thinkphp6 arbitrary file creation vulnerability reappears
01 Background
QiAnXin recently released a security risk notice for the "arbitrary" file creation vulnerability in ThinkPHP 6.0. In response, DYSRC immediately analyzed the vulnerability and successfully Reproduce the vulnerability.
Vulnerability scope: top-think/framework 6.x
02 Location problem
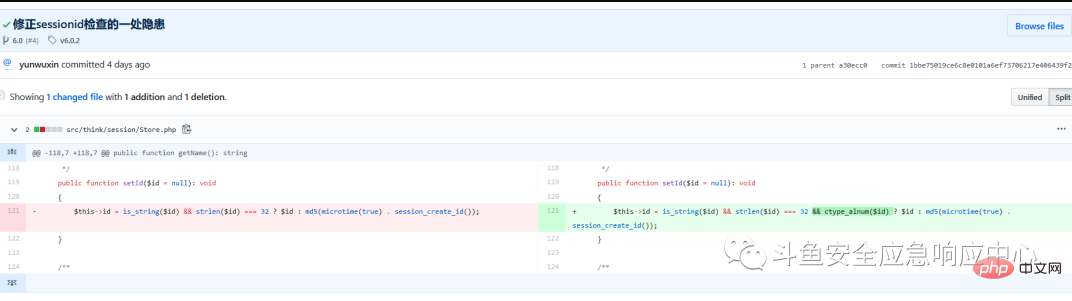
Based on the creation of arbitrary files and recent commit history, it can be inferred that 1bbe75019 is the patch for this problem. It can be seen that the patch restricts the sessionid to only consist of letters and numbers, which makes the problem more obvious.
03 Principle Analysis
Putting aside the above issues first, let’s take a look at how thinkphp stores sessions.
The system defines the interface thinkcontractSessionHandlerInterface
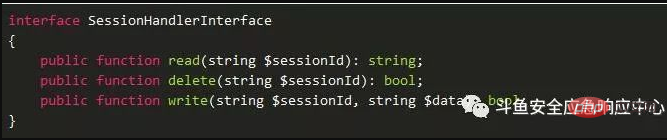
SessionHandlerInterface::write method is executed when localizing session data, and the system will automatically execute it at the end of each request. implement.
Let’s take a look at how the thinksessiondriverFile class is implemented.
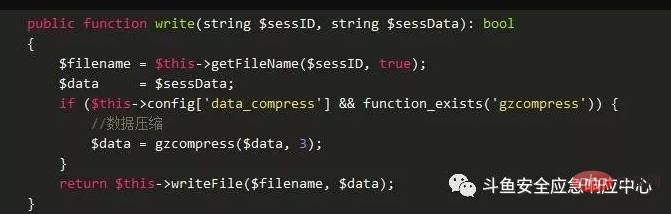
First generate the file name based on $sessID through getFileName, and then writeFile to write the file.
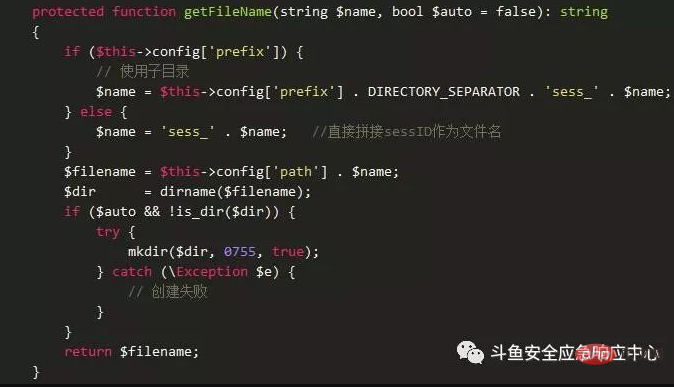
Follow up getFileName and directly concatenate the incoming $sessID as the file name. Since $sessID is controllable, the file name is controllable.
