How does HTTPS ensure security? (detailed explanation)
This article will take you through the problems of HTTP and introduce how HTTPS ensures security. It has certain reference value. Friends in need can refer to it. I hope it will be helpful to everyone.

Problems with HTTP
1, Eavesdropping risk: Communication use Plain text (not encrypted), the content may be eavesdropped (a third party may learn the communication content)
2, Risk of impersonation: The identity of the communicating party is not verified, so there is a possibility of encountering disguise
3, Tampering risk: The integrity of the message cannot be proven, so it may have been tampered
HTTPS
You can see HTTPS websites, and a lock mark will appear in the address bar of the browser.
HTTPS is not a new protocol for the application layer. Usually HTTP communicates directly with TCP, while HTTPS first communicates with the security layer (SSL/TLS), and then the security layer communicates with the TCP layer.

The SSL/TLS protocol was born to solve the problems of HTTP mentioned above. Let’s take a look at how it is solved. :
1. All information is encrypted and transmitted, and third parties cannot eavesdrop.
2. Equipped with identity verification to prevent identity impersonation
3. Has a verification mechanism , once tampered with, both communicating parties will immediately discover it
Encryption
##Symmetric encryption
Encryption The method of using the same secret key for decryption is called shared key encryption, also called symmetric key encryption.
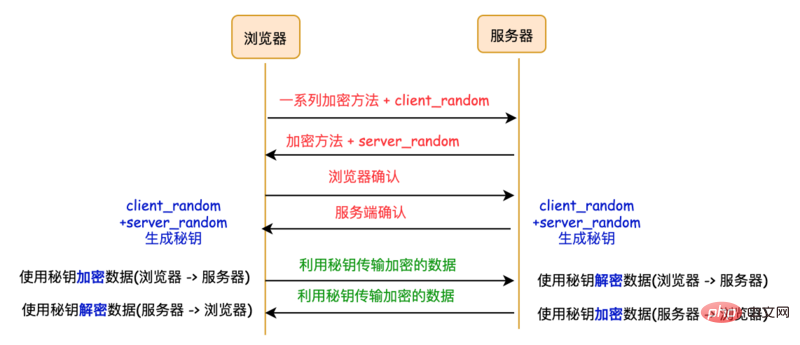
- The browser sends to the server
client_random
and a series of encryption methods - The server sends it to the browser
server_random
and encryption method##The existing browser and server have three identical credentials:
, server_random and encryption methodUse the encryption method to mix the two random numbers client_random
and server_random to generate a secret key. This key is the password for communication between the browser and the server. Existing problems: The third party can obtain
, server_random and the encryption method in the middle. Since this encryption method can be decrypted at the same time, the middleman can successfully decipher the password. By decrypting and obtaining the data, it is easy to crack this encryption method.
- The server sends the encryption method and public key to the browser
- The browser then encrypts the data and transmits it to the server through the public key, and the server receives the data Decrypt using private key. When the server sends data to the browser, it uses the private key to encrypt it. The browser receives the data sent from the server and uses the public key to decrypt it.
- The efficiency of asymmetric encryption is too low
- , which will seriously affect the speed of encryption and decryption, and then affect the user's ability to open the page speed.
- . The server's data can only be encrypted with the private key (because if it uses the public key, the browser cannot It cannot be decrypted). Once the middleman gets the public key, he can decrypt the data sent from the server, and it is cracked again.
The data transmission phase still uses symmetric encryption, but we use non-symmetric encryption keys. Symmetrically encrypted transmission.
- The server receives it and returns server_random, encryption method and public key.
- The browser receives it, then generates another random number pre_master, encrypts it with the public key, and transmits it to the server. (Key operation!)
- The server uses the private key to decrypt the encrypted pre_master.
So far, the server and browser have the same client_random, server_random and pre_master, and then the server and browser The server will use these three sets of random numbers to generate a symmetric secret key. With the symmetric secret key, both parties can use symmetric encryption to transmit data.
CA (digital certificate)
uses a symmetric and asymmetric hybrid method to achieve encrypted transmission of data. But there is still a problem, the server may be impersonated by hackers. In this way, the browser accesses the hacker's server, and the hacker can implement the public key and private key on his own server. However, the browser does not fully know that the hacker's site is being visited.
The server needs to prove its identity and needs to use a certificate issued by an authoritative organization. This authoritative organization is the CA (Certificate Authority). The issued certificate is called a digital certificate (Digital Certificate).
For the browser, the digital certificate has two functions:
Prove the identity of the server to the browser through the digital certificate
-
The digital certificate contains the server public key
Let’s take a look at the HTTPS request process containing the digital certificate
Compared to the HTTPS request process without digital certificates, the following two main changes have been made
The server does not directly return the public key to the browser, but returns the number Certificate, and the public key is included in the digital certificate;
There is an additional certificate verification operation on the browser side. After the certificate is verified, the subsequent process continues.
Reference
How to explain asymmetry in easy-to-understand terms Encryption?
(1.6w words) The soul of the browser Ask, how many can you pick up?
Recommended tutorial: Web server security
The above is the detailed content of How does HTTPS ensure security? (detailed explanation). For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to use Nginx Proxy Manager to implement reverse proxy under HTTPS protocol
Sep 26, 2023 am 08:40 AM
How to use Nginx Proxy Manager to implement reverse proxy under HTTPS protocol
Sep 26, 2023 am 08:40 AM
How to use NginxProxyManager to implement reverse proxy under HTTPS protocol. In recent years, with the popularity of the Internet and the diversification of application scenarios, the access methods of websites and applications have become more and more complex. In order to improve website access efficiency and security, many websites have begun to use reverse proxies to handle user requests. The reverse proxy for the HTTPS protocol plays an important role in protecting user privacy and ensuring communication security. This article will introduce how to use NginxProxy
 How to use Nginx Proxy Manager to implement automatic jump from HTTP to HTTPS
Sep 26, 2023 am 11:19 AM
How to use Nginx Proxy Manager to implement automatic jump from HTTP to HTTPS
Sep 26, 2023 am 11:19 AM
How to use NginxProxyManager to implement automatic jump from HTTP to HTTPS. With the development of the Internet, more and more websites are beginning to use the HTTPS protocol to encrypt data transmission to improve data security and user privacy protection. Since the HTTPS protocol requires the support of an SSL certificate, certain technical support is required when deploying the HTTPS protocol. Nginx is a powerful and commonly used HTTP server and reverse proxy server, and NginxProxy
 Nginx with SSL: Configure HTTPS to protect your web server
Jun 09, 2023 pm 09:24 PM
Nginx with SSL: Configure HTTPS to protect your web server
Jun 09, 2023 pm 09:24 PM
Nginx is a high-performance web server software and a powerful reverse proxy server and load balancer. With the rapid development of the Internet, more and more websites are beginning to use the SSL protocol to protect sensitive user data, and Nginx also provides powerful SSL support, making the security performance of the web server even further. This article will introduce how to configure Nginx to support the SSL protocol and protect the security performance of the web server. What is SSL protocol? SSL (SecureSocket
 What does the https workflow look like?
Apr 07, 2024 am 09:27 AM
What does the https workflow look like?
Apr 07, 2024 am 09:27 AM
The https workflow includes steps such as client-initiated request, server response, SSL/TLS handshake, data transmission, and client-side rendering. Through these steps, the security and integrity of data during transmission can be ensured.
 How to configure https in tomcat
Jan 05, 2024 pm 05:15 PM
How to configure https in tomcat
Jan 05, 2024 pm 05:15 PM
Configuration steps: 1. Obtain the SSL certificate; 2. Configure the SSL certificate; 3. Edit the Tomcat configuration file; 4. Restart Tomcat. Detailed introduction: 1. You need to obtain an SSL certificate, either a self-signed certificate or a valid SSL certificate from a certification agency (such as Let's Encrypt); 2. Place the obtained SSL certificate and private key files on the server and ensure that these files Located in a safe location, only users with sufficient permissions can access; 3. Edit Tomcat configuration files, etc.
 Solution: urllib3 ProxySchemeUnknown(proxy.scheme)
Feb 29, 2024 pm 07:01 PM
Solution: urllib3 ProxySchemeUnknown(proxy.scheme)
Feb 29, 2024 pm 07:01 PM
The reason for the error is that the ProxySchemeUnknown(proxy.scheme) error of urllib3 is usually caused by the use of an unsupported proxy protocol. In this case, urllib3 does not recognize the proxy server's protocol type and therefore cannot use the proxy for network connections. To resolve this issue, you need to ensure that you are using a supported proxy protocol, such as HTTP or https. How to resolve To resolve this issue, you need to ensure that you are using a supported proxy protocol, such as HTTP or HTTPS. You can solve this problem by setting the proxy parameters of urllib3. If you are using an http proxy, the code example is as follows: importurllib3http
 Using HTTPS for data transmission in Java API development
Jun 18, 2023 pm 10:43 PM
Using HTTPS for data transmission in Java API development
Jun 18, 2023 pm 10:43 PM
With the development of science and technology, network communication has become one of the important tools for information transmission in modern society. But at the same time, information transmission on the network faces the risk of malicious attacks and theft, so security is particularly important. Based on this, the HTTPS protocol came into being. It is a protocol that adds SSL/TLS encryption to the HTTP protocol to ensure network transmission security. As a language widely used in network development, Java naturally provides a rich API to support the HTTPS protocol. This article will
 How Nginx firewall ensures HTTPS secure communication
Jun 10, 2023 am 10:16 AM
How Nginx firewall ensures HTTPS secure communication
Jun 10, 2023 am 10:16 AM
In today's Internet era, secure communication has become an indispensable part. Especially in HTTPS communication, how to ensure its security is particularly important. As a popular web server and reverse proxy server, Nginx's firewall can also play an important role in ensuring HTTPS secure communication. This article will discuss the Nginx firewall from the following aspects. TLS/SSL encryption The security of HTTPS communication is mainly based on TLS/SSL encryption technology, which can prevent data from being transmitted during transmission.




)
)
)


