502 bad gateway nginx what does it mean?

1. What does 502 bad gateway nginx mean?
Generally speaking, 502 bad gateway means there is a problem with the website you are visiting, because when the 502 Bad Gateway server acts as a gateway or proxy, it is to complete access to the next server, but the server returns An illegal response was received. Maybe temporarily, maybe yes. It is recommended that you wait for a while and try to access again.
2. What causes 502 bad gateway?
Most of the reasons for 502 bad gateway are due to connection timeout. We send a request to the server. Because the server currently has too many connections, the server cannot give a normal response. This will occur. 502 bad gateway error.
Generally speaking, the server just acts as a gateway or proxy to meet the requirements of customers (such as web browsers) to access the URL we request. The server received an invalid response from the upstream server it requested to access. This does not mean that the upstream server is down (unresponsive gateway/proxy), but that the upstream server and gateway/proxy do not agree on the protocol to exchange data. Since the Internet protocol is fixed, this means that one or two machines have been incorrectly or not fully programmed.
3. What is the cause of the fixed 502 error?
Generally this problem is due to poor IP communication between the backend computers, possibly including the web server for the site you are trying to access. While analyzing this issue, you should clear your browser cache before visiting again.
If you see this problem on all websites you try to access when surfing the Internet, there are two possibilities
①Your ISP has a major equipment failure/overload
②Yes Problems with the internal internet connection such as your firewall not functioning properly.
In this case, only your ISP can help you. In the second case, you need to fix what is blocking your access to the Internet.
If you only experience this problem with some of the websites you are trying to access, it is most likely a problem with one of these websites, whose equipment is malfunctioning or overloaded. Contact your site's administrator.
4. How to rescue 502 bad gateway?
1. Refresh
To put it bluntly, it is very simple - refresh (not an ordinary refresh)
The refresh mentioned here mainly refers to downloading from the server The data is sent to the local hard disk browser, and then the data is read from the local hard disk and displayed in the browser for us to see. There are usually two refresh modes:
①Basic refresh: click refresh or use the F5 shortcut key
The basic refresh just re-fetches the data from the local hard disk to the browser, and does not redirect it to the browser. The server makes the request. Most users refresh like this most of the time, and it has no effect when encountering a 502 error.
② Refresh from the server: If you re-click directly on the webpage link you want to browse, you will find the "502 bad gateway" error message page that was just displayed. After re-clicking the link, you can browse normally.
Solution: Refresh from the server: shortcut key ctrl F5. This will resend the request to the server. If the server can respond to you normally, you can see the page.
2. DNS buffering problem
This situation is mainly caused by you visiting some foreign websites that are blocked by the national firewall, such as YouTube and Facebook.
Solution: In this case, access is usually available within a few minutes. You can also try running ipconfig /flushdns in the cmd window to refresh the DNS cache
3. DNS is hijacked
Solution: Change the DNS, 114.114.114.114 is recommended, and Ali’s public DNS such as: 223.5.5.5, 223.6.6.6
5. Nginx 502 bad gateway error
① Check whether php-cgi is running
Sometimes due to excessive website traffic or other reasons, php-cgi goes down directly, so we have to check whether php-cgi is running. Execute the following command:
1 |
|
If it is not running, we can start it manually
1 |
|
If you find that php-cgi sometimes goes down for unknown reasons, you can use the following script to temporarily solve the problem. Add to cronjob.
1 |
|
②The reason why the number of fastcgi processes is not enough and the php execution time is long
The number of fastcgi processes can modify the value of max_children in php-fpm.conf, and the memory consumed by php-cgi at peak times It is 20M, please calculate it according to your own memory situation.
Limiting the execution time of php can be set in request_terminate_timeout in php-fpm.conf. This is to prevent bugs in the php program from causing php-cgi to die.
③FastCGI execution time is too long
Increase the following parameter values according to the actual situation
1 |
|
6. Solve the 502 error in nginx
①查看当前的PHP FastCGI进程数是否够用
1 |
|
如果实际使用的"FastCGI进程数"接近预设的"FastCGI进程数",那么,说明"FastCGI进程数"不够用,需要增大。
②部分PHP程序的执行时间超过了Nginx的等待时间,可以适当增加nginx.conf配置文件中FastCGI的timeout时间
例如,系统当前的PHP FastCGI进程数明显超过了预设值的64这个数值,在电信的服务器上查看当前的PHP FastCGI进程数没有高于64这个数值,而且网通线路的活动连接明显高于电信的活动连接,由此可以说明出现nginx不稳定的情况是由于服务器访问负载过大引起的。
总结:php-cgi进程数不够用、php执行时间长、或者是php-cgi进程死掉,都会出现502错误。
更多Nginx相关技术文章,请访问Nginx使用教程栏目进行学习!
