What kind of security model is firewall technology?
The so-called firewall refers to a protective barrier composed of software and hardware devices and constructed on the boundary between the internal network and the external network, and between the private network and the public network.

A firewall is a technical measure to protect computer network security. It isolates internal and external communications by establishing a corresponding network communication monitoring system at the network boundary. External network to block network intrusions from the outside. (Recommended learning: web front-end video tutorial)
Firewall technology was originally a protective measure taken against Internet network insecurity. As the name suggests, a firewall is an internal network barrier used to block the influence of external insecure factors. Its purpose is to prevent unauthorized access by external network users.
It is a combination of computer hardware and software that establishes a security gateway (Security Gateway) between the Internet and the Internet to protect the internal network from intrusion by illegal users. The firewall is mainly composed of service access policies It consists of four parts, verification tool, packet filtering and application gateway. A firewall is a piece of software or hardware located between a computer and the network it is connected to (hardware firewalls are rarely used and are only used by the Department of Defense and other places because of their price. expensive).
All network traffic to and from this computer must pass through this firewall.
Firewalls include network firewalls and computer firewalls. Network firewall refers to setting up a network firewall between the external network and the internal network. This kind of firewall is also called a filtering router.
The network firewall detects the protocol, destination address, port (network layer) and transmitted information form (application layer) of incoming information, and filters out external information that does not comply with regulations.
Computer firewall refers to setting up a firewall between the external network and the user's computer. Computer firewalls can also be part of the user's computer.
The computer firewall detects the interface procedures, transmission protocols, destination addresses and/or transmitted information structures, etc., and eliminates incoming information that does not meet the regulations. The computer firewall checks the information output by the user's computer and adds the corresponding protocol layer flag to transmit the information to the receiving user's computer (or network).
The benefits of using firewalls include: protecting vulnerable services, controlling access to systems, centralized security management, enhancing confidentiality, recording and counting network utilization data and illegal use of data. There are usually two basic design strategies for firewall design: first, allow any service unless explicitly prohibited; second, prohibit any service unless explicitly permitted. The second strategy is generally used.
From a technical perspective, there are two types of firewalls, namely standard firewalls and dual-hole gateways. Standard firewalls use specialized software and require a relatively high level of management, and there is a certain delay in information transmission.
Dual-hole gateway is an expansion of the standard firewall, also known as the application layer gateway. It is a separate system, but it can complete all the functions of the standard firewall at the same time. Its advantage is that it can run more complex applications while preventing any direct connection between the Internet and internal systems, ensuring that data packets cannot directly reach the internal network from the external network.
The above is the detailed content of What kind of security model is firewall technology?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 Fix: Windows Activation Error 0x87e10bc6 on Windows 11
Apr 19, 2023 pm 01:37 PM
Fix: Windows Activation Error 0x87e10bc6 on Windows 11
Apr 19, 2023 pm 01:37 PM
The Windows 11 activation error 0x87e10bc6 issue occurs when some users try to activate the platform using a product key through settings. When this issue occurs, the Activation tab in Settings displays the following error message: Something is preventing us from communicating with the activation server. Wait a few minutes and try again. Error code: 0x87e10bc6. Specific activation errors may occur because a firewall blocks the connection to Microsoft's activation servers. Therefore, when this error occurs, users cannot activate Windows 11 using their product key. Unfortunately, even Windows 10 users have been plagued by the same issue in the past, so prepare for the benefits
 How to fix 'Error: 0x80070185, Cloud operation was unsuccessful” in OneDrive
May 16, 2023 pm 04:26 PM
How to fix 'Error: 0x80070185, Cloud operation was unsuccessful” in OneDrive
May 16, 2023 pm 04:26 PM
