

● XSS (cross-site scripting attack) has two forms: inputting JS code or HTML code causes page chaos.
● XSS (cross-site scripting attack) can be used to steal other users’ cookie information. To avoid such problems, you can use the following solutions:
Filter all JavaScript scripts directly;
Escape Html metacharacters and use functions such as htmlentities and htmlspecialchars;
The system’s extended function library provides the remove_xss method for XSS security filtering;
Some of the new version’s URL access features System variables have been processed by XSS.
When users submit form information, there may be relevant "code" (html/css/js and other codes) in the form, which will interfere with the page effect when the information is displayed.
1. Download htmlpurifier, unzip it and put the library folder into the ThinkPhp plug-in folder and create function.php in the grouped common folder
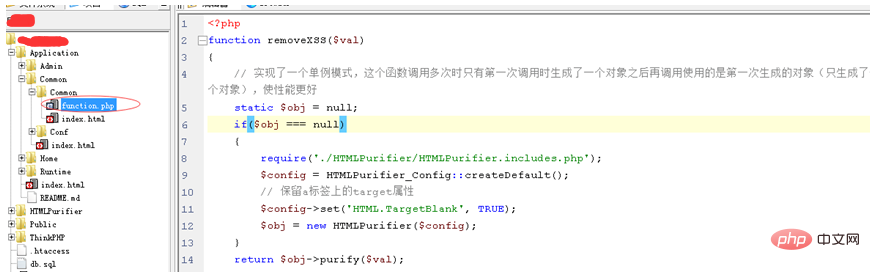
2. Create it in function, php Methods to prevent xss attacks
3. We can first filter the data obtained from the post through the I() method that comes with the hThinkphp system, and then filter it by calling the function fanXSS
Take the following example:
In the background process of thinphp development, you need to add an editor. To make the editor display normally, you need to set the I function not to filter.
Now the problem is coming. If you don’t filter, you will be attacked by XSS. If you filter the online editor, it will not work. The solution should be selective filtering.
We can An open source filtering package: htmlpurifier package.
Extract the downloaded package to the directory and rename it to HTMLpurifier
Create a function
Then modify the configuration file config.php to let the I function use this function to filter:
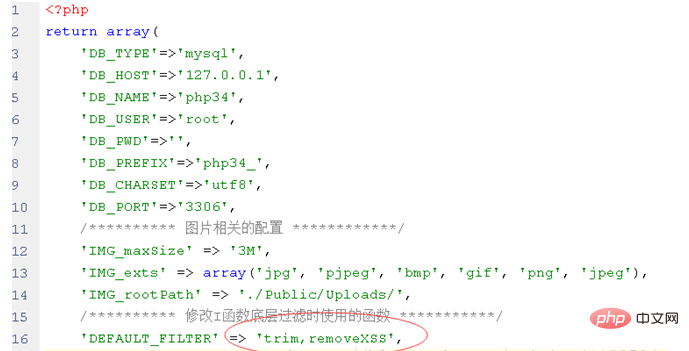
Now the I function in the website uses the function we wrote when filtering: Selective The filter only filters dangerous code.
The website is very safe!
This article comes from the ThinkPHP framework technical article column: http://www.php.cn/phpkj/thinkphp/
The above is the detailed content of How to prevent XSS attacks in thinkphp. For more information, please follow other related articles on the PHP Chinese website!