Apache server security settings

Securing your web server is very important, which means allowing others to view only some of the information and protecting the data and limiting access.
These are common things to enhance the security of your Apache web server. (Recommended learning: Apache Server)
1. Hide Apache version and operating system information. Apache displays its version and operating system name incorrectly, as shown below Screen shot shown.
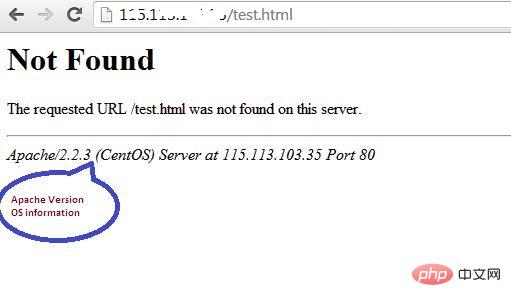
#Hackers can use this information to launch attacks using exposed vulnerabilities in specific versions of servers or operating systems. To prevent Apache webserver from displaying this information, we can modify the server signature option provided in the apache configuration file. By default it is on, set it to off.
vim /etc/httpd/conf/httpd.conf<br/>
The modification is:
ServerSignature Off<br/>ServerTokens Prod<br/>
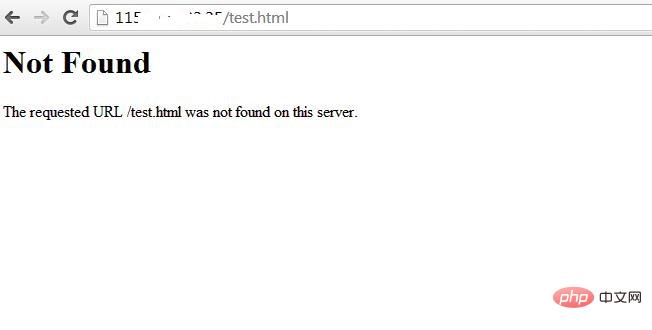
We also set up "ServerTokens Prod", which tells the web server to only return apache and prohibits operating system major and minor versions . After modifying the configuration file, the Apache web server must be restarted/reloaded for it to take effect.
service httpd restart<br/>
After modifying and restarting the Apache server, you should see similar results -
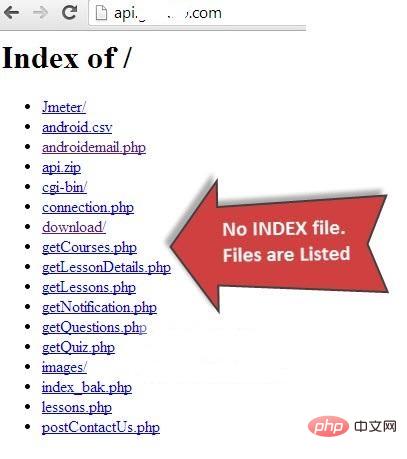
2. Disable directory listing
If there is no index file in the document root directory (such as: index.html, index.php, index.html, etc.), then by default, the apache web server will display all the contents of the document root directory.
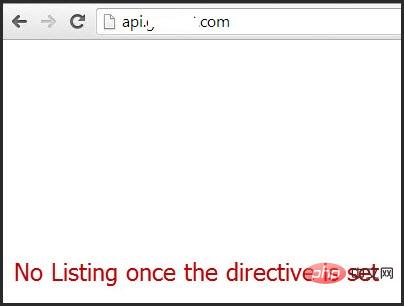
This feature can be turned off for a specific directory through the options directive provided in the Apache configuration file.
<Directory /var/www/html><br/> Options -Indexes<br/></Directory><br/>
3. Disable unnecessary modules
It is best to disable all unused unnecessary modules, you can See the list of enabled modules in the apache configuration file -
[root@amsterdam ~]#httpd –M<br/>perl_module (shared)<br/>php5_module (shared)<br/>proxy_ajp_module (shared)<br/>python_module (shared)<br/>ssl_module (shared)<br/>
Many of the listed modules can be disabled like mod_imap, mod_include, mod_info, mod_userdir, mod_autoindex as they are hardly used by any production Used by web server.
vi /etc/httpd/conf/httpd.conf<br/>
Then comment out -
#LoadModule auth_digest_module modules/mod_auth_digest.so<br/>
After commenting the module, save the file. Use the following command to restart the apache service.
/etc/init.d/httpd restart/<br/>
4. Use mod_evasive to counter DoS attacks
If you want to protect your web server from DoS (i.e. Denial of Service), you must enable the module mod_evasive. It is a third-party module that detects DoS attacks and prevents them from causing damage far beyond the course of their operation.
