The world's most mainstream encryption algorithm
An epoch-making algorithm, earth-shattering; an encryption algorithm that can only be cracked with computing power

##RSA algorithm Stepping out of the historical stage (recommended learning: webfront-end video tutorial)
The time came to 1976, two American computer scientists Whitfield Diffie and Martin Herbert Martin Hellman, for the first time proved that decryption can be completed without directly transmitting the key. This is called the "Diffie-Hellman Key Exchange Algorithm". The emergence of the DH algorithm has epoch-making significance: from this moment on, it enlightens people that different rules can be used for encryption and decryption, as long as there is a certain correspondence between the rules. This new mode is also called "asymmetric encryption algorithm": (1) Party B generates two keys, a public key and a private key. The public key is public and can be obtained by anyone, while the private key is kept secret. (2) Party A obtains Party B’s public key and uses it to encrypt the information. (3) Party B obtains the encrypted information and decrypts it with the private key. The information encrypted by the public key can only be decrypted by the private key. As long as the private key is not leaked, the communication is safe. Just one year after the invention of the DH algorithm, in 1977, Ron Rivest, Adi Shamir and Leonard Adleman They proposed the RSA algorithm together at MIT. RSA is composed of the initial letters of their last names spelled together.The newly born RSA algorithm has more powerful characteristics than the DH algorithm, because the DH algorithm is only used for key distribution, while the RSA algorithm can be used for information encryption and digital signatures. In addition, the longer the key of the RSA algorithm, the difficulty of cracking increases exponentially.
Because of its powerful performance, it is no exaggeration to say that wherever there is a computer network, there is the RSA algorithm.
This is how the RSA algorithm works
The RSA algorithm is famous all over the world, so how does it work?The first step , randomly select two unequal prime numbers p and q. The second step is to calculate the product n of p and q. The length of n is the key length, generally expressed in binary, and the general length is 2048 bits. The longer the number of digits, the harder it is to crack. The third step is to calculate the Euler function φ(n) of n. The fourth step is to randomly select an integer e, where 1< e < φ(n), and e and φ(n) are relatively prime. The fifth step is to calculate the modular inverse element d of e with respect to φ(n). The so-called "modular inverse element" means that there is an integer d that can make the remainder of ed divided by φ(n) 1. The sixth step is to encapsulate n and e into public key (n,e), and encapsulate n and d into private key (n,d). Suppose user A wants to send encrypted information m to user B, and he wants to encrypt m with the public key (n,e). The encryption process is actually a formula: After user B receives the information c, he uses the private key (n, d) to decrypt it. The decryption process is also a formula: In this way, user B knows that the message sent by user A is m. As long as user B keeps the number d secret, others will not be able to obtain the encrypted information m based on the transmitted information c. The RSA algorithm uses (n, e) as the public key. Is it possible to deduce d when n and e are known? (1)ed≡1 (mod φ(n)). Only by knowing e and φ(n) can we calculate d. (2)φ(n)=(p-1)(q-1). Only by knowing p and q can we calculate φ(n). (3)n=pq. Only by factoring n can we calculate p and q. So, if n can be decomposed very simply, it is easy to calculate d, which means the information is cracked.But currently the factorization of large integers is a very difficult thing. At present, apart from brute force cracking, no other effective method has been found. In other words, as long as the key length is long enough, information encrypted with RSA cannot actually be decrypted.
