

According to the official CVE vulnerability report, we learned that WordPress has a new combined rce vulnerability. The vulnerability numbers are CVE-2019-8943 and CVE-2019-8942. Download the source code of the vulnerability version and analyze it. Vulnerability triggering process, note: When the vulnerability recurs, the network must be disconnected to build. WordPress will automatically update the code package when it is connected to the Internet. Find the file post.php where the vulnerability occurs. WordPress has multiple post.php files. Here is a brief explanation of their respective functions. wp-includes/post.php is the source file of post, and wp-admin/includes/post.php has the backend. Permissioned post interface, wp-admin/post.php is for background post request processing. The specific calling code is as follows:
wp-admin/post.php:require_once( dirname( __FILE__ ) . '/admin.php' ); wp-admin/admin.php:require_once(ABSPATH . 'wp-admin/includes/admin.php'); wp-admin/includes/admin.php:require_once(ABSPATH . 'wp-admin/includes/post.php'); wp-admin/admin.php::require_once(dirname(dirname(__FILE__)) . '/wp-load.php'); wp-load.php:require_once( dirname( ABSPATH ) . '/wp-config.php' ); wp-config.php:require_once(ABSPATH . 'wp-settings.php'); wp-settings.php:require( ABSPATH . WPINC . '/post.php' ); define( 'WPINC', 'wp-includes' );
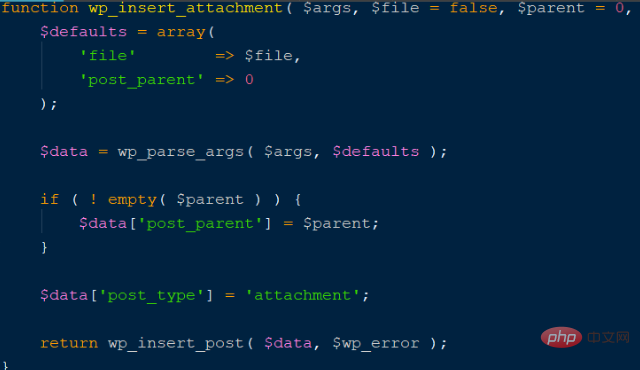
According to the above calling process, the vulnerability exploitation process is to upload an image to the media library and then update it. Operation, call the wp-admin/post.php function, and switch to case:editpost, as shown in the following figure:
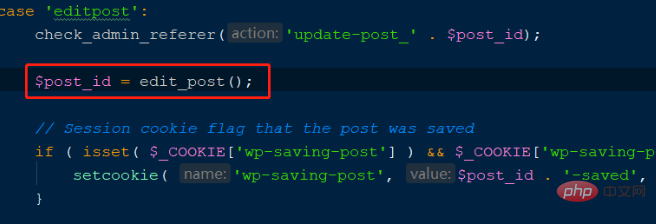
where edit_post is the vulnerability function, enter the function declaration, As shown in the figure below:
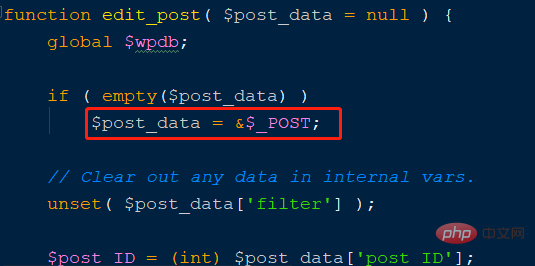
$post_data is a post array without any filtering protection, which caused subsequent vulnerabilities. Compare the repaired code, as shown in the figure below Instructions:
