PHPCMS various injection vulnerability patches

1. Wide byte injection vulnerability
/phpcms/modules/pay/respond.php Location is about 16 Line
original code
$payment = $this->get_by_code($_GET['code']);
is replaced with
$payment = $this->get_by_code(mysql_real_escape_string($_GET['code']));
2. phpcms injection vulnerability
/phpcms/modules/poster/poster .php position is about 221 lines after
if ($_GET['group']) {, add
$_GET['group'] = preg_replace('#`#', '', $_GET['group']);
3, phpcms front-end injection leads to arbitrary file reading vulnerability patch
/phpcms/ modules/content/down.php
(1) Replace line 17
parse_str($a_k);
with
$a_k = safe_replace($a_k); parse_str($a_k);
(2) Line 89
parse_str($a_k);
Replace with
$a_k = safe_replace($a_k); parse_str($a_k);
(3) and add
$filename = date('Ymd_his').random(3).'.'.$ext;
# after line 120 of position 3.
$fileurl = str_replace(array('<','>'), '',$fileurl);
4, phpcms injection vulnerability
/phpcms/modules/member/index.php is located at about 615 lines
Original code:
$password = isset($_POST['password']) && trim($_POST['password']) ? trim($_POST['password']) : showmessage(L('password_empty'),HTTP_REFERER);
Replaced with:
$password = isset($_POST['password']) && trim($_POST['password']) ? addslashes(urldecode(trim($_POST['password'] ))) : showmessage(L('password_empty'), HTTP_REFERER);
5, PHPCMS V9.6.2 SQL Injection vulnerability
(1) phpcms/libs/classes/param.class.php is located at about line 109
The original code
$value = isset($_COOKIE[$var]) ? sys_auth($_COOKIE[$var], 'DECODE') : $default;
is replaced with
$value = isset($_COOKIE[$var])?addslashes(sys_auth($_COOKIE[$var],'DECODE')):$default;
(2)/phpsso_server/phpcms/libs/classes/param.class.php is located at about 108 lines
The original code
return isset($_COOKIE[$var]) ? sys_auth($_COOKIE[$var], 'DECODE') : $default;
is replaced with
return isset($_COOKIE[$var]) ? addslashes(sys_auth($_COOKIE[$var],'DECODE')) : $default;
6. A logical problem somewhere in phpcms caused getshell
/phpcms/libs/classes/attachment.class.php to be located at line 143 of
function download($field, $value,$watermark = '0',$ext = 'gif|jpg|jpeg|bmp|png', $absurl = '', $basehref = ''){followed by
$extArray=explode('|',$ext);
if(!empty($extArray) && is_array($extArray)){
foreach($extArray as $k => $v){
if(!in_array(strtolower($v), array('gif','jpg','jpeg','bmp','png'))); exit('0');//循环判断如果
有一个不符合,直接返回 0
}
}In this way, add a judgment. If the allowed file formats are 'gif', 'jpg', 'jpeg', 'bmp', 'png', continue, otherwise it will jump out. Of course, the formats here can be increased as needed. several.
7. phpcms injection vulnerability
/api/phpsso.php is located at about 128 lines
The original code
$arr['uid'] = intval($arr['uid']); $phpssouid = $arr['uid'];
is replaced by , two-in-one code
$phpssouid = intval($arr['uid']);
8. phpcms authkey generation algorithm problem leads to authkey leakage
Follow the following function to regenerate the key value, and then find caches/configs Just replace the two parameters in /system.php and it will be ok
<?php
function random($length, $chars = '0123456789') {
$hash = '';
$max = strlen($chars) - 1;
for($i = 0; $i < $length; $i++) {
$hash .= $chars[mt_rand(0, $max)];
}
return $hash;
}
echo random(20, 'authkey').'<br/>';
echo random(32, 'phpssoauthkey');exit;
?>PHP Chinese website, a large number of free PHPCMS tutorials, welcome to learn online!
