
Make a note here. After reading some information on the Internet, I understand the working principle of the https protocol.
First let’s talk about symmetric encryption and asymmetric encryption. Symmetric encryption means that the same secret key is used when encrypting and decrypting information. , the advantage of symmetric encryption is high efficiency but relatively insecure; asymmetric encryption keys are divided into public keys and private keys. We can use private key encryption and public key decryption. Of course, we can also use public key encryption and private key decryption. The advantage of symmetric encryption is that it is more secure than symmetric encryption, but it is less efficient.
The communication between the client and the server is carried out using a combination of asymmetric encryption and symmetric encryption. That is, asymmetric encryption is first used to negotiate the encryption key for symmetric encryption, and then symmetric encryption is used. Information is transmitted in an encrypted manner. This not only ensures the security of information but also solves the efficiency problem caused by decrypting information during information transmission.
In order to ensure that the information is not tampered with by hackers during the transmission of the encrypted public key, a CA organization is required to ensure the correctness of the encrypted public key. General process:
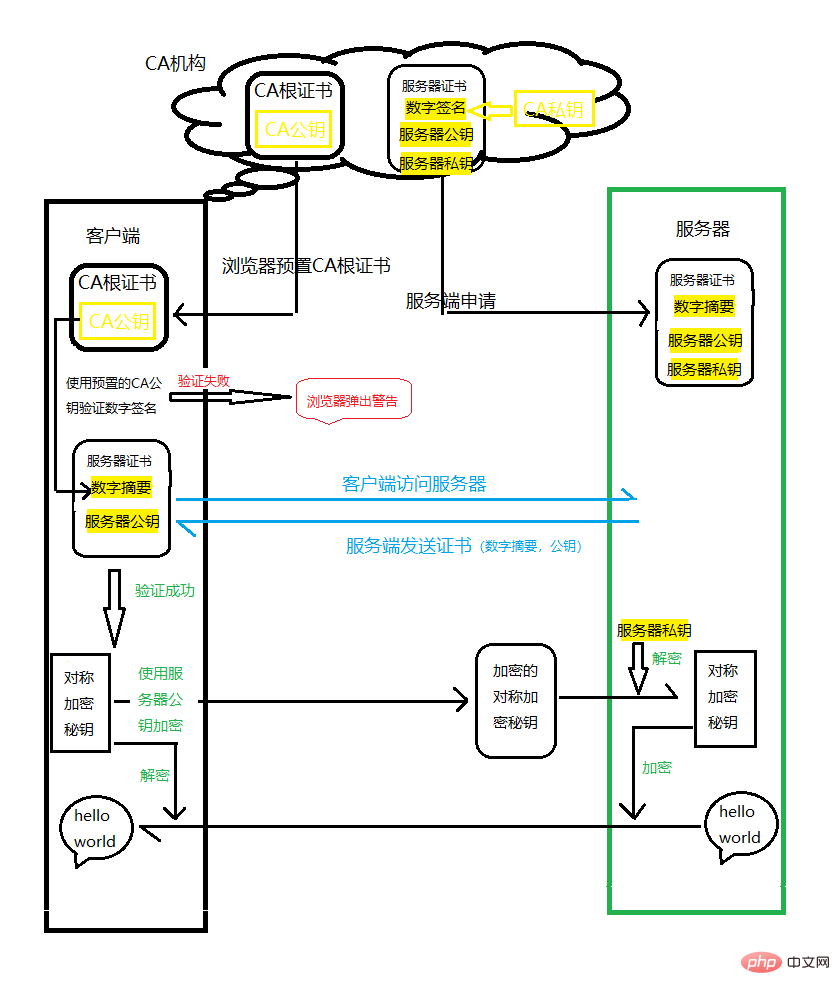
#1. The administrator of the website applies to the CA service provider for the server key (public key and private key)
2. Client Request the server to obtain the public key, and use the CA root certificate preset by the CA organization on the client to verify whether the server public key is correct, whether it is within the validity period, etc.
3. If there is no problem in verifying the server public key, the client Generate a secret key for symmetric encryption and encrypt it using the server's public key, and send it to the server
4. After receiving the encrypted secret key, the server uses the private key to decrypt and obtain the actual symmetric encryption The secret key value, and then uses symmetric encryption to encrypt the information to be transmitted
5. After receiving the information, the client uses the symmetric encryption key to decrypt and obtain the actual information content transmitted by the server
The above is compiled from books. I hope it will be helpful to everyone. If there are any errors, please point them out to avoid misleading everyone.
For more related questions, please visit the PHP Chinese website: PHP Video Tutorial
The above is the detailed content of Personal understanding sharing about HTTPS principles. For more information, please follow other related articles on the PHP Chinese website!