OneDrive is a popular cloud storage application provided by Microsoft. Most of us use OneDrive to store our files, folders, documents, etc. But some users complained that when they try to access shared files on OneDrive, it gives an error stating “Error: 0x80070185, Cloud operation was unsuccessful”. Therefore, they cannot perform any operations on OneDrive such as copying files, pasting, downloading shared files, etc. Nowadays, it is necessary to use these operations in our daily work. This error can be easily solved and for this we have some methods that we can apply and try to solve the problem. let's start! Method 1 – Sign out and sign back in to OneDrive app steps
 8 Big Fixes if Grammarly Not Working on Windows 10 Browser
May 05, 2023 pm 02:16 PM
8 Big Fixes if Grammarly Not Working on Windows 10 Browser
May 05, 2023 pm 02:16 PM
If you have syntax issues on your Windows 10 or 11 PC, this article will help you solve the problem. Grammarly is one of the most popular typing assistants for fixing grammar, spelling, clarity, and more. It has become an essential part of writing professionals. However, if it doesn't work properly, it can be a very frustrating experience. Many Windows users have reported that this tool does not work well on their computers. We did an in-depth analysis and found the cause and solution of this problem. Why doesn't Grammarly work on my PC? Grammarly on PC may not work properly due to several common reasons. It includes the following
 Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
Win11 firewall advanced settings gray solution
Dec 24, 2023 pm 07:53 PM
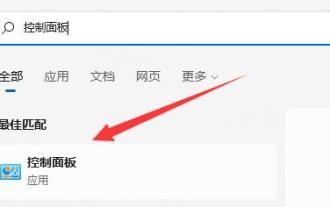
When setting up the firewall, many friends found that their win11 firewall advanced settings were grayed out and unable to be clicked. This may be caused by not adding a control unit, or by not opening the advanced settings in the correct way. Let’s take a look at how to solve it. Win11 firewall advanced settings gray method one: 1. First, click the start menu below, search and open "Control Panel" at the top 2. Then open "Windows Defender Firewall" 3. After entering, you can open "Advanced Settings" in the left column . Method 2: 1. If the above method cannot be opened, you can right-click "Start Menu" and open "Run" 2. Then enter "mmc" and press Enter to confirm opening. 3. After opening, click on the upper left
 How to Fix Steam Error Code 130 on Windows PC
Apr 28, 2023 pm 01:40 PM
How to Fix Steam Error Code 130 on Windows PC
Apr 28, 2023 pm 01:40 PM
Steam is a popular online game streaming platform that allows its users to purchase and play games as well as chat with other gamers on the platform. In addition to the features it offers, there are also some bugs encountered on the platform. One such error encountered by many Steam users is “Error code: 130 The webpage cannot be loaded (Unknown error)”. This error occurs when the Steam client attempts to load a web page but is unable to retrieve the page from its server. This error code may appear on any page in the Steam client, including inventory pages, update news, or store pages that prevent you from searching for a game you're interested in purchasing. One of the main reasons for this problem is a weak internet connection on your PC. Other possible causes are Stea
 Fix: Windows 11 Firewall blocks printer
May 01, 2023 pm 08:28 PM
Fix: Windows 11 Firewall blocks printer
May 01, 2023 pm 08:28 PM
Firewalls monitor network traffic and can block network connections for certain programs and hardware. Windows 11 includes its own Windows Defender Firewall, which may block printers from accessing the web. Therefore, affected users cannot use their Brother printers when the firewall blocks it. Keep in mind that this issue affects other brands as well, but today we’ll show you how to fix it. Why is my Brother printer blocked by the firewall? There are several causes for this issue, and you will most likely need to open certain ports before your printer can access the network. Printer software can also cause problems, so be sure to update it as well as your printer driver. Read on to learn how
 How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
How to enable or disable firewall on Alpine Linux?
Feb 21, 2024 pm 12:45 PM
On AlpineLinux, you can use the iptables tool to configure and manage firewall rules. Here are the basic steps to enable or disable the firewall on AlpineLinux: Check the firewall status: sudoiptables -L If the output shows rules (for example, there are some INPUT, OUTPUT, or FORWARD rules), the firewall is enabled. If the output is empty, the firewall is currently disabled. Enable firewall: sudoiptables-PINPUTACCEPTsudoiptables-POUTPUTACCEPTsudoiptables-PFORWARDAC
 Resolve error code 0xc004f074 when activating Windows 11.
May 08, 2023 pm 07:10 PM
Resolve error code 0xc004f074 when activating Windows 11.
May 08, 2023 pm 07:10 PM
After installing the latest operating system on your PC, activating your copy of Windows 11 is the main job. Not only does it unlock the true potential of the Windows 11 operating system, but it also gets rid of the annoying "Activate your Windows 11" message. However, for some users, Windows 11 activation error 0xc004f074 hinders the smooth progress of activation. This bug apparently prevents users from activating Windows 11 and forces them to use an operating system with limited functionality. Windows 11 activation error code 0xc004f074 is related to the Key Management Service. You will encounter this problem when KMS is unavailable. Okay, that's it for this tutorial