The above is the detailed content of PHPCMS various injection vulnerability patches. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Jailbreak any large model in 20 steps! More 'grandma loopholes' are discovered automatically
Nov 05, 2023 pm 08:13 PM
Jailbreak any large model in 20 steps! More 'grandma loopholes' are discovered automatically
Nov 05, 2023 pm 08:13 PM
In less than a minute and no more than 20 steps, you can bypass security restrictions and successfully jailbreak a large model! And there is no need to know the internal details of the model - only two black box models need to interact, and the AI can fully automatically defeat the AI and speak dangerous content. I heard that the once-popular "Grandma Loophole" has been fixed: Now, facing the "Detective Loophole", "Adventurer Loophole" and "Writer Loophole", what response strategy should artificial intelligence adopt? After a wave of onslaught, GPT-4 couldn't stand it anymore, and directly said that it would poison the water supply system as long as... this or that. The key point is that this is just a small wave of vulnerabilities exposed by the University of Pennsylvania research team, and using their newly developed algorithm, AI can automatically generate various attack prompts. Researchers say this method is better than existing
 Buffer overflow vulnerability in Java and its harm
Aug 09, 2023 pm 05:57 PM
Buffer overflow vulnerability in Java and its harm
Aug 09, 2023 pm 05:57 PM
Buffer overflow vulnerabilities in Java and their harm Buffer overflow means that when we write more data to a buffer than its capacity, it will cause data to overflow to other memory areas. This overflow behavior is often exploited by hackers, which can lead to serious consequences such as abnormal code execution and system crash. This article will introduce buffer overflow vulnerabilities and their harm in Java, and give code examples to help readers better understand. The buffer classes widely used in Java include ByteBuffer, CharBuffer, and ShortB
 Error 87 prevents kb4474419 patch from being installed
Jan 03, 2024 pm 03:28 PM
Error 87 prevents kb4474419 patch from being installed
Jan 03, 2024 pm 03:28 PM
If there is a problem with the kb4474419 patch, automatic updates cannot be performed. Generally speaking, it is solved by re-downloading the patch and installing it. However, many friends reported that they encountered installation errors. In fact, the solution is very simple. Let’s take a look. kb4474419 patch installation error 87: 1. First, click on the portal to download the latest kb4474419 patch. 2. Unzip the downloaded compressed package resources. 3. You can use the shortcut key "win+R" to open the command prompt, and then enter "cmd". You can also enter "command prompt" in the system search and run it as an administrator. 4. First enter C:\Windows\System32 and enter
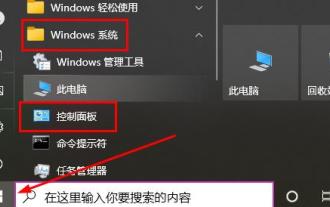 How to uninstall Win10 patches
Dec 25, 2023 pm 08:49 PM
How to uninstall Win10 patches
Dec 25, 2023 pm 08:49 PM
After the system is patched, these patches will remain in the computer and will occupy a lot of memory over time. Therefore, many users want to know how to uninstall win10 patches. It is actually very simple. Let’s take a look. How to uninstall the win10 patch: 1. First click on the lower left corner to start, then find "Windows System" and open the "Control Panel". 2. Then click "Uninstall a program" below. 3. Then click "View installed updates" on the left. 4. Now you can see all the patches, right-click and click "Uninstall".
 The OpenAI DALL-E 3 model has a vulnerability that generates 'inappropriate content.' A Microsoft employee reported it and was slapped with a 'gag order.'
Feb 04, 2024 pm 02:40 PM
The OpenAI DALL-E 3 model has a vulnerability that generates 'inappropriate content.' A Microsoft employee reported it and was slapped with a 'gag order.'
Feb 04, 2024 pm 02:40 PM
According to news on February 2, Shane Jones, manager of Microsoft’s software engineering department, recently discovered a vulnerability in OpenAI’s DALL-E3 model, which is said to be able to generate a series of inappropriate content. Shane Jones reported the vulnerability to the company, but was asked to keep it confidential. However, he eventually decided to disclose the vulnerability to the outside world. ▲Image source: Report disclosed by ShaneJones. This site noticed that ShaneJones discovered through independent research in December last year that there was a vulnerability in the DALL-E3 model of OpenAI text-generated images. This vulnerability can bypass the AI Guardrail (AIGuardrail), resulting in the generation of a series of NSFW inappropriate content. This discovery attracted widespread attention
 Comma operator vulnerabilities and protective measures in Java
Aug 10, 2023 pm 02:21 PM
Comma operator vulnerabilities and protective measures in Java
Aug 10, 2023 pm 02:21 PM
Overview of Comma Operator Vulnerabilities and Defense Measures in Java: In Java programming, we often use the comma operator to perform multiple operations at the same time. However, sometimes we may overlook some potential vulnerabilities of the comma operator that may lead to unexpected results. This article will introduce the vulnerabilities of the comma operator in Java and provide corresponding protective measures. Usage of comma operator: The syntax of comma operator in Java is expr1, expr2, which can be said to be a sequence operator. Its function is to first calculate ex
 What to do if Win7 update patch prompts error code 0x80070643
Jun 29, 2023 pm 12:58 PM
What to do if Win7 update patch prompts error code 0x80070643
Jun 29, 2023 pm 12:58 PM
What should I do if the Win7 update patch prompts error code 0x80070643? Win7 system upgrade is a way of daily maintenance of Windows. We often install the latest update patches on computers to strengthen the system. However, recently some Win7 users have encountered the error code 0x80070643 when updating patches. So how to solve it? Woolen cloth? Many friends don’t know how to operate in detail. The editor has compiled the solutions to the Win7 update patch prompt error code 0x80070643. If you are interested, follow the editor to take a look below! Solution to the Win7 update patch error code 0x80070643 1. Open the Start menu on the desktop.
 What framework is phpcms?
Apr 20, 2024 pm 10:51 PM
What framework is phpcms?
Apr 20, 2024 pm 10:51 PM
PHP CMS is a PHP-based open source content management system for managing website content. Its features include ease of use, powerful functionality, scalability, high security, and free open source. It can save time, improve website quality, enhance collaboration and reduce development costs, and is widely used in various websites such as news websites, blogs, corporate websites, e-commerce websites and community forums.