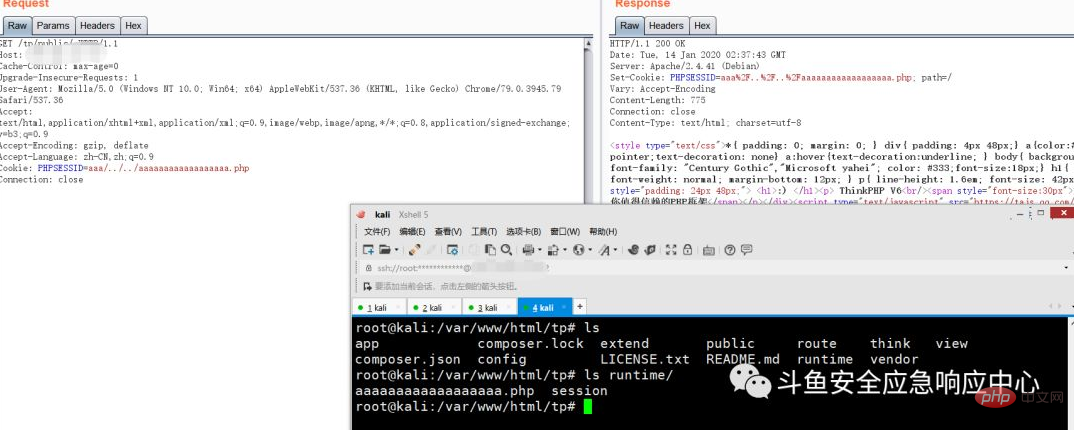
04 Demonstration
At this point in the analysis, the entire vulnerability process is basically clear. The local demonstration results are given below.
php Chinese website, a large number of free thinkphp introductory tutorials, welcome to learn online!
The above is the detailed content of thinkphp6 arbitrary file creation vulnerability reappears. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 What Are the Key Considerations for Using ThinkPHP in a Serverless Architecture?
Mar 18, 2025 pm 04:54 PM
What Are the Key Considerations for Using ThinkPHP in a Serverless Architecture?
Mar 18, 2025 pm 04:54 PM
The article discusses key considerations for using ThinkPHP in serverless architectures, focusing on performance optimization, stateless design, and security. It highlights benefits like cost efficiency and scalability, but also addresses challenges
 What Are the Advanced Features of ThinkPHP's Dependency Injection Container?
Mar 18, 2025 pm 04:50 PM
What Are the Advanced Features of ThinkPHP's Dependency Injection Container?
Mar 18, 2025 pm 04:50 PM
ThinkPHP's IoC container offers advanced features like lazy loading, contextual binding, and method injection for efficient dependency management in PHP apps.Character count: 159
 How to Build a Distributed Task Queue System with ThinkPHP and RabbitMQ?
Mar 18, 2025 pm 04:45 PM
How to Build a Distributed Task Queue System with ThinkPHP and RabbitMQ?
Mar 18, 2025 pm 04:45 PM
The article outlines building a distributed task queue system using ThinkPHP and RabbitMQ, focusing on installation, configuration, task management, and scalability. Key issues include ensuring high availability, avoiding common pitfalls like imprope
 What Are the Key Features of ThinkPHP's Built-in Testing Framework?
Mar 18, 2025 pm 05:01 PM
What Are the Key Features of ThinkPHP's Built-in Testing Framework?
Mar 18, 2025 pm 05:01 PM
The article discusses ThinkPHP's built-in testing framework, highlighting its key features like unit and integration testing, and how it enhances application reliability through early bug detection and improved code quality.
 How can I prevent SQL injection vulnerabilities in ThinkPHP?
Mar 14, 2025 pm 01:18 PM
How can I prevent SQL injection vulnerabilities in ThinkPHP?
Mar 14, 2025 pm 01:18 PM
The article discusses preventing SQL injection vulnerabilities in ThinkPHP through parameterized queries, avoiding raw SQL, using ORM, regular updates, and proper error handling. It also covers best practices for securing database queries and validat
 What Are the Key Differences Between ThinkPHP 5 and ThinkPHP 6, and When to Use Each?
Mar 14, 2025 pm 01:30 PM
What Are the Key Differences Between ThinkPHP 5 and ThinkPHP 6, and When to Use Each?
Mar 14, 2025 pm 01:30 PM
The article discusses key differences between ThinkPHP 5 and 6, focusing on architecture, features, performance, and suitability for legacy upgrades. ThinkPHP 5 is recommended for traditional projects and legacy systems, while ThinkPHP 6 suits new pr
 How to Implement Service Discovery and Load Balancing in ThinkPHP Microservices?
Mar 18, 2025 pm 04:51 PM
How to Implement Service Discovery and Load Balancing in ThinkPHP Microservices?
Mar 18, 2025 pm 04:51 PM
The article discusses implementing service discovery and load balancing in ThinkPHP microservices, focusing on setup, best practices, integration methods, and recommended tools.[159 characters]
 What Are the Best Ways to Handle File Uploads and Cloud Storage in ThinkPHP?
Mar 17, 2025 pm 02:28 PM
What Are the Best Ways to Handle File Uploads and Cloud Storage in ThinkPHP?
Mar 17, 2025 pm 02:28 PM
The article discusses best practices for handling file uploads and integrating cloud storage in ThinkPHP, focusing on security, efficiency, and scalability.




