Network security related knowledge

Network security related knowledge
Five ways to steal secret attacks
Footprinting: The attacker collects the target's information in advance and usually uses tools such as Whois, Finger, Nslookup, and Ping to obtain some of the target's information, such as domain name, IP address, network topology, related user information, etc. These are often the first steps for hackers to invade;
Scanning: Scanning here mainly refers to port scanning. Nmap and other port scanning tools are usually used to obtain some useful information about the target computer. Information, such as which ports are opened on the machine, will know which network services are opened. Hackers can exploit these server-side vulnerabilities to conduct further intrusions. This is often the second step in a hacker's intrusion.
Protocol stack fingerprinting (Stack Fingerprinting) identification (also called operating system detection): Hackers send detection packets to the target host. Since there are many subtle differences between the IP protocol stack implementations of different OS manufacturers, each OS Each has its own unique response method, and hackers are often able to determine the OS the target host is running. This can often be seen as part of the scanning phase.
Information flow sniffing (Sniffering): By setting a host's network card to promiscuous mode in a shared LAN, or using ARP spoofing in various LANs, the host will accept all passing data packets. Based on this principle, hackers can use a sniffer (hardware or software) to monitor network information flow and collect information such as account numbers and passwords. This is the third step of hacking.
Session Hijacking: The so-called session hijacking means that during a normal communication process, a hacker participates as a third party, or injects additional information into the data stream, or inserts the information of both parties into the process. The communication model secretly changes, that is, from direct contact to being relayed by hackers. This attack method can be considered as the fourth step of hacking - one of the real attacks.
What is a firewall? Why do you need a firewall?
A firewall is a device, which is a combination of software and hardware equipment. It is usually located between an enterprise's internal LAN and the Internet. It restricts Internet users' access to the internal network and manages internal user access. Internet permissions.
In other words, a firewall provides a blocking tool between an internal network that is considered safe and trusted and an external network that is considered less secure and trustworthy. If there is no firewall, the security of the entire internal network completely depends on each host. Therefore, all hosts must achieve a consistent high level of security, which is very difficult in actual operation.
The firewall is designed as a device running dedicated access control software and has no other services, so it means there are relatively few defects and security holes, which makes security management more convenient. Ease of control will also make internal networks more secure. The principle followed by the firewall is to ensure the security of the internal network as much as possible while ensuring the smooth flow of the network. It is a static security component.
What are the limitations of firewalls?
Some attacks on the network can bypass the firewall
Firewalls cannot prevent attacks from the internal network.
Firewalls cannot protect the transmission of virus-infected programs and files.
Firewalls cannot protect against new online threats.
When using end-to-end encryption, the role of the firewall will be greatly limited.
Firewalls are not completely transparent to users and may cause problems such as transmission delays, bottlenecks, and single points of failure.
Firewalls cannot protect against data-driven attacks.
The above is the detailed content of Network security related knowledge. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to adjust MTU size on Windows 11
Aug 25, 2023 am 11:21 AM
How to adjust MTU size on Windows 11
Aug 25, 2023 am 11:21 AM
If you're suddenly experiencing a slow internet connection on Windows 11 and you've tried every trick in the book, it might have nothing to do with your network and everything to do with your maximum transmission unit (MTU). Problems may occur if your system sends or receives data with the wrong MTU size. In this post, we will learn how to change MTU size on Windows 11 for smooth and uninterrupted internet connection. What is the default MTU size in Windows 11? The default MTU size in Windows 11 is 1500, which is the maximum allowed. MTU stands for maximum transmission unit. This is the maximum packet size that can be sent or received on the network. every support network
![WLAN expansion module has stopped [fix]](https://img.php.cn/upload/article/000/465/014/170832352052603.gif?x-oss-process=image/resize,m_fill,h_207,w_330) WLAN expansion module has stopped [fix]
Feb 19, 2024 pm 02:18 PM
WLAN expansion module has stopped [fix]
Feb 19, 2024 pm 02:18 PM
If there is a problem with the WLAN expansion module on your Windows computer, it may cause you to be disconnected from the Internet. This situation is often frustrating, but fortunately, this article provides some simple suggestions that can help you solve this problem and get your wireless connection working properly again. Fix WLAN Extensibility Module Has Stopped If the WLAN Extensibility Module has stopped working on your Windows computer, follow these suggestions to fix it: Run the Network and Internet Troubleshooter to disable and re-enable wireless network connections Restart the WLAN Autoconfiguration Service Modify Power Options Modify Advanced Power Settings Reinstall Network Adapter Driver Run Some Network Commands Now, let’s look at it in detail
 How to solve win11 DNS server error
Jan 10, 2024 pm 09:02 PM
How to solve win11 DNS server error
Jan 10, 2024 pm 09:02 PM
We need to use the correct DNS when connecting to the Internet to access the Internet. In the same way, if we use the wrong dns settings, it will prompt a dns server error. At this time, we can try to solve the problem by selecting to automatically obtain dns in the network settings. Let’s take a look at the specific solutions. How to solve win11 network dns server error. Method 1: Reset DNS 1. First, click Start in the taskbar to enter, find and click the "Settings" icon button. 2. Then click the "Network & Internet" option command in the left column. 3. Then find the "Ethernet" option on the right and click to enter. 4. After that, click "Edit" in the DNS server assignment, and finally set DNS to "Automatic (D
 Fix 'Failed Network Error' downloads on Chrome, Google Drive and Photos!