The above is the detailed content of 502 bad gateway nginx what does it mean?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to allow external network access to tomcat server
Apr 21, 2024 am 07:22 AM
How to allow external network access to tomcat server
Apr 21, 2024 am 07:22 AM
To allow the Tomcat server to access the external network, you need to: modify the Tomcat configuration file to allow external connections. Add a firewall rule to allow access to the Tomcat server port. Create a DNS record pointing the domain name to the Tomcat server public IP. Optional: Use a reverse proxy to improve security and performance. Optional: Set up HTTPS for increased security.
 How to generate URL from html file
Apr 21, 2024 pm 12:57 PM
How to generate URL from html file
Apr 21, 2024 pm 12:57 PM
Converting an HTML file to a URL requires a web server, which involves the following steps: Obtain a web server. Set up a web server. Upload HTML file. Create a domain name. Route the request.
 How to deploy nodejs project to server
Apr 21, 2024 am 04:40 AM
How to deploy nodejs project to server
Apr 21, 2024 am 04:40 AM
Server deployment steps for a Node.js project: Prepare the deployment environment: obtain server access, install Node.js, set up a Git repository. Build the application: Use npm run build to generate deployable code and dependencies. Upload code to the server: via Git or File Transfer Protocol. Install dependencies: SSH into the server and use npm install to install application dependencies. Start the application: Use a command such as node index.js to start the application, or use a process manager such as pm2. Configure a reverse proxy (optional): Use a reverse proxy such as Nginx or Apache to route traffic to your application
 Can nodejs be accessed from the outside?
Apr 21, 2024 am 04:43 AM
Can nodejs be accessed from the outside?
Apr 21, 2024 am 04:43 AM
Yes, Node.js can be accessed from the outside. You can use the following methods: Use Cloud Functions to deploy the function and make it publicly accessible. Use the Express framework to create routes and define endpoints. Use Nginx to reverse proxy requests to Node.js applications. Use Docker containers to run Node.js applications and expose them through port mapping.
 How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
How to deploy and maintain a website using PHP
May 03, 2024 am 08:54 AM
To successfully deploy and maintain a PHP website, you need to perform the following steps: Select a web server (such as Apache or Nginx) Install PHP Create a database and connect PHP Upload code to the server Set up domain name and DNS Monitoring website maintenance steps include updating PHP and web servers, and backing up the website , monitor error logs and update content.
 How to use Fail2Ban to protect your server from brute force attacks
Apr 27, 2024 am 08:34 AM
How to use Fail2Ban to protect your server from brute force attacks
Apr 27, 2024 am 08:34 AM
An important task for Linux administrators is to protect the server from illegal attacks or access. By default, Linux systems come with well-configured firewalls, such as iptables, Uncomplicated Firewall (UFW), ConfigServerSecurityFirewall (CSF), etc., which can prevent a variety of attacks. Any machine connected to the Internet is a potential target for malicious attacks. There is a tool called Fail2Ban that can be used to mitigate illegal access on the server. What is Fail2Ban? Fail2Ban[1] is an intrusion prevention software that protects servers from brute force attacks. It is written in Python programming language
 Come with me to learn Linux and install Nginx
Apr 28, 2024 pm 03:10 PM
Come with me to learn Linux and install Nginx
Apr 28, 2024 pm 03:10 PM
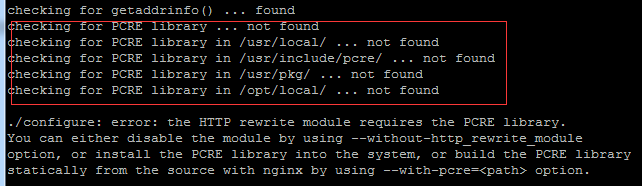
Today, I will lead you to install Nginx in a Linux environment. The Linux system used here is CentOS7.2. Prepare the installation tools 1. Download Nginx from the Nginx official website. The version used here is: 1.13.6.2. Upload the downloaded Nginx to Linux. Here, the /opt/nginx directory is used as an example. Run "tar-zxvfnginx-1.13.6.tar.gz" to decompress. 3. Switch to the /opt/nginx/nginx-1.13.6 directory and run ./configure for initial configuration. If the following prompt appears, it means that PCRE is not installed on the machine, and Nginx needs to
 Several points to note when building high availability with keepalived+nginx
Apr 23, 2024 pm 05:50 PM
Several points to note when building high availability with keepalived+nginx
Apr 23, 2024 pm 05:50 PM
After yum installs keepalived, configure the keepalived configuration file. Note that in the keepalived configuration files of master and backup, the network card name is the network card name of the current machine. VIP is selected as an available IP. It is usually used in high availability and LAN environments. There are many, so this VIP is an intranet IP in the same network segment as the two machines. If used in an external network environment, it does not matter whether it is on the same network segment, as long as the client can access it. Stop the nginx service and start the keepalived service. You will see that keepalived pulls the nginx service to start. If it cannot start and fails, it is basically a problem with the configuration files and scripts, or a prevention problem.