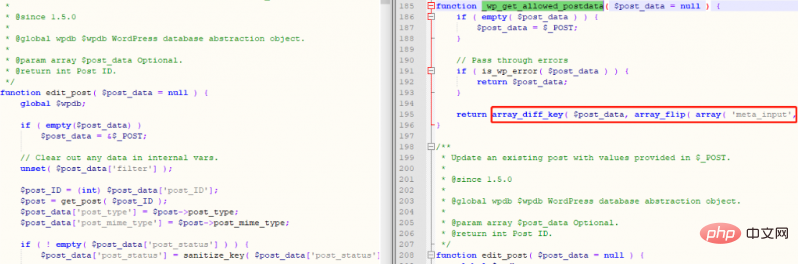
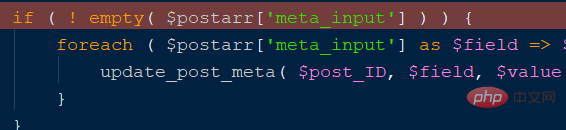
I will say a few more words here, because I did not find that wordpress will automatically update when connected to the Internet at the beginning, so I located another similar vulnerability point. , as shown in the figure below:
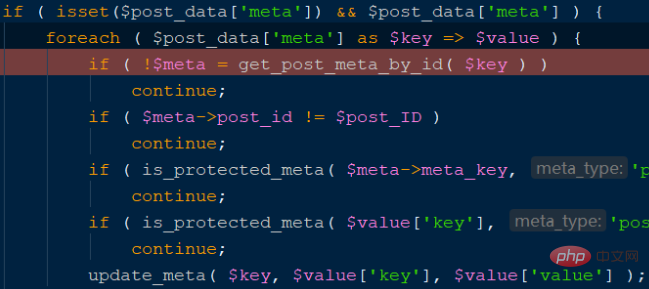
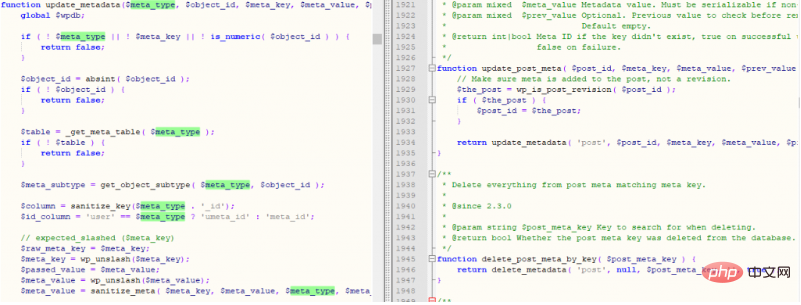
The above code will update_meta based on the incoming meta array. According to the $key (meta_id in the database) in the code, $value[' key'] (meta_key in the database), $value['value'] (meta_value in the database), construct meta[1][key]=_wp_attached_file&meta[1][value]=123, and finally execute a database statement similar to the following UPDATE `wp_postmeta` SET `meta_key` = '_wp_attached_file', `meta_value` = '123' WHERE `meta_id` = 2, the implementation process is as shown in the figure below:
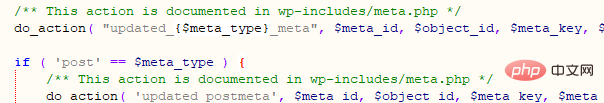
#Related Recommended: "WordPress Tutorial"
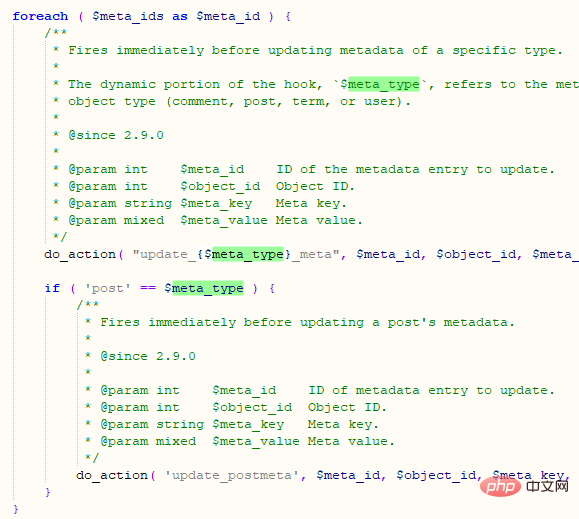
Update the content in the wp_postmeta table according to meta_id, and finally execute the do_action function, as shown in the following figure:

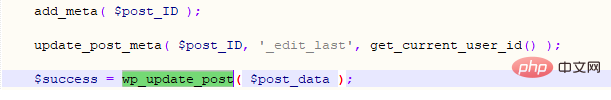
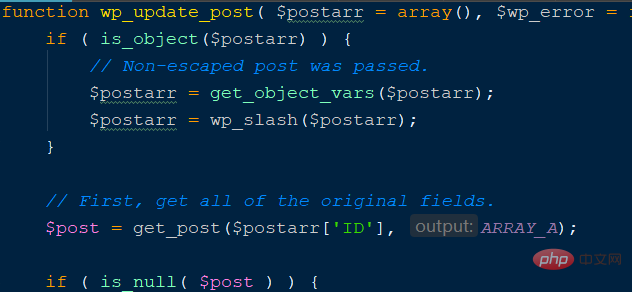
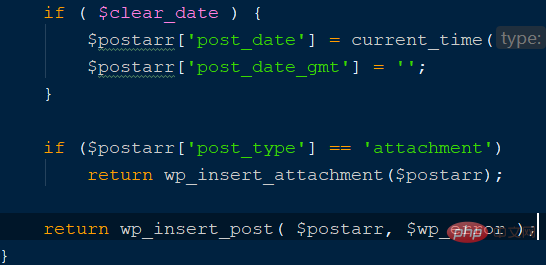
Complete the WordPress directory traversal vulnerability here, and then use the local file inclusion vulnerability to execute rce. WordPress officially uses image libraries for GD and Imagick, as shown in the following figure:
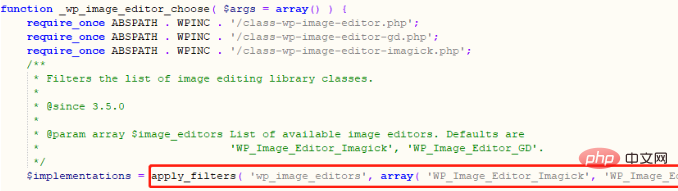
Imagick does not come with WordPress and requires downloading a plug-in, so by default you can execute arbitrary code by bypassing the GD library.
The above is the detailed content of Does wordpress have vulnerabilities?. For more information, please follow other related articles on the PHP Chinese website!