Oct 27, 2023 pm 11:13 PM
Fix 'Failed Network Error' downloads on Chrome, Google Drive and Photos!
Oct 27, 2023 pm 11:13 PM
What is the "Network error download failed" issue? Before we delve into the solutions, let’s first understand what the “Network Error Download Failed” issue means. This error usually occurs when the network connection is interrupted during downloading. It can happen due to various reasons such as weak internet connection, network congestion or server issues. When this error occurs, the download will stop and an error message will be displayed. How to fix failed download with network error? Facing “Network Error Download Failed” can become a hindrance while accessing or downloading necessary files. Whether you are using browsers like Chrome or platforms like Google Drive and Google Photos, this error will pop up causing inconvenience. Below are points to help you navigate and resolve this issue
 Fix: WD My Cloud doesn't show up on the network in Windows 11
Oct 02, 2023 pm 11:21 PM
Fix: WD My Cloud doesn't show up on the network in Windows 11
Oct 02, 2023 pm 11:21 PM
If WDMyCloud is not showing up on the network in Windows 11, this can be a big problem, especially if you store backups or other important files in it. This can be a big problem for users who frequently need to access network storage, so in today's guide, we'll show you how to fix this problem permanently. Why doesn't WDMyCloud show up on Windows 11 network? Your MyCloud device, network adapter, or internet connection is not configured correctly. The SMB function is not installed on the computer. A temporary glitch in Winsock can sometimes cause this problem. What should I do if my cloud doesn't show up on the network? Before we start fixing the problem, you can perform some preliminary checks:
 What should I do if the earth is displayed in the lower right corner of Windows 10 when I cannot access the Internet? Various solutions to the problem that the Earth cannot access the Internet in Win10
Feb 29, 2024 am 09:52 AM
What should I do if the earth is displayed in the lower right corner of Windows 10 when I cannot access the Internet? Various solutions to the problem that the Earth cannot access the Internet in Win10
Feb 29, 2024 am 09:52 AM
This article will introduce the solution to the problem that the globe symbol is displayed on the Win10 system network but cannot access the Internet. The article will provide detailed steps to help readers solve the problem of Win10 network showing that the earth cannot access the Internet. Method 1: Restart directly. First check whether the network cable is not plugged in properly and whether the broadband is in arrears. The router or optical modem may be stuck. In this case, you need to restart the router or optical modem. If there are no important things being done on the computer, you can restart the computer directly. Most minor problems can be quickly solved by restarting the computer. If it is determined that the broadband is not in arrears and the network is normal, that is another matter. Method 2: 1. Press the [Win] key, or click [Start Menu] in the lower left corner. In the menu item that opens, click the gear icon above the power button. This is [Settings].
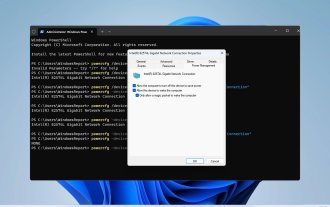 How to enable/disable Wake on LAN in Windows 11
Sep 06, 2023 pm 02:49 PM
How to enable/disable Wake on LAN in Windows 11
Sep 06, 2023 pm 02:49 PM
Wake on LAN is a network feature on Windows 11 that allows you to remotely wake your computer from hibernation or sleep mode. While casual users don't use it often, this feature is useful for network administrators and power users using wired networks, and today we'll show you how to set it up. How do I know if my computer supports Wake on LAN? To use this feature, your computer needs the following: The PC needs to be connected to an ATX power supply so that you can wake it from sleep mode remotely. Access control lists need to be created and added to all routers in the network. The network card needs to support the wake-up-on-LAN function. For this feature to work, both computers need to be on the same network. Although most Ethernet adapters use
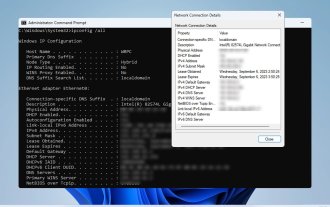 How to check network connection details and status on Windows 11
Sep 11, 2023 pm 02:17 PM
How to check network connection details and status on Windows 11
Sep 11, 2023 pm 02:17 PM
In order to make sure your network connection is working properly or to fix the problem, sometimes you need to check the network connection details on Windows 11. By doing this, you can view a variety of information including your IP address, MAC address, link speed, driver version, and more, and in this guide, we'll show you how to do that. How to find network connection details on Windows 11? 1. Use the "Settings" app and press the + key to open Windows Settings. WindowsI Next, navigate to Network & Internet in the left pane and select your network type. In our case, this is Ethernet. If you are using a wireless network, select a Wi-Fi network instead. At the bottom of the screen you should see