5. Limit request size
Apache does not have any limit on the total size of http requests that may lead to a DoS attack. The request size of the Apache directive LimitRequestBody can be limited using directory tags.
Depending on the requirements, this value can be set from 0 to 2GB (i.e. 2147483647 bytes).
<Directory "/var/www/html/uploads"><br/> LimitRequestBody 512000<br/></Directory><br/>
The above is the detailed content of Apache server security settings. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How to run the h5 project
Apr 06, 2025 pm 12:21 PM
How to run the h5 project
Apr 06, 2025 pm 12:21 PM
Running the H5 project requires the following steps: installing necessary tools such as web server, Node.js, development tools, etc. Build a development environment, create project folders, initialize projects, and write code. Start the development server and run the command using the command line. Preview the project in your browser and enter the development server URL. Publish projects, optimize code, deploy projects, and set up web server configuration.
 How to export pdf with xml
Apr 03, 2025 am 06:45 AM
How to export pdf with xml
Apr 03, 2025 am 06:45 AM
There are two ways to export XML to PDF: using XSLT and using XML data binding libraries. XSLT: Create an XSLT stylesheet, specify the PDF format to convert XML data using the XSLT processor. XML Data binding library: Import XML Data binding library Create PDF Document object loading XML data export PDF files. Which method is better for PDF files depends on the requirements. XSLT provides flexibility, while the data binding library is simple to implement; for simple conversions, the data binding library is better, and for complex conversions, XSLT is more suitable.
 Apache Troubleshooting: Diagnosing & Resolving Common Errors
Apr 03, 2025 am 12:07 AM
Apache Troubleshooting: Diagnosing & Resolving Common Errors
Apr 03, 2025 am 12:07 AM
Apache errors can be diagnosed and resolved by viewing log files. 1) View the error.log file, 2) Use the grep command to filter errors in specific domain names, 3) Clean the log files regularly and optimize the configuration, 4) Use monitoring tools to monitor and alert in real time. Through these steps, Apache errors can be effectively diagnosed and resolved.
 How to generate pom.xml
Apr 03, 2025 am 06:00 AM
How to generate pom.xml
Apr 03, 2025 am 06:00 AM
There are the following ways to generate a pom.xml file: Use Maven Archetype to provide predefined project templates to automatically generate pom.xml files for specific types of projects. Use the Maven Helper plugin to provide commands to generate pom.xml files. Create manually to customize the pom.xml file for the project.
 How to set character encoding on the server side to solve Bootstrap Table garbled
Apr 07, 2025 pm 12:00 PM
How to set character encoding on the server side to solve Bootstrap Table garbled
Apr 07, 2025 pm 12:00 PM
To set character encoding on the server side to solve the garbled Bootstrap Table, you need to follow the following steps: check the server character encoding; edit the server configuration file; set the character encoding to UTF-8; save and restart the server; verify the encoding.
 How to preview the Bootstrap page
Apr 07, 2025 am 10:06 AM
How to preview the Bootstrap page
Apr 07, 2025 am 10:06 AM
The preview methods of Bootstrap pages are: open the HTML file directly in the browser; automatically refresh the browser using the Live Server plug-in; and build a local server to simulate an online environment.
 Cannot start mysql in xampp
Apr 08, 2025 pm 03:15 PM
Cannot start mysql in xampp
Apr 08, 2025 pm 03:15 PM
There are many reasons why XAMPP fails to start MySQL, including port conflicts, configuration file errors, insufficient system permissions, service dependency issues, and installation issues. The troubleshooting steps are as follows: 1) Check port conflicts; 2) Check configuration files; 3) Check system permissions; 4) Check service dependencies; 5) Reinstall MySQL. Follow these steps and you can find and resolve issues that cause MySQL startup to fail.
 Summary of phpmyadmin vulnerabilities
Apr 10, 2025 pm 10:24 PM
Summary of phpmyadmin vulnerabilities
Apr 10, 2025 pm 10:24 PM
The key to PHPMyAdmin security defense strategy is: 1. Use the latest version of PHPMyAdmin and regularly update PHP and MySQL; 2. Strictly control access rights, use .htaccess or web server access control; 3. Enable strong password and two-factor authentication; 4. Back up the database regularly; 5. Carefully check the configuration files to avoid exposing sensitive information; 6. Use Web Application Firewall (WAF); 7. Carry out security audits. These measures can effectively reduce the security risks caused by PHPMyAdmin due to improper configuration, over-old version or environmental security risks, and ensure the security of the database.




