTTP response splitting vulnerability in Java and its fix
Aug 08, 2023 am 08:19 AM
Summary of HTTP Response Splitting Vulnerabilities in Java and Their Fixes: In Java Web applications, HTTP response splitting vulnerabilities are a common security threat. This article will introduce the principle and impact of the HTTP response splitting vulnerability, as well as how to fix the vulnerability, and use code examples to help developers better understand and prevent such security threats. Introduction The HTTP protocol is one of the most commonly used protocols in web applications. It communicates through HTTP requests and HTTP responses to provide interaction with the web server.