RSA algorithm is gradually being applied to all aspects of human beingsDue to the reliability of the RSA algorithm, this technology is now applied in many places. The most important application is the protection of information transmission on the Internet. Using the RSA algorithm, even if it is intercepted during the transmission process, it will be difficult to decrypt, ensuring the security of information transmission. Only those with the private key can interpret the information. The U-Shield for bank transactions is the only proof of user identity. When the USB shield is used for the first time, the RSA algorithm is used to generate the private key and save it in the USB shield. In future use, the private key is used to decrypt the transaction information to perform subsequent transaction operations and protect the interests of the user. Nowadays, there are many fake and shoddy products, and companies need to use some anti-counterfeiting methods. At present, the most common one is QR code anti-counterfeiting, which facilitates consumers to verify products through a simple scanning operation. However, if the QR code is displayed in plain text, it will be easily used by criminals. Currently, some people have used the RSA algorithm to encrypt the plain text of the QR code to protect the interests of consumers.The above is the detailed content of The world's most mainstream encryption algorithm. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Enable 256-bit Bitlocker encryption on Windows 11 for increased security
Nov 26, 2023 am 11:21 AM
Enable 256-bit Bitlocker encryption on Windows 11 for increased security
Nov 26, 2023 am 11:21 AM
Bitlocker is the default encryption technology for Windows operating systems. It is widely used on Windows, but some users prefer third-party solutions such as VeraCrypt. What many users of Bitlocker don't know is that it defaults to 128-bit encryption, even though 256-bit is available. Without going into too much detail about the differences; the core difference between AES 128-bit and 256-bit encryption is the length of the security key. Longer keys make brute force attacks more difficult. While the default is 128-bit, even Microsoft recommends 256-bit for better security. The problem is, most users probably don't know about the weaker defaults or how to change them. First, you might want to know W
 Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Win11 encrypted dns detailed tutorial
Dec 25, 2023 am 10:13 AM
Microsoft previously provided dns encryption services for win11, but many users do not know how to use win11 encrypted dns. In fact, we only need to open the dns settings under network settings. Detailed tutorial on win11 encrypted dns: 1. First enter the disk and find the folder you want to encrypt. 2. Then open "Ethernet" on the right 3. Then find the DNS server allocation below and click "Edit" 4. After changing "Auto (DHCP)" to "Manual", open "IPv4" below 5. After turning it on, enter "8.8.8.8" in the preferred DNS 6. Then change the preferred DNS encryption to "Encryption only (DNS over HTTPS)" 7. After the changes are completed, click "Save" and you will find
 Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
Does Win10 Home Edition support folder encryption?
Jan 09, 2024 am 08:58 AM
File encryption aims to implement professional-level encryption of data to more effectively ensure data security! Only by mastering the correct encryption key can the decryption operation be performed, ensuring the security of information assets. However, the file encryption function of Win10 Home Edition does not yet have this feature. Can Win10 Home Edition encrypt folders? Answer: Win10 Home Edition cannot encrypt folders. Tutorial on encrypting files in Windows system 1. Right-click on the file or folder you want to encrypt (or press and hold for a while), and then select the "Properties" function. 2. In the new expanded interface, look for the "Advanced" option. After clicking to enter, remember to check the "Encrypt content to protect data" option located below. 3. After the setting is completed, click "OK" to
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
 Common network communication and security problems and solutions in C#
Oct 09, 2023 pm 09:21 PM
Common network communication and security problems and solutions in C#
Oct 09, 2023 pm 09:21 PM
Common network communication and security problems and solutions in C# In today's Internet era, network communication has become an indispensable part of software development. In C#, we usually encounter some network communication problems, such as data transmission security, network connection stability, etc. This article will discuss in detail common network communication and security issues in C# and provide corresponding solutions and code examples. 1. Network communication problems Network connection interruption: During the network communication process, the network connection may be interrupted, which may cause
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
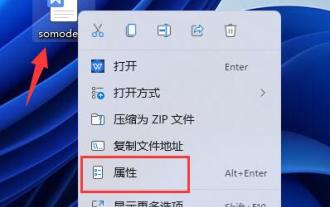 Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Complete guide to win11 file encryption
Jan 09, 2024 pm 02:50 PM
Some friends want to protect their files, but don’t know how to encrypt win11 documents. In fact, we can directly use folder encryption or use third-party software to encrypt files. Detailed tutorial on win11 document encryption: 1. First find the file you want to encrypt, right-click to select it, and open "Properties" 2. Then click "Advanced" in the properties column 3. Select "Encrypt content to protect data" in Advanced and click " OK" 4. Then click "OK" to save. 5. Finally, select the desired encryption mode and "OK" to save the document to encrypt the document.
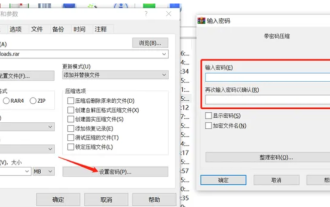 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct



