Is closing the registry an effective worm prevention strategy?
Close the registry is not an effective strategy for worm prevention. Security measures to prevent worm viruses: 1. Turn on personal firewall; 2. Check the accounts used by the machine, delete unnecessary accounts, and use complex passwords for necessary accounts; 3. Update security patches to prevent vulnerability-based attacks ; 4. Regularly check whether there are suspicious items in services, processes, and registries.

The spread process of worm virus is as follows:
Step one: Scan. The scanning process is to use a scanner to scan the host and detect the host's operating system type, version, host name, user name, open ports, open server software version, etc.
Step 2: Attack. The attack process is generally divided into two types. One is an attack that exploits vulnerabilities. If the operating system information or information about certain software returned by the scan is a vulnerable version, you can directly use the attack code for the vulnerability to obtain the corresponding permissions. Another type of attack is based on file sharing and weak keys. This attack requires trying to guess the user's password based on the collected information. Generally, worms have mechanisms such as testing empty passwords, simple passwords, and whether the password is the same as a known password. After guessing the correct password, you will have control over the remote host.
Step 3: Copy. Copying is actually a file transfer process, which uses file transfer protocols and ports for network transmission.
In order to prevent your computer from being attacked by LAN worms and infected with such viruses, it is recommended that users take the following basic security measures:
1. Turn on the personal firewall: According to Application conditions and for certain types of viruses, if you set some protection rules for protocols, ports, programs, intrusion detection, etc., the protection effect will be better;
2. Try to close unnecessary file sharing. In addition to shared files set by users, Windows operating systems generally have default shares such as C$, D$, ADMIN$, IPC$, etc. If these share attributes are removed, virus files cannot be copied locally;
3. Enforce password policies. Check the accounts used by this machine and delete unnecessary accounts. Use complex passwords for necessary accounts;
4. Apply all security patches to the operating system in a timely manner to prevent vulnerability-based attacks;
5. Regularly check services, processes, and registry entries If there are any suspicious items, promptly close or delete unnecessary services or startup items.
For more related knowledge, please visit: PHP Chinese website!
The above is the detailed content of Is closing the registry an effective worm prevention strategy?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
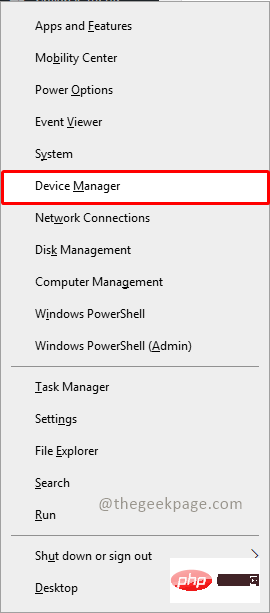 Unable to remove Xbox wireless controller, removal failure fix
Apr 14, 2023 am 10:40 AM
Unable to remove Xbox wireless controller, removal failure fix
Apr 14, 2023 am 10:40 AM
The Xbox app allows its users to play exciting games on their PC in case the console is not there. Users can connect their Xbox controller directly to the PC and start playing on their Windows PC. Sometimes the Xbox Wireless Controller cannot be removed from a user's Windows 11/Windows 10 laptop. There are a number of issues, the most prominent of which is users encountering "removal failed" issues when trying to remove gadgets. If you get a "Removal failed" error when removing your Xbox Wireless Controller, restart your computer. The most straightforward solution to common problems is to restart your Windows device. If you are restarting your computer
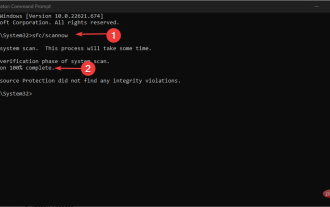 0xC004d302: How to fix this activation error
Apr 14, 2023 pm 02:49 PM
0xC004d302: How to fix this activation error
Apr 14, 2023 pm 02:49 PM
Some of our readers have recently reported that they received one of the Windows activation errors, such as the 0xC004D302 error code on their Windows PC, due to which certain features stopped working. This error occurs on computers running non-core versions of Microsoft Windows. It can be triggered when the trusted data store is reactivated. You can solve this problem by following this article. What causes the 0xc004d302 error in this article? Here are some potential reasons behind the 0xC004d302 Windows Activation Error Code: Fake or Incorrect Product Key – One of the most common reasons why you receive the 0xC004d302 error code is when you enter
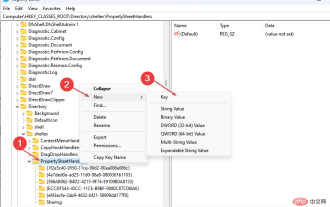 No location tab in properties: how to enable it
Apr 13, 2023 pm 11:16 PM
No location tab in properties: how to enable it
Apr 13, 2023 pm 11:16 PM
Folder properties provide users with details such as creation date, folder name, size, etc. However, sometimes you may come across the Location tab in the properties of a Windows folder. So, we'll walk you through the steps to troubleshoot and re-enable it. Alternatively, you can check out our detailed guide on fixing folder access denied issue on Windows 11. Why can't I find the Location tab in the folder properties? There are several factors that can cause the Location tab to be missing in folder properties on Windows 11. Most notably: Folders don’t support moving – some folders support moving to another location, while others don’t. By default, moving from one location to another is supported
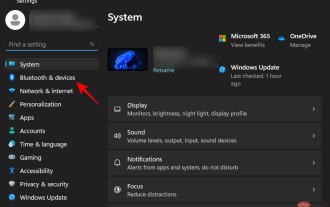 Remove a printer on Windows 11: 6 methods and 7 fix instructions
Apr 17, 2023 am 09:37 AM
Remove a printer on Windows 11: 6 methods and 7 fix instructions
Apr 17, 2023 am 09:37 AM
Removing a Printer on Windows 11 Completely removing a printer requires two things - removing the printer itself, and then removing the driver. There are several ways you can perform these operations on Windows 11. They are: Method 1: From Settings Perhaps the most common method, a printer can be easily removed from the Windows Settings application. Here's how to do it: Press Win+I to open Settings. Then click Bluetooth & Devices in the left pane. On the right, click Printers & Scanners. Click the printer you want to uninstall. Select Delete. When prompted, click Yes. Method 2: Use Device Manager to Remove Printer Drivers Device Manager lets you manage and remove Windows
 How to solve the problem of location services being grayed out in Windows 10/11?
Apr 26, 2023 pm 03:49 PM
How to solve the problem of location services being grayed out in Windows 10/11?
Apr 26, 2023 pm 03:49 PM
Location services are an important feature for some applications on Windows, depending on the location of your system. So if you see the Location Services option grayed out on your system, you can't even toggle it manually. Usually, some system glitch causes this issue and you can easily fix it by following these simple solutions. Fix 1 – Adjust the registry You can adjust the registry to fix this greyed out location services issue. 1. Press the Win key and type "Registry". 2. Then, click "Registry Editor" to open the Registry Editor on your system. 3. You will delete a specific registry subdirectory. Usually, it won't affect your system at all. However, it is recommended that you perform a system backup. one. After opening the Registry Editor, click
 How to disable core parking on Windows 10
May 16, 2023 pm 01:07 PM
How to disable core parking on Windows 10
May 16, 2023 pm 01:07 PM
If you are a Windows user and want to disable the core parking functionality in your system, this article will guide you through the process. What is core parking? The core parking function is a power saving mechanism. It puts some of your processors into a sleep mode that doesn't perform any tasks and consumes very little or no power. This helps reduce energy consumption and therefore heat in the system. These cores are unparked when needed. Few users need to disable this feature, especially gamers. Disabling this feature will improve your system performance. Disable Windows Core Parking using Windows Registry Editor Step 1: Use Windows + R keys simultaneously to open the run prompt. Step 2: At the run prompt
 Fix: WD My Cloud doesn't show up on the network in Windows 11
Oct 02, 2023 pm 11:21 PM
Fix: WD My Cloud doesn't show up on the network in Windows 11
Oct 02, 2023 pm 11:21 PM
If WDMyCloud is not showing up on the network in Windows 11, this can be a big problem, especially if you store backups or other important files in it. This can be a big problem for users who frequently need to access network storage, so in today's guide, we'll show you how to fix this problem permanently. Why doesn't WDMyCloud show up on Windows 11 network? Your MyCloud device, network adapter, or internet connection is not configured correctly. The SMB function is not installed on the computer. A temporary glitch in Winsock can sometimes cause this problem. What should I do if my cloud doesn't show up on the network? Before we start fixing the problem, you can perform some preliminary checks:
 How to add jump list items on Windows 10 and 11
May 11, 2023 pm 04:31 PM
How to add jump list items on Windows 10 and 11
May 11, 2023 pm 04:31 PM
Jump list on Windows provides easy access to recent files. If you want to add jump list items on Windows, this tutorial will help you get started. Jump Lists on Windows 10 and Windows 11 allow easy access to recently used files, folders, and websites. However, you may want to display more than the 10 most recent items that Windows displays by default. You can make Windows display more items in your jump list by adjusting the registry. For example, you can set it to display about 15-20 items, which will display well on most monitors. This tutorial will show you how to use Windows 10 and Windows 10



